Back in 2013, technology giants Apple, Microsoft, Facebook and Twitter all suffered a serious security breach. Their corporate networks had all been attacked by the same hacking gang, after Mac-using staff visited a website for iOS developers hosting a zero-day Java exploit. The previously unseen Pintsized Trojan horse was able to waltz around the Gatekeeper protection in OS X, and install itself on computers posing as a piece of printing software called cupsd. With Pintsized successfully installed, remote hackers were able to gain unauthorised access to systems and data. For instance, at Twitter some 250,000 users had limited information exposed as a result of the hack, and it was revealed that a number of developers' computers at Apple's Cupertino HQ had also been compromised.
Now newly-released research from security firms Symantec and Kaspersky reveals that a much wider range of corporations have been hit by the hackers since at least 2011 - with law firms and companies involved in corporate mergers and acquisitions targeted, as well as businesses in the healthcare, investment, pharmaceutical and technology industries. What may surprise onlookers, is that security researchers do not believe the attacks are state-sponsored, but are instead financially-motivated economic espionage. Variously known as "Wild Neutron" or "Morpho", the gang is thought to be a highly organised professional organisation, uninterested in stealing credit card data or customer databases, but instead focused on high-value corporate information which could be exploited for insider dealing. The investigation into the hacking gang follows the news last month that the United State SEC was hunting a group of insider-trading hackers stealing sensitive information, such as details of company mergers, from publicly traded companies for financial gain. Clearly, some hacking gangs are becoming more ambitious in their attacks, using their skills to maximise their profits. Symantec says that it has uncovered 49 different organisations in more than 20 countries that have been attacked by the Morpho/Wild Neutron gang. The vast majority of victims are located in Europe, the United States and Canada. In some cases it appears that smaller offices can be initially targeted to gain a foothold in later attacks against headquarters:
"[We] found evidence that Morpho has attacked three major European pharmaceutical firms. In the first attack, the attackers gained a foothold by first attacking a small European office belonging to one firm and using this infection to then move on to its US office and European headquarters. This template appeared to be followed in the two subsequent attacks on big pharma firms, with Morpho compromising computers in a number of regional offices before being discovered."
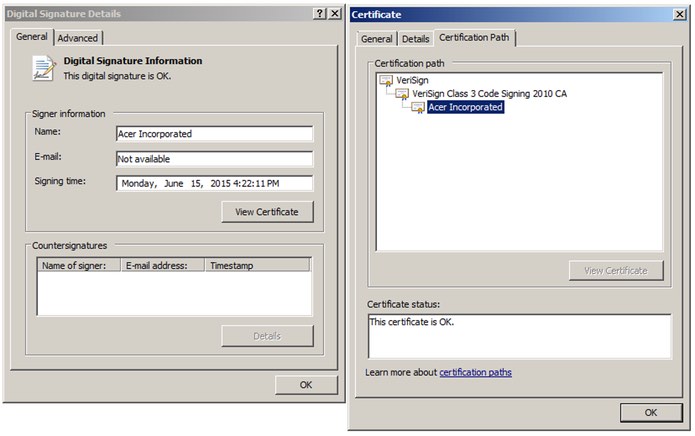
Companies involved in commodities such as gold and oil have also been fallen victim to the attacks, as have law firms specialising in finance and natural resources. Most recently, as Ars Technica reports, the hackers have managed to bypass the protection built into some operating systems by using a valid digital certificate issued to Taiwanese electronics firm Acer.
Meanwhile, the Pintsized backdoor Trojan has been ported to the Windows platform since the attacks against Facebook, Twitter, Microsoft and Apple, proving its worth time and time again by helping the hackers penetrate the networks of corporate victims. The best defence against such professional hackers is to lock down your systems with layered security. Keep your systems patched and your protection software updated. Configure your security software so it can reduce the threat of zero-day attacks. Encrypt sensitive information, and enforce the use of strong, hard-to-crack passwords and multi-factor authentication where available. Ultimately, your best defence might be to adopt the mindset of the hackers. If you were to hack your company - how would you go about it? Find the weak points inside your organisation's defences before the real hackers do.

