Achieving the DoD’s Top Three Compliance Requirements
With unique compliance requirements across a wide variety of platforms and systems, protecting the U.S. Department of Defense (DoD) community is a unique responsibility. A deep understanding of those requirements is a prerequisite for vendors seeking to support the DoD’s security initiatives and is critical to the success of its mission.
Tripwire has demonstrated its expertise in meeting DoD requirements for nearly two decades, helping over 500 DoD customers achieve compliance, evolve as requirements evolve, and improve their overall cybersecurity. Tripwire compliance solutions cover over 2,000 federally-mandated security compliance OS combinations including NIST 800-53, FISMA, DISA STIGs, and others.
Based on recent work with DoD customers, Tripwire has identified three of the DoD’s top-of-mind compliance requirements that are presenting a variety of hurdles that few DoD partners have the expertise to help agencies overcome.
If the following requirements have one thing in common, it’s that they all bring both tremendous challenge and promise to the DoD’s cybersecurity mission.
#1 Compliance Requirement: CMMC
Given the priorities outlined in the Biden Administration’s latest Cybersecurity Executive Order—many centered around supply chain security—achieving the Cybersecurity Maturity Model Certification (CMMC) requirement takes on an even greater level of significance and urgency for DoD partners, as well as for agency decision-makers.
How it Works
While meeting CMMC requirements is of primary concern for DoD partners, DoD procurement organizations need a thorough understanding of how to implement CMMC language in RFPs.
Agencies, overall, have a vested interest in seeing their key partners demonstrate compliance in order to enable continuity of operations.
Bid solicitations will indicate whether a contract requires compliance with CMMC. As the CMMC Audit Bureau (the body responsible for certifying auditors) ramps up the auditing infrastructure, the number of contracts subject to CMMC will increase. By 2026, all new contracts are expected to include CMMC compliance.
While a bidder and its subcontractors will be required to demonstrate compliance prior to the bid being awarded, bidders will not be required to be compliant in order to make a bid. The winning bidder will be able to expense certain costs of compliance to help mitigate the impact of CMMC on small suppliers.
In the meantime, DoD officials are encouraging suppliers to use the Public CMMC model to perform “self-checks.”1 This is where Tripwire can start the CMMC journey with companies of all sizes and CUI sensitivity levels and relieve their concerns from start to finish.
The Tripwire Advantage
CMMC is designed to scale based on the sensitivity of the data handled by a contractor. As the data becomes more sensitive, the number and difficulty of required practices increases. Because of this, CMMC is organized into five levels. For example, at Level 1, a contractor is only required to comply with 17 practices, whereas a Level 5 contractor must comply with 171 practices (the 15 practices of Level 5, plus all of the lower level practices).
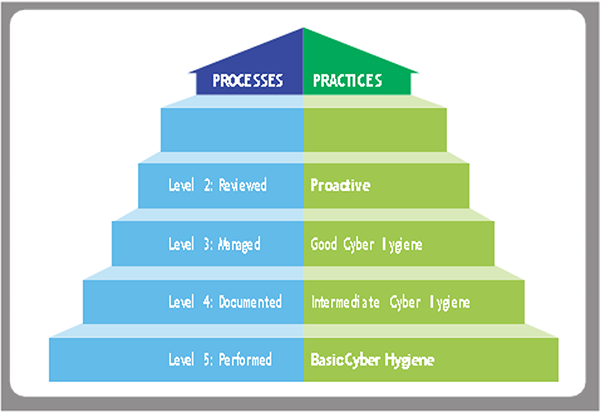
Also, the level of cybersecurity maturity attained by contractors must increase with the sensitivity of the data handled. At Level 1, contractors must demonstrate that they have changed the default passwords on wireless access points, but they don’t have to have written policies or controls that monitor access point passwords.
As the CMMC level increases, contractors are expected to operationalize processes. At the highest CMMC levels, contractors are expected to actively tune their cybersecurity tools and processes to respond to a changing threat landscape. The image below depicts this expectation of increasing maturity.
The role of Tripwire® Enterprise in CMMC is to monitor the network for compliance to CMMC requirements and to provide evidence auditors can use to confirm compliance. Specifically, it inspects devices on the network and verifies that practices have been implemented and are being properly maintained.
Tripwire Enterprise eliminates the reporting challenge of CMMC by creating reports that demonstrate compliance to auditors. For example, if network device passwords are supposed to be changed every three months, Tripwire regularly scans them and reports if their passwords were indeed changed. If a password has not been changed according to policy, the variance is flagged in the report; a waiver or explanation is then required to explain why the policy was not followed.
#2 Compliance Requirement: Comply-to-Connect
Comply-to-Connect (C2C) is a cybersecurity framework that began in 2013 to help DoD and Intelligence agencies manage their growing number of endpoints. Pilot programs at various base locations identified tools and technologies that could successfully stop unsecured devices from joining the network. Due to the pilot success, DISA expanded the initiative DoD-wide and identified the technologies needed to restrict access for devices that do not comply with established standards and configurations while “allowing real-time visibility of all IP endpoint, network infrastructure, and internet of things (IoT) devices,” as detailed in DISA’s RFI.
According to DISA’s recently released Zero Trust Reference Architecture (a cybersecurity model on center stage of the White House’s Cybersecurity Strategy), controlling access to resources based on the risk of the user and devices is the baseline requirement for Zero Trust. Comply-to-Connect is one of the capabilities “...representative of an end-state Zero Trust implementation.”2
How It Works
A converged, single platform discovers, identifies, categorizes, classifies, and profiles all devices connecting to networks comprising the DoDIN (Department of Defense information networks) to include devices from every USCYBERCOM defined endpoint category (i.e., physical and virtual workstations, physical and virtual servers, networked user support devices and peripherals, mobile devices, network infrastructure devices, platform information technology devices, and Internet of Things (IoT) devices). In doing so, it uses the widest variety of both passive and active network-based and host-based discovery methodologies.
