
Anti-malware providers see a lot of spam and phishing attempts through their users' experiences. For its part, Kaspersky Lab understands how these encounters reveal the ever-evolving toolset of bad actors and their efforts to prey upon unsuspecting users. But it also knows users and security professionals alike can leverage information of these attacks to help make the web a safer place. That's why the Russian security firm analyzes all the spam and phishing attempts detected by its products and shares its findings with the infosec community every quarter. Here's what Kaspersky Lab's researchers found in the second quarter of 2017.
Spam and Phishing at a Glance
In Q2 2017, Kaspersky Lab saw the percentage of spam in overall email traffic increase by 17 percent from the previous quarter. The average percentage for the quarter was 56.97 percent, or about 1.07 percentage points (p.p.) greater than the previous quarter. By far, the largest proportion of 57.99 percent came in April. Here are some other notable spam statistics from the security firm for the quarter:
- Vietnam accounted for the biggest share of world spam at 12.37 percent. The United States was the only other country to register a spam portion in the double digits at 10.1 percent. China was responsible for 8.96 percent of the world's unsolicited messages, followed closely behind by India at 8.77 percent.
- Consistent with the first quarter, more than half (64.57 percent) of spam emails came in either one of two sizes. The "less popular" size category was 20-50 KB at 27.16 percent of all spam. Meanwhile, over a third (37.14 percent) of spammers chose an email size of between zero and two kilobytes, no doubt in an effort to evade detection.
- Trojan-Downloader.JS.SLoad was the most common malware spread via malspam campaigns at 8.73 percent of all malicious attachments.
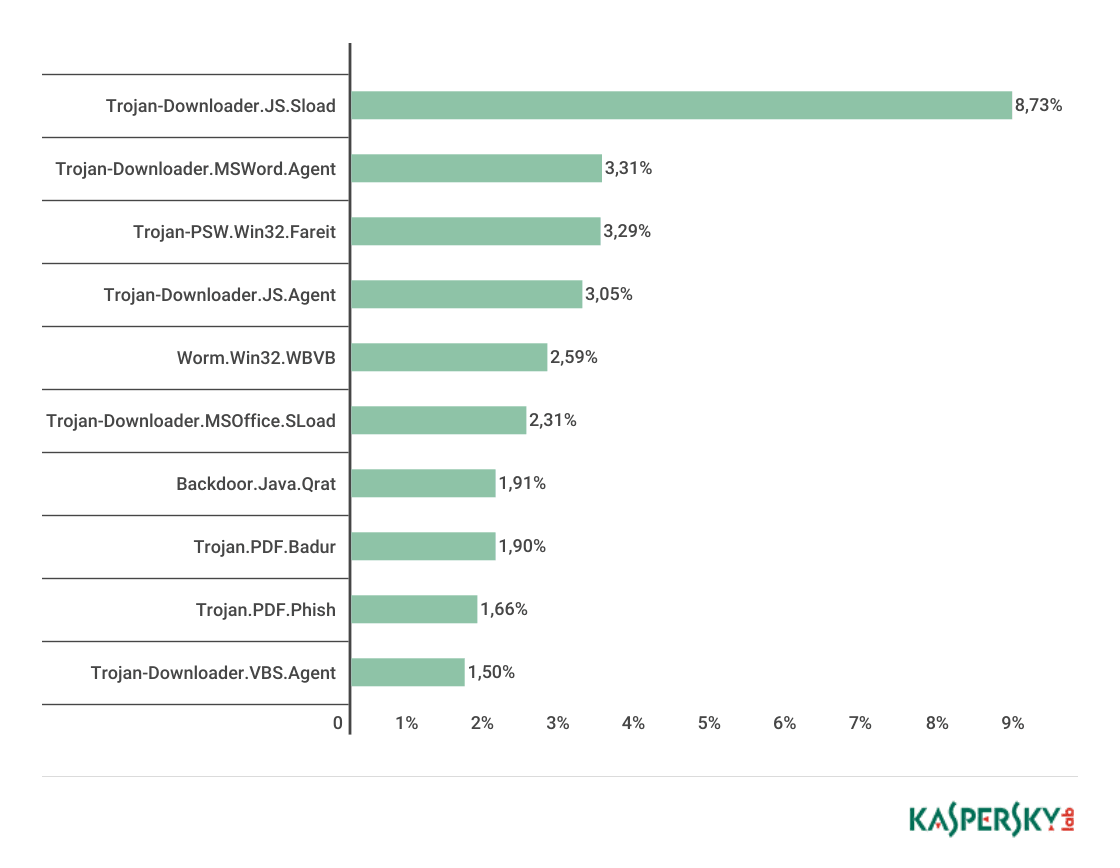
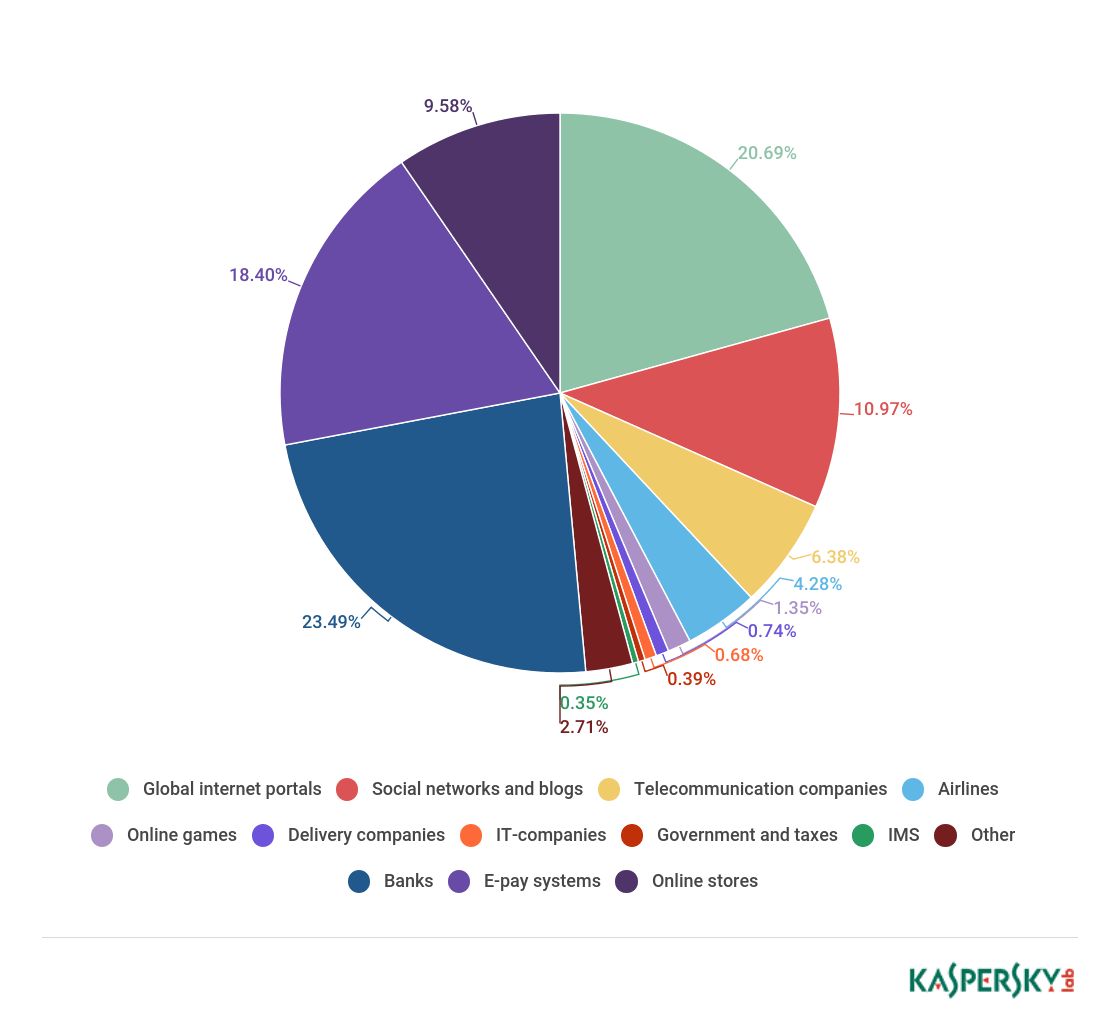
TOP 10 malware families in Q2 2017. (Source: Kaspersky) As for phishing, Kaspersky Lab's products prevented 46,557,343 attempted visits of pages boasting this form of social engineering. 8.26 percent of all Kaspersky users suffered one of these attempts, with Brazil accounting for the largest share (18.09 percent) of phishing attacks. It was followed by China, whose percentage decreased by 7.24 p.p. to 12.85 percent, and Australia, which increased by 1.96 p.p. to 12.69 percent. The vast majority of organizations that suffered a phishing attack in Q2 2017 were banks at 23.49 percent. Even so, payment systems and online stores also saw their fair share of phishing attempts at 18.4 percent and 9.58 percent, respectively. Together, those three company categories accounted for more than half (51.47 percent) of all documented attacks.
