Tripwire’s File Integrity Monitoring (FIM) Solution
To enhance your Federal Information Security Management Act (FISMA) compliance grade, you must implement one of the most challenging controls in NIST SP 800-53: the Controls, Family: System Information & Integrity (SI) 7 requirement. SI-7 states that organizations must employ automated and centrally managed integrity verification tools to detect unauthorized change. This level of visibility can be difficult enough to achieve, but SI-7 also requires organizations to incorporate the unauthorized changes they find into their incident response process and be ready to pass an audit trail demonstrating these capabilities.
Tripwire’s file integrity monitoring (FIM) solution delivers the capabilities necessary to address this requirement by providing a deep understanding of all the changes occurring in your environment and, when desired, provides seamless integration into IT Service Management (ITSM) solutions to create a workflow for the smooth exchange of system change and security configuration state information with a wide variety of compliance, operations and reporting/ analytics solutions. Tripwire ITSM partners integrate with Tripwire® Enterprise so that inventory can be shared with, and used within, the CMDB. ITSM partners include BMC Remedy, CA, Cherwell Software, HP Service Manager, IBM, Atlassian (JIRA), Landesk, Microsoft and ServiceNow.
Requirements of NIST SP 800-53 SI-7:
SI-7 Software and Information Integrity
Control:
- Employ integrity verification tools to detect unauthorized changes to the following software, firmware, and information: [Assignment: organization defined software, firmware, and information]; and
- Take the following actions when unauthorized changes to the software, firmware, and information are detected: [Assignment: organization defined actions].
Supplemental Guidance: Unauthorized changes to software, firmware, and information can occur due to errors or malicious activity. Software includes operating systems (with key internal components, such as kernels or drivers), middleware, and applications. Firmware interfaces include Unified Extensible Firmware Interface (UEFI) and Basic Input/Output System (BIOS). Information includes personally identifiable information and metadata that contains security and privacy attributes associated with information. Integrity checking mechanisms—including parity checks, cyclical redundancy checks, cryptographic hashes, and associated tools—can automatically monitor the integrity of systems and hosted applications.
Control Enhancements:
- Integrity Checks
- Automated Notifications of Integrity Violations
- Centrally Managed Integrity Tools
- Tamper evident Packaging
- Automated Response to Integrity Violations
- Cryptographic Protection
- Integration of Detection and Response
- Auditing Capability for Significant Events
- Verify Boot Process
- Protection of Boot Firmware
- Confined Environments with Limited Privileges
- Integrity Verification
- Code Execution in Protected Environments
- Binary or Machine Executable Code
- Code Authentication
- Time Limit on Process Execution Without Supervision
- Runtime Application Self-Protection (RASP)
Tripwire’s Response to SI-7
Tripwire, the leading provider of IT security and FISMA compliance automation solutions, can help your agency take control of a wide range of security and compliance challenges including SI-7. Tripwire has a trusted track record and reputation with FIM. Over half the Fortune 500 companies and almost every Cabinet agency uses Tripwire solutions.
Tripwire Enterprise combines file and system integrity monitoring, compliance policy management, real time analysis of detected change, and prescriptive remediation guidance to help IT organizations achieve and maintain compliance. It does this by immediately detecting file and configuration changes through real time continuous file integrity monitoring. Tripwire also incorporates integrations to ITSM tools to identify authorized and unauthorized changes to system configuration components including those that introduce security risk or take systems out of compliance (security controls). Remediation guidance is provided for undesirable changes so IT and Security teams can fix issues quickly. Tripwire Incorporates apps and actions that allow admins to auto-promote other changes based on patch manifest matches, severity values and items deemed to be “business as usual” these action types simplify the implementation of a solid SI-7 focused tool.
Tripwire also offers Tripwire LogCenter™, a complete log and security event management solution that integrates with Tripwire Enterprise to deliver even greater control over IT infrastructure. For example, in addition to standard out of box change detection, side by side analysis and alerting in Tripwire Enterprise, changes discovered in Tripwire Enterprise are now matched to the footprint or “log events” surrounding the change right in the Tripwire Enterprise GUI. Tripwire LogCenter contains normalization and correlation rules alongside reporting to validate SI-7 control policies right out of the box.
Tripwire IP360™, a leading vulnerability management solution, proactively discovers, profiles and assesses the vulnerability risk of all wired and wireless devices on an organization’s network. Tripwire IP360 can quickly detect vulnerabilities and prioritize risk using business context data unique to your organization. Remediation of identified vulnerabilities is simplified through integrations with reporting and ticketing tools. Tripwire Enterprise uses vulnerability intelligence tags from Tripwire IP360 (vulnerability risk, specific vulnerabilities, specific applications, ease/ impact of exploit, time endpoint was last scanned) to provide deeper security visibility and to further prioritize suspicious changes on critical endpoints.
Tripwire Advantages for FIM and FISMA
Tripwire has a solid reputation as a proven FIM provider. As matter of fact, it was specified as the industry standard in the original PCI standards. In addition to comprehensive and reliable file integrity monitoring capabilities, Tripwire Enterprise includes comprehensive policy compliance management capabilities with a library of over 2000 policy and OS combinations that enable proactive validation of the state of the IT infrastructure against internal and external best practices, security and compliance policies.
