With the Target data breach, many are wondering how criminals can profit from the use of the stolen credit cards. The card holders themselves will not be responsible for any of the charges, so how is it that criminals are able to make money from stolen credit cards?
I have been involved with several cases where organized crime rings have been unveiled, many of these have had connections to Russian and Eastern European groups. These groups generate a significant profit through stolen property acquired through burglaries, shoplifting, identity theft, credit card skimming and carding. Many underestimate the complexity of some of these networks and the revenue they generate.
The United States is a mecca for carders, simply because of the fact we are one of the last countries to rely on magnetic strip credit cards that are easily cloned and lack the security of newer chip and pin. The reason the U.S. is still using the technology from the 1960’s is a topic for another blog post altogether.
Buying Stolen Credit Cards Online
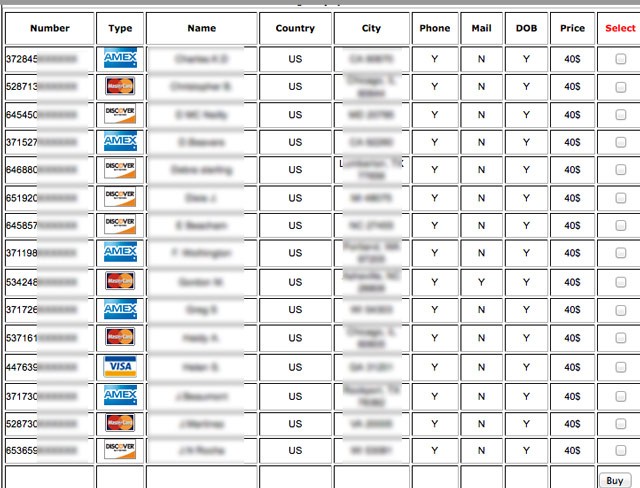
First the card numbers are sold to brokers who acquire the stolen card numbers in bulk. These are then sold to carders. The price for valid credit cards can be as high as $100 per card depending on the amount of information available with the card, type of card and known limits of the card. Many of these sites offer guarantees on the validity of the cards and will provide a valid replacement if it is blocked. Now that is customer service.
Valid stolen credit cards for sale on a website in the “deep web”
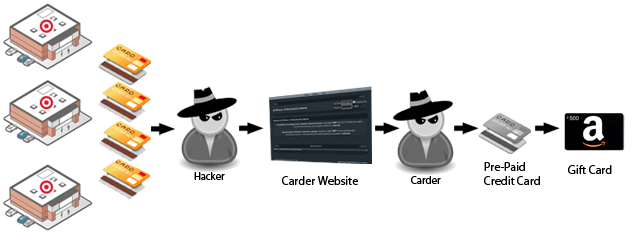
The Credit to Gift Card Shell Game – Find the Fraud!
One lucrative method of “carding” involves a shell game, where stolen credit cards are used to charge pre-paid cards. These cards are then used to purchase store specific gift cards, such as from Amazon for example.
Shopping & Reshipping
The carder then uses that gift card to purchase high value goods, usually electronics such as cell phones, computers and game consoles. This process makes it difficult for companies to trace. By the time it is figured out and the cards blocked the criminal is in possession of the purchased goods.
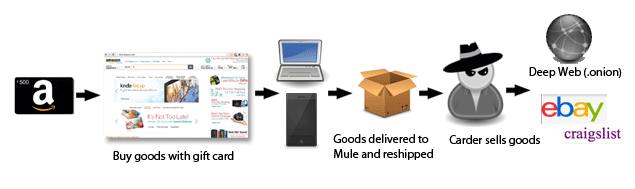
These packages are usually then shipped via a re-shipping scam. Unsuspecting individuals are recruited as Mules (re-shippers) usually through legitimate channels such as Craigslist job listings promising “easy work-from-home jobs” and usually in the United States as it raises fewer red flags.
The re-shipper then assembles multiple packages and ships them usually outside the country, or directly to someone who purchases the goods from an auction site the fraudster has posted the goods to.
Reselling Goods for Profit
The carder may then sell the electronics through legitimate channels such as through eBay, or to avoid risk can sell the goods through a hidden underground “deep web” site. Most people know the “deep web” from the Silk Road, which was recently shut down by the FBI, reappeared and then vanished again.
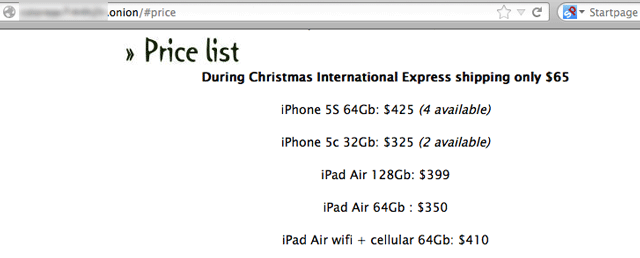
The Silk Road was a marketplace for illegal products such as drugs online. However the Silk Road had somewhat of a code of ethics, as certain products were restricted from sale such as pornography, weapons, personal data (stolen credit cards, passwords etc), poisons, or weapons.
There are many hidden services available that do not have such scruples. There are numerous places on the deep web that sell stolen credit cards and goods acquired through carding.
On these hidden illegal websites the goods are usually sold at deep discounts on the black market, usually around 50% of retail and reshipped or sent to a secure drop (vacant house etc) a purchaser has setup for this purpose.
Right now the entire carding underground is busy, as banks scramble to monitor fraudulent activity on the stolen Target cards, the carders need to stay a step ahead and move quickly. Much of the credit card charges have already been made and thieves have already cashed out.
This process of detecting fraud by the banks is furthered hampered simply because of the holiday season and the high volume of transactions that are occurring. It is going to be tough time for fraud analysts this holiday season.
Prevent Your Cloud from Getting Hacked
Read our guide "Six Security Controls to Prevent Your Cloud from Getting Hacked"