In an ideal environment, a robust solution would provide the following workflow:
- Remote users connect via VPN to the closest data center (if connecting from an office, VPN access is not needed) and potentially via SECURE PROXY.
- Once connected, users authenticate through an access control server. After successful login, Forescout (the designated DoD compliance assessment platform) sees the live connection and begins the C2C process.
- The C2C process requires that the endpoint passes “DoD Service based policy” before being allowed onto NIPRNet. This policy generally includes the need to pass a vulnerability assessment and possibly a compliance assessment, etc.
- Platform then reaches out to vulnerability solution such as Tripwire IP360™ and gathers the latest scan results to qualify pass/fail.
The Tripwire Advantage
Tripwire is the ideal tool to integrate into the Forescout platform. Only Tripwire can provide all of the following actions using the award-winning agentless vulnerability management (VM) solution Tripwire IP360 coupled with Tripwire Enterprise’s ability to demonstrate compliance with an established required baseline:
- Agent and/or agentless technology to assess compliance to connect to the DoD network
- Pooled load balanced access points to parse collected data into actionable results ensuring continuous connectivity
- A hierarchy update system that ensures its VM agents are updated with the latest rules the moment they connect to the network
- Pooled and load balanced access points to pass its results up the chain for reporting
“Eighty-five percent of breaches in 2020 involved the human element. Phishing was present in 36% of breaches in our dataset, up from 25% last year. Business Email Compromises (BECs) were the second-most common form of Social Engineering. This reflects the rise of Misrepresentation, which was 15 times higher than last year.”
- Verizon 2021 Data Breach Investigations Report
Not only does Tripwire provide the latest scan results, but also it enables Forescout to assess whether the data is within the “freshness” period. If the data is outside the bounds of the fresh ness period, Tripwire IP360 will update the endpoint with the latest VM Rules
(ASPL) and force a rescan that can reassess the results for policy pass/fail.
In the instance where Forescout periodically assesses connected-endpoints scan results to ensure they are fresh, Tripwire IP360 assesses the fresh ness period of the latest scan results. It passes them to Forescout if fresh, resulting in no need to rescan the endpoint.
#3 Compliance Requirement: Cybercrime and the Internal Threat
The majority of attacks that result in successful data breaches are simply not that complex or novel, relying instead on well-known, tried-and-true methods. Yet most agencies lack the time and expertise to develop the security content—the breach detection rules and configuration hardening policies for servers—that can deter attempts and foil breaches and data loss. With a nationally sized problem at hand, consistent implementation of basic controls can go a long way towards improving the situations.
How It Works
In order to prevent a breach, cybersecurity controls are needed to assess configurations against a set of frequently updated configuration hardening tests.
These tests focus on four main areas to protect against host-based attacks that stem from malware:
- Tightening communications with the monitored server, while monitoring the critical components of the OS—so that if an attack occurs, it’s more likely to be detected in real time.
- Reducing the attack surface by disabling services and system components (am I hardened? Am I vulnerable?).
- Using a variety of cybercrime rule tactics, such as monitoring for changes in processes, services, listening or established port sessions, startup and scheduled tasks, new file drops (software), ACLs, hashes, and a host of other attributes along with firmware.
- Protecting the audit trail so that if an attack succeeds, forensic data helps you detect it and modify systems to fend off subsequent attacks.
Armed with the assessment results, agencies can quickly update failed configurations and harden their servers.
The Tripwire Advantage
Tripwire has long been an industry leader in developing security content that strengthens the DoD’s security and ensures the integrity of servers and their configurations. Tripwire provides Cybercrime Controls™ for Tripwire Enterprise that leverage MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) framework, offering hundreds of tests for hardening against and detecting activities associated with cybercrime behavior coming from external and internal threats.
Cybercrime Controls includes a set of Tripwire-developed breach detection rules that immediately detect changes to the most common server attack vectors: local firewall configurations, scheduled tasks, startup tasks, and more. Because these items should rarely change, it’s important to be immediately alerted when they do.
Tripwire studies examples of attacks and malware, classifies their actions and behaviors, and translates those into specific, targeted rules. Because these rules are available as a free download to Tripwire Enterprise users, DoD agencies can immediately benefit, sparing the time and effort of developing policies in-house.
Anti-virus monitoring allows agencies to identify whether AV software is installed and actually running on the service, and if it is up to date. Tripwire offers monitoring support for Symantec, McAfee, Trend Micro, Sophos, and Kaspersky Lab AV products—with the ability to add any other AV product.
The Compliance Partner of Choice
Agencies that successfully apply the necessary policies in their compliance programs are able to monitor with confidence, decide with confidence, and operate with confidence. A strategic partner to the Department of Defense for over 20 years, Tripwire has helped thousands of federal customers improve their cybersecurity. As the pioneers of file integrity monitoring (FIM), Tripwire’s expertise is built on a history of innovation that includes over 40 patents. Tripwire’s award-winning cyber integrity solutions are used across the DoD, intelligence agencies, and nearly every civilian federal department, independent agency, as well as the legislative and judicial branches.
“Tripwire understood the requirements they had, supported the evaluation, and provided constant communication. Tripwire took their requirements seriously.”
- U.S. Military Agency Partner
Sources
- https://www.fedscoop.com/cmmc-contractor-timeline-for-certification/
- https://dodcio.defense.gov/Portals/0/Documents/Library/(U)ZT_RA_v1.1(U)_Mar21.pdf