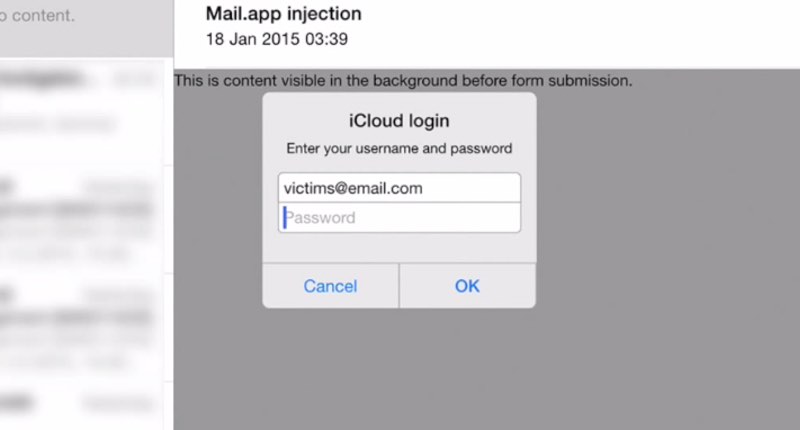
I would wager that most people who have an iPhone or iPad use the default Apple iOS Mail application, rather than a third-party app, to read their email. And if you're one of those people, you could be at risk from an unpatched vulnerability that could allow hackers to convincingly trick you into handing them your passwords. As The Register describes, Ernst and Young security researcher Jan Soucek has gone public with details of a serious flaw that he found in the default Mail app.
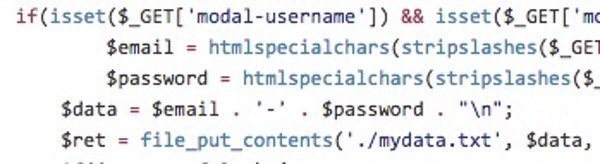
"Back in January 2015 I stumbled upon a bug in iOS's mail client, resulting in <meta http-equiv=refresh> HTML tag in e-mail messages not being ignored. This bug allows remote HTML content to be loaded, replacing the content of the original e-mail message. JavaScript is disabled in this UIWebView, but it is still possible to build a functional password "collector" using simple HTML and CSS."
A video made by Soucek demonstrates the serious risk that a hacker could exploit the flaw to steal passwords, such as those belonging to a victim's iCloud account. https://www.youtube.com/watch?v=9wiMG-oqKf0&rel=0 In a nutshell, Soucek has found a way to do something which any properly-working email client should never allow – popping up a realistic message box asking for a password to be entered. Users could be easily duped by such a message to enter, as in the video example above, their iCloud credentials. Sneakily, the attack code uses cookies to ensure that it is only displayed once on each victims' computer, reducing the chances of suspicions being raised that something odd has occurred.
And what trouble could come from a malicious party getting hold of your Apple iCloud details? Well, you shouldn't have to think very long before you remember the plight of various female celebrities who were embarrassed to find their intimate snapshots plastered all over the internet last year after their accounts were compromised. Of course, the flaw could easily be exploited in attempts to harvest passwords for non-iCloud accounts, as well. Soucek says that he notified Apple about the vulnerability, sharing technical information about how it worked, on 15 January 2015. But at the time of writing, the bug has yet to be fixed.

Controversially, Soucek has now released code demonstrating how the vulnerability can be exploited on Github, potentially putting it in the hands of malicious hackers and identity thieves. Although I can understand his frustration with Apple's lack of response for fixing the issue, Soucek could have applied pressure to the company by demonstrating the flaw to the tech media, rather than releasing exploit code for potential misuse. Meanwhile, as we wait for Cupertino to roll out a patch, it would be wisest to either exercise extreme caution whenever an unexpected pop-up appears while perusing our Mail inbox, or use a third-party email app instead. Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