Here are some distinguishing features of Tripwire Enterprise’s capabilities:
- Baselines endpoints and assesses systems against a known good configuration—provides differences between like systems.
- Real time system change detection— assesses change in detail to include “when, what, where and who” information. Combined with Tripwire Log Center or other SIEM tool and you will also have instant footprint data.
- Compliance and security policies— assesses your systems for their current secure/hardened state. Use our remediation guidance or auto-remediation workflows (where applicable) to bring your systems to a compliant state. Continuously monitor to ensure systems remain compliant, saving manpower and dollars by staying compliant.
- Reduces file system auditing resource usage by utilizing Tripwire Enterprise’s built in “event generator” on endpoints.
- Full role-based access control (RBAC) capabilities to allow permission based login and tool usage—users can login and only use specific components of the tool they are authorized for. For instance, a Windows admins can log in to Tripwire Enterprise and only see the “windows assets” they are responsible for.
- As an Operations tool—many customers rely on Tripwire Enterprise to track change, so they can easily determine what went wrong when systems or applications are no longer functioning or when router changes block access to resources.
- As a Security tool—Tripwire solutions are regularly relied upon to monitor for and assess endpoints for deviations that are in line with cyberattacks and breaches.
- As a tool to assess Indicators of Compromise—Tripwire Enterprise hashes nearly everything and stores these values in its database. Users can search for known bad hashes or use our File Analytics tools to search local or SaaS-based partner databases for hash matches.
- As an isolation tool—Tripwire Enterprise can utilize “execution” actions to isolate systems that have known critical risks or contain malicious information.
- Tripwire Enterprise can also alert when items that are not allowlisted (whitelisted) appear in your environment (services, applications, open ports, group memberships, routes and valid users).
- Combine our Ticketing Event Integration Framework (TEIF) with Tripwire Enterprise to assess change against ITSM tools such as Service Now, Remedy, Jira, Check it and many others. This allows Tripwire Enterprise to auto-promote changes that have an approved status. It also allows IT organizations to utilize Tripwire Enterprise to close out approved CRs or create new incidents when unapproved changes occur.
- Add the Tripwire Dynamic Software Reconciliation app to give Tripwire Enterprise the ability to assess all changes during maintenance windows against patch manifests to determine valid “patch related” change. Tripwire Enterprise then promotes patch related changes with no need of reconciliation.
- Combine Event Sender with Tripwire Enterprise to provide “event” specific format and expanded context to your SIEM tool of choice.
Tripwire provides truly continuous compliance monitoring by detecting changes that impact security parameters as they occur, in contrast to typical periodic full scans of endpoints. Tripwire’s approach reduces the audit performance impact on target systems and the network through the use of a built In “event generator,” while allowing organizations to monitor and maintain compliance over time—even as change occurs. Tripwire integrates with a wide range of solutions to extend the insight on the change, which results in enhanced security and optimized processes. Tripwire integrates with SIEM providers to deliver more context around the events they are collecting for investigation.
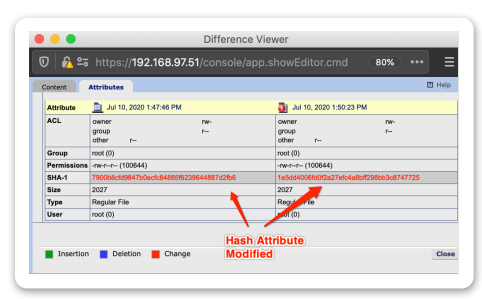
Tripwire integrates with ITSM solutions for closed loop change control. To increase security, Tripwire integrates with File Analytic feeds and sandboxing technologies to gain additional insight or validation on the potential threat. Tripwire can detect and take action on zero day malware attacks in real time.
These advantages are why many FISMA customers are committed to Tripwire. Tripwire’s distinct value of deep and real time understanding of systems and changes sets the company apart from the others. Remove your SI-7 requirement struggles with Tripwire and achieve FISMA compliance with a worthy grade.
As a premiere FIM provider, Tripwire has expanded on this core competency to deliver advanced enterprise class solutions that include configuration and policy management, file integrity monitoring, vulnerability management, log management, and reporting and analytics. Tripwire is the choice for security, FISMA compliance and operations needs.
Conclusion
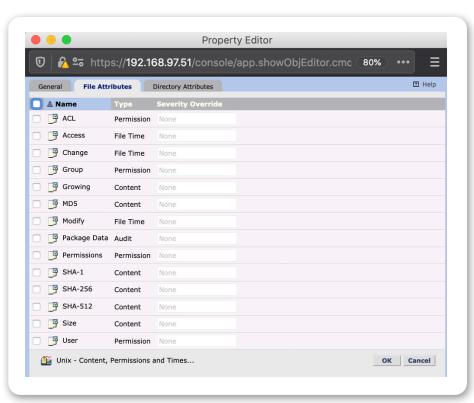
FIM goes beyond SI-7 compliance. FIM is basic security hygiene that all organizations should have to track malicious activity. FIM is critical for IT operations to keep systems up and optimal with the key insight to correct and restore. Remember bad users don’t just enter a network and reside on a wire, in short order, bad users end up on an exploited endpoint.
Ready to Dig Deeper?
Tripwire pricing is tailored to your specific system requirements, so you can rest assured your quote will be matched to the exact amount of coverage you need and nothing more.