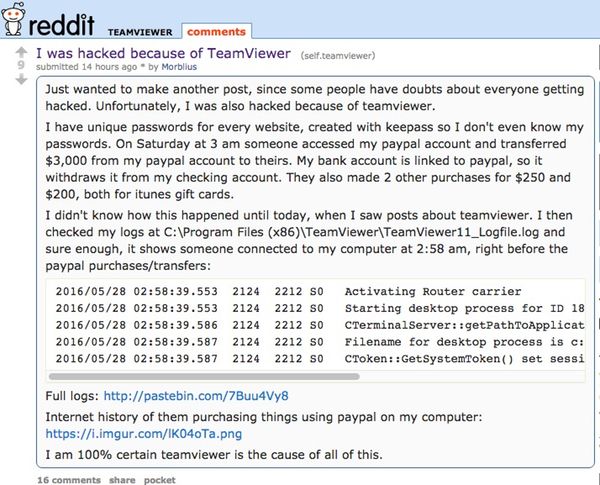
In the last day or two, there have been a spate of posts by TeamViewer users claiming that their computers have been hijacked by malicious hackers, their PayPal and other banking accounts emptied, their webmail accessed, and malicious software installed. And the victims seem to believe the attacks are linked to their use of TeamViewer.
Hold on a minute. What's TeamViewer? It's a piece of software popularly used for remote desktop access. In other words, if you have a problem with your computer, an IT guy can use TeamViewer to remotely access your computer from anywhere else in the world. With TeamViewer, someone can't just see what's on your computer screen. They can also take control of your mouse and keyboard. It's as though they're sitting right in front of your computer. And it's not just your computer. TeamViewer has remote-control clients for iOS and Android, as well as Windows, OS X, Linux, and Chrome OS. Sounds neat! If a hacker isn't able to exploit it... Yes, it's a very handy tool for doing remote technical support, or simply if you wish to access your home computer when you're traveling. But if your TeamViewer account isn't properly secured, you potentially have a big problem. So, has TeamViewer been hacked? TeamViewer has issued a statement, denying it has been hacked and putting the blame for any account breaches on user carelessness:
"There is no evidence to suggest that TeamViewer has been hacked. Neither do we have any information that would suggest that there is a security hole in TeamViewer."
(TeamViewer's statement is dated 23 May 2016, though it refers to concerns that have bubbled up into the press this week.) What kind of user carelessness does TeamViewer feel led to these account breaches? In short, TeamViewer appears to be pointing the finger at people re-using passwords:
"Unfortunately, users are still using the same password across multiple user accounts with various suppliers. While many suppliers have proper security means in place, others are vulnerable. The latter ones tend to be targeted by professional data thieves. As TeamViewer is a widely spread software, many online criminals attempt to log in with the data gained from compromised accounts (obtained via the aforementioned vulnerable sources), in order to discover whether there is a corresponding TeamViewer account with the same credentials."
That sounds sensible. Password reuse is a big problem. Right. We're all aware of data from mega-breaches at LinkedIn, Tumblr and MySpace being put up for sale on the dark web. And normally TeamViewer's explanation of what has happened would sound reasonable. But a number of the people reporting that their computers have been hijacked are adamant they weren't reusing passwords and that their credentials were rightly hard-to-crack as well as impossible to guess.
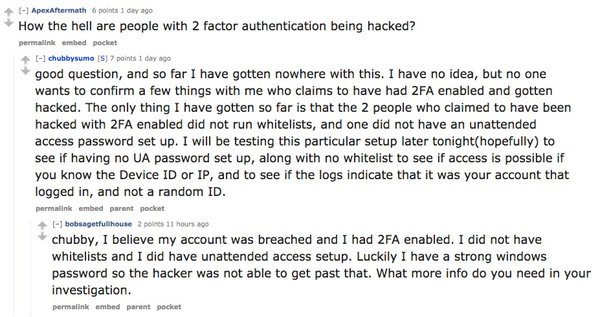
Furthermore, some of those who have had their TeamViewer accounts compromised say that they had even taken the step of enabling two-factor authentication, meaning that a hacker shouldn't be able to break in with just a username and password alone.

So, if people hadn't reused their passwords and had enabled 2FA on TeamViewer, how were their accounts hacked and their computers hijacked? We don't know. Some think TeamViewer is suffering from a security flaw that has managed to go under the radar of its team. But at this time, all of that is speculation. Frankly, not knowing what is really going on is leaving some deeply concerned. It's always better to know what you're up against. Yuck! So what should I do if I'm a TeamViewer user? If you're using TeamViewer, then ensure that you have configured its settings to maximize security. That means ensuring you have enabled two-factor authentication and restricted who can remotely access your computer (by setting up an access control whitelist, and other options). It should go without saying that it may make sense to review your password, ensuring that it is unique and strong, and that you keep your anti-virus defenses updated just in case spyware is stealing credentials as you type them into your computer. But don't stop there. If TeamViewer has been compromised in some fashion, then the attackers are using it as a springboard to attack your other online accounts. So ensure that you have properly hardened your bank accounts, PayPal, Amazon, eBay, and the like with strong, unique passwords along with their respective equivalents to two-factor authentication (sometimes delivered as two-step verification.) At the very simplest level, remember that a hacker can only use TeamViewer to remotely access your computer if you are running TeamViewer! It may make sense to quit the software when you don't need it or when you're not sat at your computer to see what's going on. More best practices for TeamViewer security are discussed in this Reddit thread. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

