
Here's a piece of advice for anyone responsible for securing a corporation's data: If you discover security researcher Randy Westergren is using your app, you had best take a long hard look at whether you are protecting your users' information properly. Because, if you're not, there's a good chance that he might be about to tell you what you're doing wrong. Westergren, who has recently uncovered security flaws in wine-loving app Vivino and Verizon's My FiOS app, has most recently turned his attention to the Marriott International Android app, used by travellers around the world to book their hotel stays. The issue, patched last week, made it simple for attackers to access the reservation and personal details of Marriott customers via its web services, exposing check-in dates, victims' last names, and victims' contact information including physical address, email address and partial payment card data.
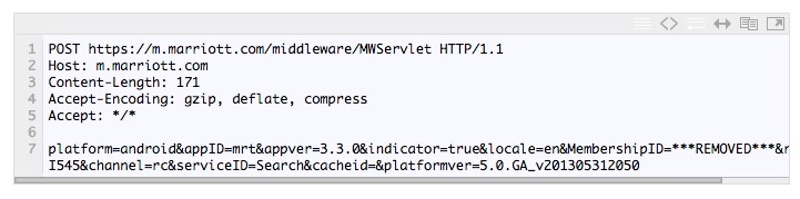
It turned out that Marriott's Android app didn't need to use any authentication to query Marriott's web services for reservation information. All it required was a Membership ID. Which meant that if Westergren, or someone malicious, wanted to access the details of many Marriott Rewards members all he would have to do is change the Membership ID data being used to query the web server. Sure enough, Marriott's database began to spit out information:
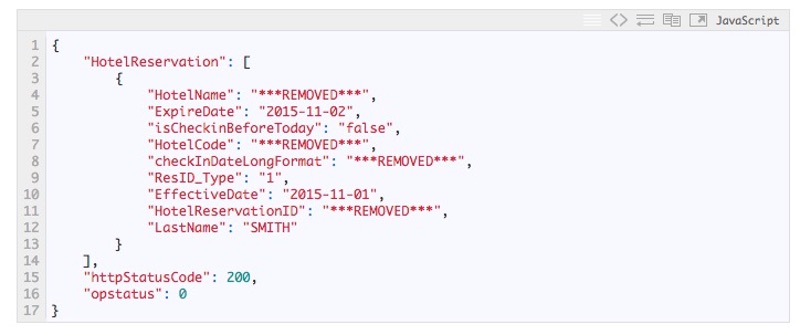
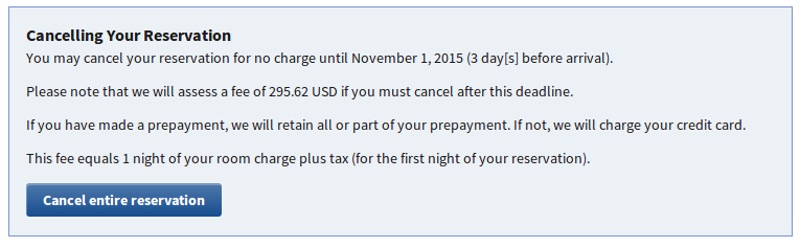
Westergren discovered that this was more than enough information to allow him to cancel, or alter, other people's hotel reservations:
In his blog post describing the vulnerability, Westergren explains how he discovered that no authentication was required to fetch details of an upcoming reservation. All that was needed was the rewards number Membership ID and the traveler's surname - both pieces of information which had been provided by the insecure web service.
"...in order to completely manage a reservation on Marriott’s website, one only needs the reservation number along with the last name of the customer."
It's easy to see how a vulnerable database like this could easily be exploited by cybercriminals eager to scoop up the personal information of travellers. Fortunately, Westergren is a strong believer in responsible disclosure - rather than making a quick name for himself by going public about vulnerabilities before companies have had a chance to fix them. Unfortunately, Westergren found it very difficult to find someone at Marriott who could fix the problem.
"It was difficult to get in contact with the right person at Marriott. I attempted the best practice email format for security issues ([email protected]), but the mailbox didn’t exist. After over a month of trying Twitter and some LinkedIn contacts, I finally got in touch with the someone in information security."
Fortunately, once Marriott's security team were briefed on the seriousness of the issue, they resolved it within approximately 24 hours. That's an impressive turnaround by Marriott, but it's disappointing that it wasn't more obvious how to contact the hotel chain about a serious security hole. If you run an organisation which collects users' information, make sure you tightly control access to the sensitive data and don't make a simple mistake like allowing an attacker simply alter a user ID to see other people's records. Also, be sure to make it clear on your website how people should contact you if they believe they have found a security issue. Finally, if Westergren drops you an email about what he's found while checking out your smartphone app, pay attention. Chances are that you will want to fix it as soon as possible.