Sources of spam by country, Q2 2017. (Source: Kaspersky
Some Notable Developments
Kaspersky Lab detected several notable spam and phishing campaigns in Q2 2017. Among them was a malicious mailing that sought to capitalize on organizations' fear of falling victim to WannaCry. Kaspersky's Darya Gudkova, Maria Vergelis, Tatyana Shcherbakova, and Nadezhda Demidova reveal the details of this particular attack:
"… [The bad actors] sent out fake notifications on behalf of well-known software vendors informing recipients that their computers had been infected with ransomware and had to be updated. The link to the supposed update, of course, led to a phishing page. We came across emails that showed the attackers hadn’t taken much care when compiling their mailings, obviously hoping their victims would be in too much of a panic to notice some obvious mistakes (sender’s address, URLs, etc.)."
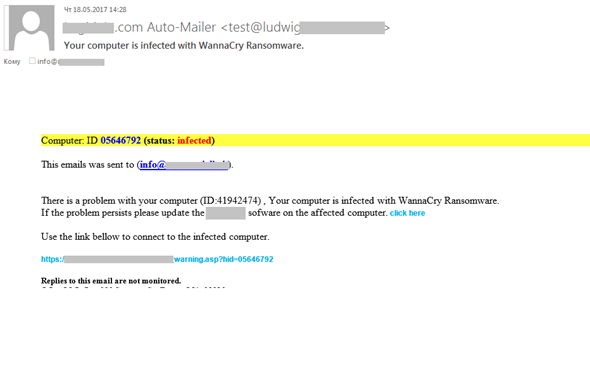
Fake WannaCry infection email. (Source: Kaspersky) Not surprisingly, not all mailings pushed out phishing pages. Some leveraged malicious attachments in password-protected archives to target the corporate sector with fake business correspondence. In so doing, these malicious attachments made it past anti-virus software and loaded either ransomware, which might have encrypted indispensable corporate data, or spyware, which attackers could have used to steal financial data. Others sent out trojan downloaders in emails disguised as notifications from delivery services. As if those types of attacks weren't enough, some nefarious individuals used mass mailings to target companies with domain fraud. These bad actors impersonated an organization involved in the registration of domain names and told the recipient that they needed to activate a domain to confirm their administrator status and ability to manage the registered domain. Kaspersky's researchers explain how the ruse worked:
"…[T]he administrator was told they had a limited time to create a PHP file with specific content in the root directory of the site. The email also stated that failure to observe these conditions would mean the confirmation procedure had not been completed and support for the domain would be suspended. "If the script is launched on the victim’s site, the attackers would be able to gain control of the site and to run any code. In addition, the script makes it possible to collect all user data entered on the site where it is registered and run. The fact that many of these fake emails were sent to addresses belonging to banks, means we can assume that the scammers wanted to collect data entered on the website of those banks, including the logins and passwords used for Internet banking."
Aside from mass mailings, Kaspersky Lab also saw instances where scammers tried to trick users with fabricated free airline ticket giveaways, fake browser warnings, and phishing pages whose URLs were Punycode-encoded.
Security Best Practices for the Future
Users can best protect themselves against spam and phishing attempts by exercising caution around suspicious links and email attachments. Executives can help their employees in this regard by implementing the Center of Internet Security's Critical Security Controls. Doing so will help to strengthen an organization's overall network security posture. For advice on how executives can get started in this regard, please download this resource.

