
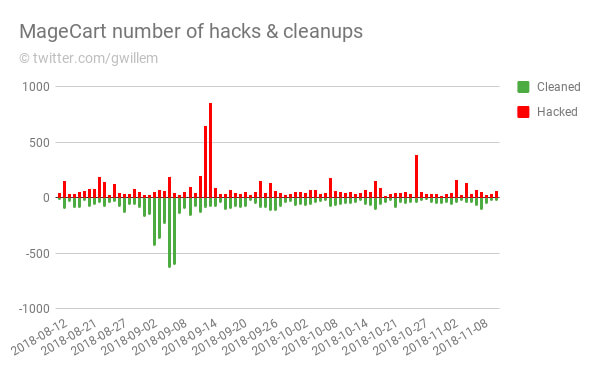
MageCart, the notorious malware that has been haunting online stores by stealing payment card details from online shoppers at checkout, is reinfecting the same websites time and time again. Dutch security consultant Willem de Groot, who has been tracking MageCart and similar threats since 2015 and has come across over 40,000 compromised stores, says in his most recent blog post that merchants are struggling to keep their checkout pages secured. What is perhaps equally concerning is that online stores are cleaning-up their infected webpages only to have them compromised again. Indeed, in the last quarter de Groot's reseawrch reveals that one out of five breached stores have been infected (and cleaned) multiple times. In some cases, de Groot says he has seen the same store reinfected up to 18 times by MageCart. One of the affected online stores belongs to Kitronik, a UK-based company that sells electronic parts including the BBC micro:bit matchbbox-sized computer. The MageCart infestation of Kitronik's Magento-powered online store made the headlines in November, but de Groot revealed that what appeared initially to the outside world to be a single breach was actually a series of reinfections:
Hacked Sep 12, cleaned Sep 20 Hacked Sep 27, cleaned Oct 1 Hacked Oct 19, cleaned Oct 22
During August, September, and October, de Groot says he identified more than 5,400 web domains that are harbouring MageCart-like malware designed to steal credit card information from online shoppers. If one in five of those compromised sites are likely to be infected again, it is clear that MageCart will continue to skim credit card details from unsuspecting shoppers for the foreseeable future. What has become apparent is that the bad guys are beating the good guys, by doing a better job of reinfecting sites than website administrators are at detecting and cleaning up an infection. De Groot reports that MageCart infections typically persist on an ecommerce site for 12.7 days, whereas reinfection typically occurs within 10.5 days. Furthermore, MageCart attackers are taking advantage of the fact that a typical website's security team is more likely to be fully-staffed during the week, leaving a window of opportunity for exploitation to take place at weekends where infections appear to be spiking.
De Groot says there are various reasons why the countermeasures put in place by online stores and their security contractors are often failing:
First, MageCart operatives are getting more sophisticated in hiding their presence and ensuring future access. Once an operative gains access to a merchant’s server, it is common to litter the site with backdoors and rogue admin accounts. Second, they use reinfection mechanisms such as database triggers and hidden periodic tasks to reinstate their payload. Third, they use obfuscation techniques to make their presence indistinguishable from legitimate code. Fourth, it is more and more common for MageCart actors to utilize unpublished security exploits (aka 0days). Researching these requires a significant investment.
"All in all, it takes some very keen eyes and a lot of effort to clean all traces of a breach," says de Groot. That can be true of any hack, of course, but is particularly critical when the site involved is a online store which the public is using to enter its credit card details.

