
The GHOST vulnerability (CVE-2015-0235), which was discovered by researchers in the GNU C Library (glibc), allows local and remote access to the gethostbyname*() functions in certain cases. Although the vulnerability was just recently disclosed, the vulnerability was introduced in glibx-2.2 on November 10, 2000. Fortunately, this was fixed on May 21, 2013 in glibc version 2.18, but as of now, it is still unknown if hackers have been actively exploiting it. CVE-2015-0235 has been listed given a critical CVSS v2 score of 6.8. While not as serious as ShellShock, the GHOST vulnerability still poses a potential threat. We recommend quickly responding to this threat and applying the patch available from your Linux distributor. Tripwire IP360 customers can immediately add custom rules, update ASPL release 599 or later and detect if this vulnerability is present in their network. Additionally, by using a command output capture rule (COCR), Tripwire Enterprise users can quickly and easily detect vulnerable systems within their environment. To find the GHOST vulnerability in your environment using Tripwire Enterprise: To detect vulnerable systems with Tripwire Enterprise, customers can download custom content for detecting glibc versions in the Tripwire Cuestomer Center. This can also be done by your Tripwire Enterprise administrator using command output capture rules, which will check for the version of glibc on the system. To show how this is done quickly and easily we have a sample script available. By comparing the major version number reported back against the vulnerable versions of glibc (2 through 18), the script can report back if the system has a vulnerable version of glibc installer or not. While this will detect if a vulnerable version of glibc is present on the system or not, it does not detect if the gethostbyname*() function is presently being used or if it is being used in a vulnerable manner. Check with the vendor of the installed applications on the asset to determine if the gethostbyname*() function is used.
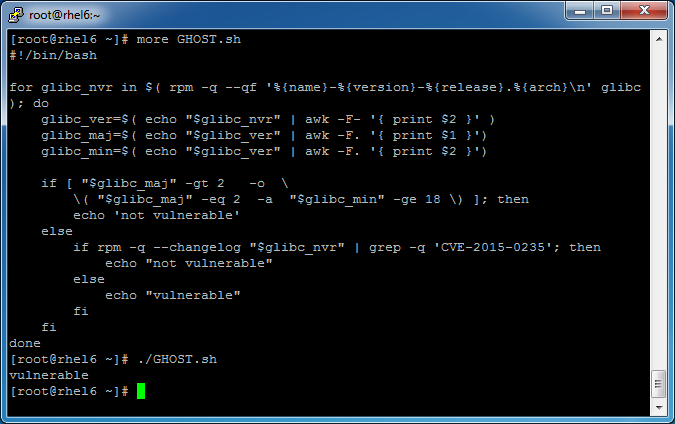
While this will detect if a vulnerable version of glibc is present on the system or not, it does not detect if the gethostbyname*() function is presently being used or if it is being used in a vulnerable manner. Check with the vendor of the installed applications on the asset to determine if the gethostbyname*() function is used.

