What is Amazon Web Services?

Amazon Web Services (AWS) is everywhere, and understanding what AWS is and how it works can be a steep learning curve for anyone who isn’t accustomed to the world of cloud services. When an organization decides to take their computing processes, content delivery or data storage off-premises and into the cloud, it takes a cloud platform like AWS, Google Cloud Platform (GCP) or Microsoft Azure to do it. AWS is the most widely-used public cloud platform of its kind, with globally-distributed data centers, millions of users and 156 unique services.
AWS is an example of what’s called “public cloud,” meaning when an organization opts for AWS, they are outsourcing the computing power, storage, and management of the platform to a third-party over the pubic internet rather than overseeing all of that themselves. On the other hand, an organization can choose the “private cloud” route, meaning they maintain their own cloud datacenters, servers, and associated processes themselves.
Who's Responsible for Cybersecurity Within AWS?
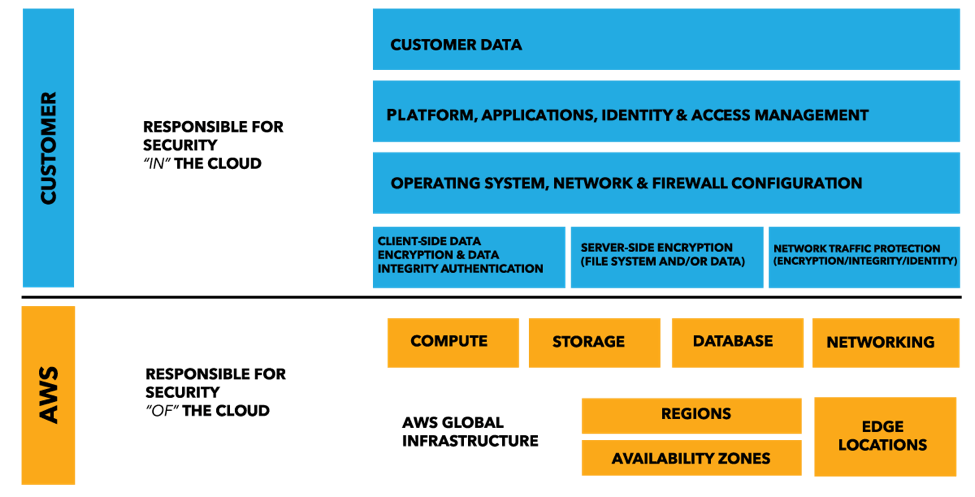
There’s a common misconception that cloud providers handle all security, possibly left over from the era of hosting providers. The truth is, there’s a lot to cloud security that the customer is responsible for. Amazon uses a shared security responsibility model, meaning that responsibility is shared between AWS and the customer.
The gold area shows security of the cloud, areas which are Amazon’s responsibility—mostly physical things (hardware and physical network resources). Security in the cloud, shown in blue, is the customer’s responsibility. There we have identity and access management, securing data in transit and at rest, network and firewall configuration, policies and configurations, logging, and monitoring. These are all areas which live outside of the operating system and that need attention, in addition to securing everything within each virtual operating system.
AWS Security Breaches
AWS compromises have become quite common. When AWS accounts are compromised, the go-to payload for most of these attackers is cryptocurrencies—the attacker will spin up large virtual instances and start mining for bitcoin (or other cryptocurrency). While the attacker is trying to make themselves some money, those CPU cycles end up costing their victims money. Many stories like this end up with people owing $2,000, $5,000 or even up to $50,000 because of insecure AWS configurations. But that’s not even the worst case.
An example of the worst thing that can happen is a company that was forced out of business due to a hacked AWS account. In 2014, hosting service Code Spaces went from a successful startup to completely out of business after hackers breached the Amazon control panel and deleted everything—all of the servers, source code and backups. This example demonstrates that there’s a real risk to both budgets and operations, and that you need to ensure that you’ve done everything you can to secure your infrastructure.
Fortunately, there is guidance from the Center for Internet Security (CIS). CIS is a nonprofit organization developing global standards to develop and sustain security best practices. In 2016, CIS launched the Amazon Web Services Foundations benchmark policy. This policy is a guideline containing recommendations for how to configure an Amazon Web Services management interface in order to be protected against common threats. Each of these settings is configured within the AWS management console, which functions as a control panel for configuring each AWS service.
Six Security Controls to Prevent Your Cloud
from Getting Hacked
Meeting CIS Benchmarks
There are several tools available to help you figure out if you’re meeting the recommendations from the CIS benchmark policy.
AWSLabs
Amazon, through AWSLabs, has published a script on GitHub. This script determines the values for the CIS recommended configuration options, and presents you with a report of each value whether it meets the recommendation or not.
Tripwire Enterprise
Tripwire Enterprise is a security configuration management (SCM) suite that provides fully-integrated solutions for policy, file integrity and remediation management. As a new Advanced Technology Partner of the AWS Partner Network (APN), Tripwire leverages AWS to deliver cybersecurity solutions via scalable, flexible and cost-effective cloud-based infrastructure. Tripwire Enterprise, along with vulnerability management solution Tripwire IP360™, span on-premises, cloud, and multi-cloud environments to help organizations reduce their overall attack surfaces.
Learn how Tripwire’s suite of foundational controls allows you to utilize the same trusted, on-premises tools with equal effectiveness in cloud.
Joining the AWS Partner Network as an Advanced Technology is part of Tripwire’s commitment to help customers get cybersecurity programs up and running quickly and easily through SaaS-delivered solutions. Starting with the ability to address vulnerabilities, which continue to be the leading cause of major data breaches, we’re making critical security controls easily available through cloud-based delivery.
VP of Product Management and Strategy Tripwire
AWS Security Resources
Ready for Better Cloud Security?
Learn more about how Tripwire can help you secure the configuration of your AWS management account.