
Within the HIPAA Security Rule are Administrative, Physical, and Technical Safeguards. These safeguards are as important to understand as they are to implement, so let’s get some clarifications for the non-initiated. Many healthcare entities and their business associates are routinely challenged with understanding and successfully implementing the technical safeguards defined by the HIPAA Security Rule. It’s been decades since HIPAA was signed into law and over a decade since the HITECH update, and since that time, healthcare facility operations have evolved to rely on software and technology to a much greater degree. Larger, faster networks, more complex software, and more instances of software inside a healthcare facility’s network seem to be the norm. As a result, healthcare IT departments have had to become smarter, and their practices have had to evolve. According to a report published in late 2020, most of the healthcare entities and business associates the Office for Civil Rights (OCR) reviewed during Phase Two Audits were not compliant. The Phase Two Audits are designed to assess whether covered entities and their business associates are complying with the HIPAA Privacy, Security and Breach Notification Rule. The U.S. Department of Health & Human Services (HHS) provides guidance on the three aforementioned areas of the rule in addition to case examples and their reports to Congress on their investigation results. HHS updated HIPAA and HITECH in 2013 when they finalized the Omnibus Rule. This rule contains edits and updates to all the previously passed rules. It is a single, exhaustive document that details all the requirements complying with HIPAA and HITECH. Consequently, business associates of healthcare entities are directly liable for any non-compliance and any fines associated with the non-compliance. Attackers are keenly aware that many healthcare organizations struggle in understanding their risks and how to mitigate them, and they’re taking full advantage. In the first half of 2021 there were 360 breaches reported to OCR, outpacing the same period for all previous years. Those 360 breaches exposed data on nearly 23 million patients. Last year, organizations reported 270 breaches of 8 million patients’ data in the first six months of the year; in 2019, around 230 breaches that exposed data on 11.2 million patients.
Let those numbers be our wakeup call. This is a fast-moving train!
More than any other time in our history, remote access to all data, not just personal health information (PHI), is at an all-time high. Health IT professionals must take care to ensure that the way their software and systems is accessed for remote support is HIPAA compliant. As every competent healthcare IT professional knows, policies, procedures, and access methods that were adequate before may be no longer acceptable today. The latest iteration of the HIPAA Security Rule defines four areas for its Technical Safeguards:
- Access Control – The implementation of technical policies and procedures for electronic information systems that maintain electronic protected health information (ePHI) to allow access only to those persons or software programs that have been granted access rights.
- Audit Controls – The implementation of the hardware, software, and/or, procedural mechanisms that record and examine activity in information systems which contain or use ePHI.
- Person or Entity Authentication – The implementation of procedures to verify that a person or entity seeking access to ePHI is the one claimed.
- Transmission Security – The implementation of technology to guard against unauthorized access to ePHI that is being transmitted over an electronic communications network.
Access Control
The Access Control safeguard ensures there is no unauthorized access of devices by a person other than an authorized, specifically known user. This is accomplished through unique usernames, passwords, and auto-logoff features. There should also be an Emergency Access Procedure to assure access to ePHI can be accomplished in the event of an emergency. Additionally, you should implement a system that encrypts messages when sending outside of your network and decrypt t messages coming into the organization. All ePHI must meet the standards set by the National Institute of Standards and Technology, regardless of whether the information is at rest or in transit.
Audit Control
Creating an audit trail is part of any sound security policy. Accordingly, a health IT professional will want to create, store, and protect appropriate log files of all security sensitive actives that take place during all access sessions. The Audit Control safeguard requires the entity be able to produce an audit trail across hardware, software, and/or all procedural mechanisms. Additionally, if a patient asks, “who has seen my health information,” the organization should be prepared to respond to such patient accounting requests. Furthermore, HIPAA requires a covered entity “to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports.”
Person or Entity Authentication
The Person or Entity Authentication standard requires a covered entity to verify people (or entities) seeking access to ePHI are who they say they are in any electronic communication. It is fundamental that healthcare IT professionals know who is accessing their network, software, and systems and that person gaining access is the one who is authorized. Many hospitals allow vendors to access their systems via shared IDs. This is a direct violation of HIPPA and HITECH as they require the use of unique user IDs. This can be quickly rectified by using tokens, smart cards or keys, password/PINS, or biometrics. There are pros and cons of each authentication method, and it is the responsibility of IT Security personnel to determine which methodologies to implement across their organizations. In many cases, one single methodology may not suffice so multiple levels of authentication will be the solution.
