
Imagine coming into the office one day, and finding that visitors to your website are not only seeing messages and images posted by hackers, but that the attackers are also posting screenshots of private emails sent to your company on Twitter. That's the scenario Lenovo faces today—although there is no evidence that the PC manufacturer's own servers have been breached. Boy, it can't be a good time to be working at Lenovo at the moment—what with the storm they created over the SSL-busting Superfish adware they preinstalled on some customers' computers, and the consequent almost-inevitable class-action law suit. So, how does a company's website change like this in the blink of an eye, without your website being actually hacked?
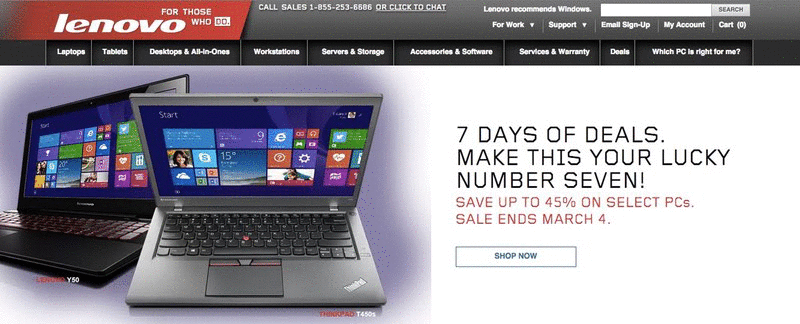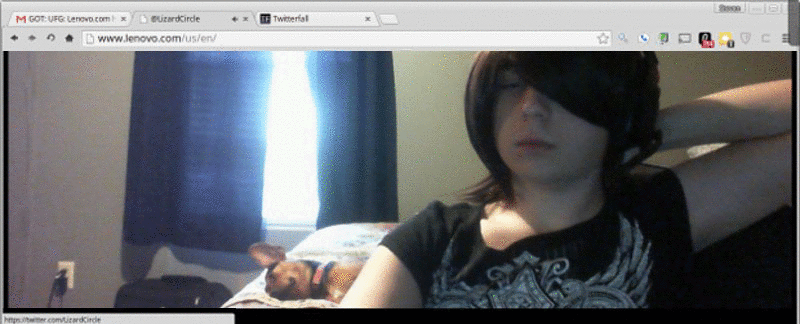
The thing is that your website doesn't have to be hacked to fall under the control of hackers. Instead, all the hackers need to do is hijack your site, and they can do that by meddling with your Domain Name System (DNS) records. DNS is the Internet's phone book, translating website URLs that people remember ("amazon.com", "google.com", etc.) into numeric IP addresses (72.21.215.232, 74.125.224.2, etc.) that the Internet understands. You can't remember your passwords—imagine having to remember the numeric address for all the websites you wanted to visit! As security blogger Brian Krebs reports that Lenovo's website was hijacked because Lizard Squad hackers were able to compromise Malaysian registrar Webnic.cc, that looks after the DNS entries Lenovo.com and some 600,000 other websites. By altering the DNS entries for Lenovo, the hackers were able to redirect web traffic trying to visit Lenovo.com to a web server under their control – which merrily displayed a slideshow of images, while playing a merry tune from "High School Musical" in the background. But more than that, the attackers also altered the MX records for Lenovo.com. Those are the settings that define the location of the mail server, which will accept email on behalf of a particular domain. In other words, the Lizard Squad hackers were now able to receive emails sent to Lenovo.com, which they were quite happy to tweet about.
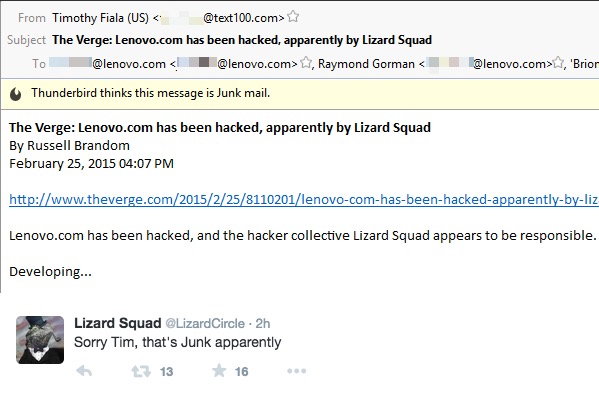
In the hours following the attack, Lenovo issued the following statement:
Unfortunately, Lenovo has been the victim of a cyber attack. One effect of this attack was to redirect traffic from the Lenovo website. We are also actively investigating other aspects. We are responding and have already restored certain functionality to our public facing website. We regret any inconvenience that our users may have if they are not able to access parts of our site at this time. We are actively reviewing our network security and will take appropriate steps to bolster our site and to protect the integrity of our users’ information and experience. We are also working proactively with 3rd parties to address this attack and we will provide additional information as it becomes available.
It's easy to pick on Lenovo at the moment, but no company should be fooled into thinking that they're not also potentially a target for a similar attack. Even Google found out to its cost earlier this week that it could be plagued by similar mischief-making, after Lizard Squad disrupted the Google Vietnam site via a similar hijack. DNS hijacking appears to be a growing threat, and is a technique not only used by the Lizard Squad hacking gang but also the Syrian Electronic Army and other online criminals. The damage that can be done to a corporate brand through hackers hijacking your website's DNS records are considerable, and many customers may assume that your own computers have been hacked. Companies which wish to protect their websites, and indeed any emails that are being sent to them, need to ask their domain name registrar what steps they are taking to protect against such attacks. For instance, the introduction of two-factor authentication and domain locking can help prevent unauthorised changes to DNS records and may deter hackers. You can also ask registrars if they are implementing DNS Security Extensions (DNSSEC), which can increase a user's trust that they are visiting the site that they intended. Unfortunately, at the moment, many registrars are not providing DNSSEC, leaving it up to website owners to put their trust that registrars services don't have vulnerabilities, and that other security practices (strong passwords and two-factor authentication) will be enough to protect their records from meddling by hackers. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc. If you are interesting in contributing to The State of Security, contact us here.
Resources:

The Executive’s Guide to the Top 20 Critical Security Controls Tripwire has compiled an e-book, titled The Executive’s Guide to the Top 20 Critical Security Controls: Key Takeaways and Improvement Opportunities, which is available for download [registration form required]. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

