
It was revealed this evening that Hillary Clinton was using a personal email account while serving as the secretary of state. This has raised a number of issues with regards to both compliance and security. Apparently, Clinton chose not to use a government-issued email address despite the Federal Records Act, which only applies to official email accounts created by the government, and are automatically retained. Furthermore, Clinton allegedly used a private email account under a personally registered domain, which circumvents the automated retention of communications, even while these communications were part of official government business. For the entire four-year tenure, Mrs. Clinton did not have a government email address while at the State Department. Her staff did not make backups of her personal email account or ensured there were archives made available as per the Federal Records Act. What I also find hard to believe is that nobody else within the government would have stopped to ask. Not only would such an activity circumvent record retainment requirements but also security requirements. For someone as high up as Hillary Clinton to be using a private email address for official government business, it raises a number of security concerns. This is shadow IT at a grand scale. With no visibility into how the Clinton's emails were being secured, it would be impossible for the government to ensure the communications were not compromised by espionage. According to the Washington Post, the worst scenario may have come true when hacker "Guccifer" reportedly released several emails pertaining to Benghazi, which appear to be between Sidney Blumenthal and Hillary Clinton at the "clintonemail.com" domain. The domain was registered January 2009 through Network Solutions.

Looking a bit deeper at the MX records for the domain they map to a service run by McAfee:
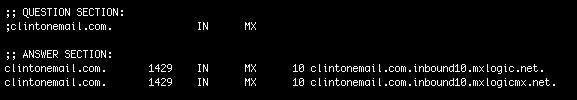
MX Logic was acquired by McAfee in June of 2009 and is now part of McAfee's SaaS offerings. So, it looks like someone knew what they were doing at some level to modify the MX records to use McAfee's service. However, the risk of this email account being compromised is significant and one wonders who else aside from Guccifer may have had access to sensitive communications. Before we pick on Hillary Clinton too much, we should evaluate how common this practice is. If the goal is to circumvent a regulatory requirement and is putting communications at risk, these shadow IT practices should be evaluated government-wide.