Transmission Security
The intention and spirit of these guidelines is to protect data during transmission. To assure this happens, all data transmission points must be known, and mechanisms must be used to provide encryption in transit and integrity verification. (“HIPAA Compliance 164.312(e)(1) - Transmission Security”) The ePHI must be protected from being altered without detection. Encryption is the primary method of achieving this safeguard for data in motion or at rest. This rule is technology neutral, so no specific information is documented regarding encryption strength. The Breach Notification Interim Final Rule provides additional guidance specifying technologies that render protected health information unusable, unreadable, and indecipherable to unauthorized individuals.
Play by the rules or else!
Since 2006, OCR also has had the responsibility to enforce the law when violations occur and plays multiple roles in its enforcement duties. It investigates complaints, conducts compliance reviews, and provides education to the entities on compliance. It also has the authority to levy penalties against non-compliant parties and can refer them to the Department of Justice if needed. Here’s the HIPAA violations break down in order of severity and the potential monetary impact:
- Category 1 (C1): A violation that the covered entity wasn’t aware of and likely couldn’t have avoided. The entity clearly tried to comply with HIPAA. $100 - $50,000 per violation.
- Category 2 (C2): A violation that the covered entity was expected to know but still could not have avoided. This category doesn’t yet constitute willful neglect. $1,000 - $50,000 per violation.
- Category 3 (C3): A violation due to willful neglect of HIPAA Rules. To fit into this category, the entity must have tried to correct its mistakes. $10,000 - $50,000 per violation,
- Category 4 (C4): A violation due to willful neglect of HIPAA Rules in which the entity was aware of its errors and did not try to correct them. At least $50,000 per violation
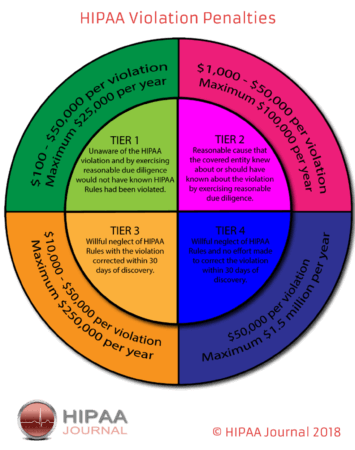
The above penalties fall under the civil violations umbrella of HIPPA. There are also annual maximums for repeat violations ranging from $25,000 to $1.5 million. Yearly maximums are unique to the tier of the violation. Recently, the HIPAA Journal provided updates to actual fines recently levied for HIPAA violations. In addition to civil penalties, criminal penalties can be imposed and are referred to the Department of Justice (DOJ). Just as civil penalties, there are different levels of severity:
- Tier 1: Deliberately obtaining and/or disclosing PHI without authorization. Up to one year in jail and a $50,000 fine.
- Tier 2: Obtaining PHI under false pretenses. Up to five years in jail and a $100,000 fine.
- Tier 3: Obtaining PHI for personal gain or malicious intent. Up to 10 years in jail and a $250,000 fine.
Where do IT Security professionals go from here?
HIPAA compliance is not a simple undertaking. Even the most well-meaning healthcare providers and their business associates can inadvertently go astray when trying to maintain privacy and confidentiality of their patients’ data plus providing the proper access and having the appropriate levels of encryption. All entities and vendors associated with healthcare organizations must have appropriate business level agreements in place, so everyone involved understands there are administrative, physical, and technical safeguards and requirements to keep our ePHI protected. Just to be clear, there are four important aspects of HIPAA compliance – the HIPAA Enforcement Rule, HIPAA Privacy Rule, HIPAA Security Rule, and HIPAA Breach Notification Rule, we’ve only summarized the Security Rule, but adherence to all four rules is critical for HIPAA Compliance. 2021 was a clear indication that our healthcare industry is under attack. HHS, OCR, and a multitude of healthcare consultants, lawyers, and vendors, like Tripwire, provide reams of guidance to assure IT Security staff in healthcare organizations have all the knowledge and tools needed to meet HIPAA Compliance. Reach out to these organizations to get your questions answered and develop solid partnerships to assure your healthcare organization(s) is/are compliant. Stay healthy and keep our ePHI safe!
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

