The National Cybersecurity Authority (NCA) is the government entity in charge of cybersecurity in Saudi Arabia, encompassing both regulatory and operational functions related to cybersecurity.
National Cybersecurity Authority Essential Cybersecurity Controls
The NCA works closely with public and private entities to improve the cybersecurity posture of the country in order to safeguard its vital interests, national security, critical infrastructures, high priority sectors, and government services and activities. The NCA’s Essential Cybersecurity Controls (ECC) take the cybersecurity needs of all organizations and sectors in the Kingdom of Saudi Arabia, meaning that every organization therein must comply.
According to NCA, it has developed the Essential Cybersecurity Controls “after conducting a comprehensive study of multiple national and international cybersecurity frameworks and standards, studying related national decisions, law and regulatory requirements, reviewing and leveraging cybersecurity best practices, analyzing previous cybersecurity incidents and attacks on government and other critical organizations, and surveying and considering opinions of multiple national organizations.”
Tripwire Enterprise and the Five Domains of the Essential Cybersecurity Controls
Tripwire® Enterprise is a security configuration management (SCM) suite that provides fully integrated solutions for policy, file integrity and remediation management. Organizations can use these solutions together for a complete end to end SCM solution, or use its file integrity monitoring (FIM) or policy management solutions on their own to address today’s pressing security and compliance challenges—while building a foundation that positions them to address tomorrow’s. Let’s take a look at the ways in which Tripwire Enterprise assists with NCA compliance.
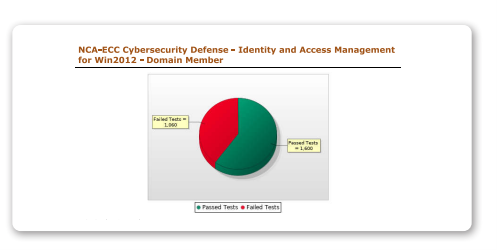
Identity and Access Management
According to the NCA, this policy is intended to ensure the secure and restricted logical access to information and technology assets in order to prevent unauthorized access and allow only authorized access for users which are necessary to accomplish assigned tasks. Tripwire Enterprise can scan against cybersecurity requirements for identity and access management that must be implemented on various operating systems. Networks Security Management This policy ensures the protection of organization’s network from cyber risks. Tripwire Enterprise can scan against cybersecurity requirements for network security management. Cryptography This policy is required to ensure the proper and efficient use of cryptography to protect information assets as per organizational policies and procedures, and related laws and regulations. Tripwire Enterprise enables you to scan against cybersecurity requirements for cryptography that must be implemented on your systems.
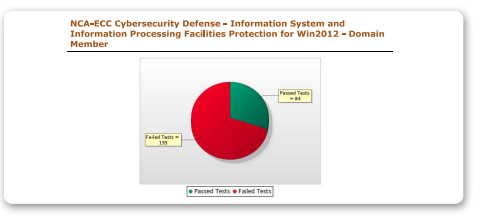
Information System and Information Processing Facilities Protection
This policy is required to ensure the protection of information systems and information processing facilities (including workstations and infrastructures) against cyber risks. Tripwire Enterprise can scan against cybersecurity requirements for protecting information systems and information processing facilities.
Networks Security Management
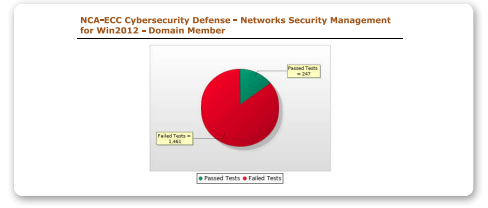
This policy ensures the protection of organization’s network from cyber risks. Tripwire Enterprise can scan against cybersecurity requirements for network security management.
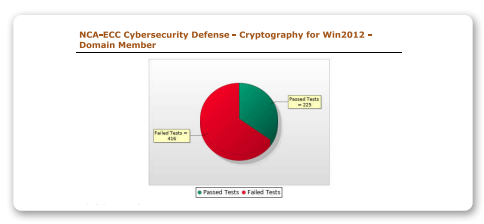
Cryptography
This policy is required to ensure the proper and efficient use of cryptography to protect information assets as per organizational policies and procedures, and related laws and regulations. Tripwire Enterprise enables you to scan against cybersecurity requirements for cryptography that must be implemented on your systems.
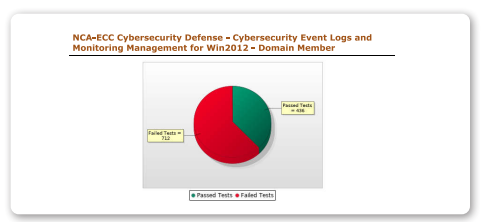
Cybersecurity Event Logs and Monitoring Management
It’s imperative to have the timely collection, analysis and monitoring of cybersecurity events for early detection of potential cyberattacks in order to prevent or minimize the negative impacts on your organization’s operations. Tripwire Enterprise can also scan against cybersecurity requirements for event logs and monitoring management.
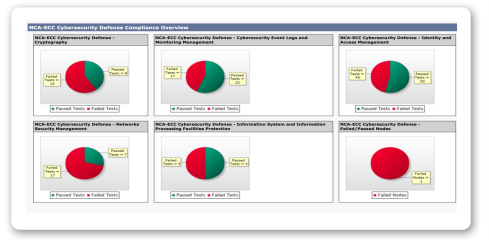
NCA-ECC Cybersecurity Defense Dashboard in Tripwire Enterprise
Tripwire Enterprise helps you achieve alignment with the NCA –ECC Cybersecurity Defense across your environment, allowing security, compliance and operations teams rapidly achieve a foundational level of security across your entire enterprise, including on premise, cloud and industrial assets, by reducing the attack surface, increasing system integrity and delivering continuous compliance.
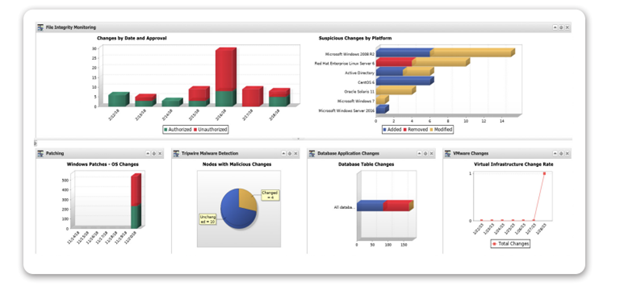
Tripwire has taken its original host-based intrusion detection tool, which could simply detect changes to files and folders, and expanded it into a robust file integrity monitoring (FIM) solution, able to monitor detailed system integrity: files, directories, registries, configuration parameters, DLLs, ports, services, protocols, etc. Additional enterprise integrations provide granular endpoint intelligence that supports threat detection and policy and audit compliance.