
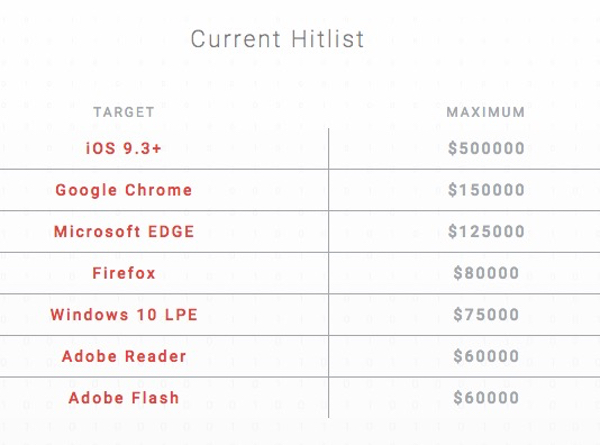
It's just a week since Apple announced its first-ever bug bounty for researchers who find vulnerabilities in its widely-used software and hardware, in the hope that it can provide better security and privacy to its millions of customers. The Cupertino-based company made headlines for its belated entry into the bug bounty marketplace, offering up to $200,000 to researchers who uncover the most serious iOS flaws. Although Apple has dragged itself late to the starting line compared to other high-profile tech firms like Google, Microsoft and Facebook, the news was welcomed - in particular because of recent attempts by law enforcement to "break" iPhone security to assist in their investigations. While many are sympathetic to the law enforcement agencies trying to gather evidence for criminal investigations, concerns have been raised that if Apple itself isn't properly informed of the security holes used to break iOS security, no patches will be made, and *all* iPhone users (criminal or otherwise) will be left at risk. It's at this point that exploit brokerage firm Exodus Intelligence enters the story. Exodus is offering $500,000 ($300,000 more than the maximum offered by Apple) to anyone who can sell them a zero-day exploit for iOS.
Exodus isn't doing this out of the goodness of their hearts, of course. They are a business. They are planning to sell details of any zero-day exploits they purchase from vulnerability researchers, and they're planning - one assumes - to make a profit. Which means that they believe there are people prepared to pay more than $500,000 for a zero-day exploit for iOS. And remember this - what use is a zero-day exploit if Apple releases a security update that fixes it? At that point it becomes worth practically nothing. No, to convince a customer that the zero-day exploit you are selling them is worth half a million dollars you need to assure them that you are not going to also share details with the one organisation capable of plugging the security hole - Apple. The very real danger is that vulnerability researchers might be tempted to sell their exploit discoveries to third-parties rather than Apple directly because of the larger pot of money available. And there is a risk that as a result vulnerabilities will not get fixed by Apple, and might therefore be exploited by abusive governments, intelligence agencies and common criminals to spy upon innocent people. Security flaws do need to get fixed. And vulnerability researchers do deserve to be rewarded for their expertise and hard work. But it's hard to understand how a free market for iOS zero day exploits is going to ensure that the majority of us will be left safer online. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

