LinkShadow integrates with Tripwire solutions to complete the full cycle of behavioral analytics and threat hunting, providing the combined benefits of Tripwire’s file integrity monitoring (FIM) technology and proactive threat detection.
Next Generation Cybersecurity Analytics
LinkShadow® Cyber Security Analytics Platform is designed to manage threats in real time. It utilizes AI based machine learning to analyze events and perform UEBA. Cutting edge threat hunting provides state of the art cyber event anticipation
Integration Use Cases
Suspicious File Access & Tripwire Enterprise
Using the Tripwire® Enterprise/ LinkShadow integration, customers can receive the following benefits:
- Compliance audit reports showing how business compliance goals are or are not being met on individual systems, with details to correct
- Faster resolution and investigation by combining LinkShadow anomalies with data from Tripwire Enterprise: what changes were made, who made the them, and when.
- Prioritized criticality of a given change that enables more rapid response by combining LinkShadow anomalies with Tripwire Enterprise results.
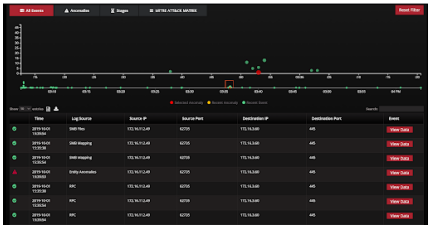
Tripwire Enterprise feeds LinkShadow with enriched detection of file events to hunt for any suspicious file access by anomalous users. With Shadow360 Dashboard, the analyst gains full visibility on all user activities before and after the suspicious file access behavior.
Anomalous File Tampering
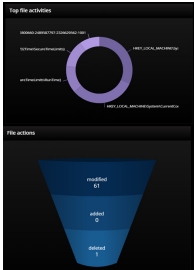
LinkShadow gains full visibility of file tampering activities on endpoints from Tripwire Enterprise. LinkShadow injects this intelligence into the machine learning algorithms to identify suspicious and anomalous activities based on the behavioral analysis. File tampering can indicate the early stages of an attack.
Suspicious File Access & Tripwire IP360
The Tripwire IP360™ and LinkShadow integration provides following benefits:
- Asset inventory list provided to LinkShadow
- Detailed software inventory on individual systems
- Vulnerabilities of the OS and the software installed on the system
- Accurate CVE records related to the vulnerability, including Tripwire risk score
- Prioritized systems by combining LinkShadow anomalies, Tripwire identified vulnerabilities, and the criticality of the systems