Vulnerability management solutions are only valuable when they help you prioritize your efforts effectively. Fortra’s Tripwire® IP360™ is an enterprise-class vulnerability management solution that enables cost-effective reduction of cyberthreat risk by focusing your remediation efforts on the highest risks and most critical assets.
The solution is built upon a scalable architecture that delivers risk-based vulnerability assessment with speed, reliability and accuracy, along with the industry’s most comprehensive vulnerability scoring and endpoint intelligence integration for quick response to new advanced threats.
Tripwire IP360 delivers:
- Comprehensive discovery and profiling of all network assets
- Highly-scalable architecture with low network and system impact
- Advanced vulnerability scoring and prioritization that identifies top risks
- Vulnerability data to asset information in Tripwire Enterprise so you can focus on the risks that matter
Find Everything on Your Network
Tripwire IP360 provides complete visibility into your network, both on-premises and in the cloud, including all devices and their associated operating systems, applications and vulnerabilities. The industry-leading Tripwire Vulnerability and Exposure Research Team (VERT) keeps Tripwire IP360 up-to-date with accurate, non-intrusive discovery signatures that are current and relevant to large organizations.
It discovers all networked hosts, applications and services to give you a comprehensive view of your network. Tripwire’s unique application-centric approach to vulnerability assessment searches for specific vulnerabilities based on operating system, applications and services. This ensures that only the required signatures are run, limiting negative application interactions.
It also supports multiple ways to discover and assess assets. Dynamically scalable vulnerability scans allow you to efficiently assess broad ranges of your network. For dynamic IP endpoints such as laptops and occasionally connected devices, agent-based vulnerability management can provide more accurate assessment of your assets. For cloud assets, Tripwire IP360 is available in the AWS and Azure marketplaces for pre-authorized scanning. And for organizations adopting DevOps, Tripwire IP360 can discover and assess both stopped and running containers.
Prioritize Intelligently
Tripwire IP360 discovers a wealth of data about the hosts on your network. Rather than providing a seemingly endless list of “high risk” vulnerabilities, Tripwire IP360 ranks vulnerabilities on a granular scale of 1–50,000, making it crystal clear where your risk lies and allowing you to focus on the mitigations that will most effectively reduce risk in your organization.
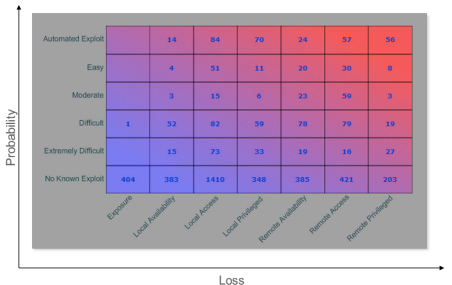
Tripwire VERT objectively analyzes each vulnerability to see how easy it is to exploit, along with what privileges an attacker will gain upon successful exploitation. This results in the risk matrix in Fig 1, which empowers teams to remediate the most critical items first. These two vectors are combined with the age of the vulnerability to provide a vulnerability risk score. This risk score allows security analysts to track risk mitigation across the enterprise, demonstrating the value of the vulnerability management program to executive sponsors.
Centralized Management
Tripwire IP360 provides an easy-to-use web interface for administration, configuration, reporting and workflow. Granular access controls and user roles enable it to conform to existing security processes.
Automation Through Integration
Tripwire IP360 is built on open standards that enable integration with existing business processes and IT systems like help desk, asset management, SIEM, intrusion detection/prevention, and other security solutions. The comprehensive endpoint intelligence it gathers enhances existing information management solutions and drives automation across your security ecosystem
Resilient Architecture
This easy-to-deploy, on-premises solution utilizes one or more hardened Linux-based virtual or physical appliances. Scanning appliances can be pooled for unprecedented speed and resiliency.