What Makes Tripwire Enterprise Different?
Thousands of organizations trust Tripwire Enterprise to serve as the core of their cybersecurity programs. Here's why.
Unparalleled Visibility
Every breach begins with a single change. Tripwire Enterprise gives you total visibility into each and every unplanned change on your network. High value, low volume change alerts reduce digital noise, and integrations provide granular endpoint intelligence for threat detection and policy compliance. Quickly gather actionable information to prioritize threats and remediate vulnerabilities.
Compliance Enforcement
Passing audits doesn’t have to be arduous. Tripwire Enterprise automates compliance evidence for you, saving you time and budget on preparation with audit-ready reporting. It supports the industry’s broadest library of over 4,000 policy and platform combinations for regulations like PCI, SOX, FISMA, HIPAA, ISO and NERC.
Proven Leadership
When you’re under pressure to protect sensitive data in a rapidly-evolving threat landscape, Tripwire Enterprise is there to automate foundational security controls and guide you through risk remediation. Investigation and root cause features and comparisons quickly tell you what’s most important: what changed, how, when and by whom. See why Tripwire has been a trusted leader cybersecurity for over 25 years.
Tripwire Enterprise Features
REAL-TIME DETECTION
Shorten the time it takes to catch and limit damage from threats, anomalies, and suspicious changes. The longer an unauthorized change remains undetected on your systems, the more time cybercriminals have to find and exploit it.
Continuous monitoring enables you to identify and respond to suspicious changes, such as credential permission escalations, as soon as they occur. You shouldn’t have to wait for your next scan to find out if your security posture is compromised by an emerging threat like Log4J or Spring4Shell, and with Tripwire Enterprise, you’ll be alerted right away.
View Tripwire Enterprise Datasheet
DEEP SYSTEM VISIBILITY
Building on real-time change detection, Tripwire Enterprise also delivers unparalleled visibility with built-in intelligence to determine the impact of an unexpected change. Extensive visibility into suspicious changes and misconfigurations helps you understand your security posture in detail.
Monitor critical assets with business-relevant tags such as risk level and geographic location. Wield its customizable reporting capabilities to view security and risk trends over time to validate continuous optimization efforts.
View Tripwire Enterprise Datasheet
EXTENSIVE APP INTEGRATIONS
Close the gap between IT and security by integrating with both teams' existing toolsets. Tripwire Enterprise's REST APIs integrate into the workflows of your other business processes and tools like Splunk, ServiceNow, Active Directory, JIRA, Cherwell, and many others.
It can automatically reconcile detected changes against tickets and requests from your change management system. Integration with Active Directory or your preferred IDP minimizes administrative overhead and human error by auto-creating users, groups, and roles for efficient access management.
View Tripwire Enterprise Datasheet
AUTOMATED COMPLIANCE
Out-of-the-box platforms and policies enforce regulatory compliance standards such as PCI DSS, NERC CIP, and HIPAA, while simultaneously supporting best practice frameworks like the CIS Controls and MITRE ATT&CK framework. Always know exactly how aligned your systems are with regulatory policies and get audit-ready reporting to quickly prove compliance and streamline your next audit.
Tripwire Enterprise includes the industry’s largest library containing 4,000+ policy and platform combinations, as well as custom policy creation functionality.
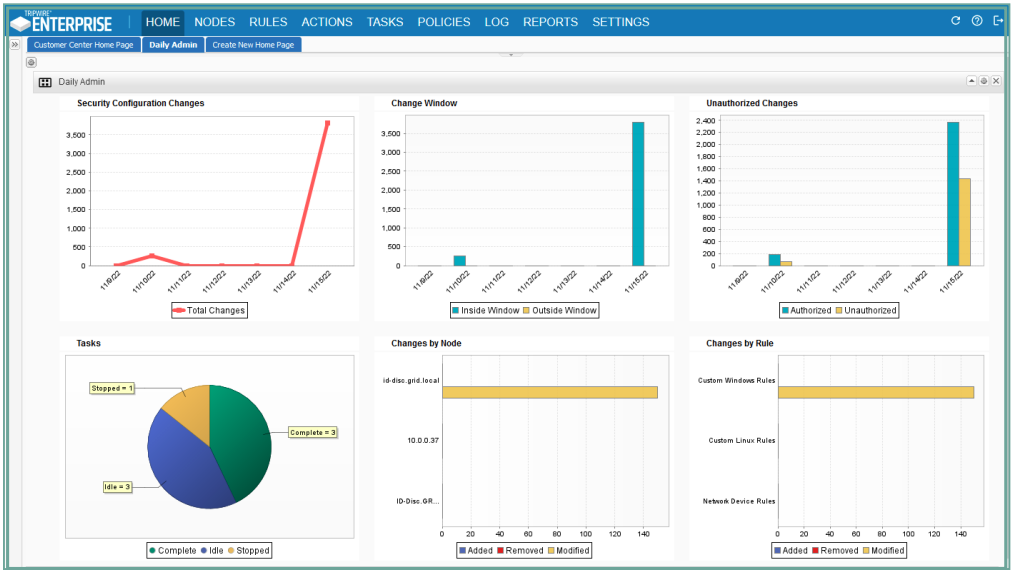
View Tripwire Enterprise Datasheet
Try a Self-Guided Tour of Tripwire Enterprise
Take a closer look at the features and functionality of the industry's leading FIM and SCM solution at your own page with a self-lead, interactive product tour.
How Does Tripwire Enterprise work?
Help Control Security Breaches With Integrity and Compliance Monitoring
Backed by decades of experience, Tripwire Enterprise is capable of advanced use cases unmatched by other solutions. Tripwire helps reduce your attack surface and risk exposure with proper system hardening and continuous configuration monitoring. See how Tripwire enables you to maintain a secure baseline configuration, monitor assets for deviations, while automating and guiding security teams for rapid repair of non-compliant systems and misconfigurations.
Request a Demo
See Tripwire Enterprise for yourself in a live, personalized demo. Simply complete this form and a Tripwire product specialist will reach out to schedule. We look forward to helping you achieve your cybersecurity and compliance goals.
Fill out the form to get a personalized demo of Tripwire Enterprise’s FIM and SCM capabilities.
The Tripwire name is trusted in the industry and has never given reason to doubt it. Continued development and listening to customers only strengthens this fact.
— IT Systems Analyst, Fortune 500 Energy & Utilities Company
See why Tripwire is trusted by thousands of customers worldwide