
On 11 May 2017, President Donald Trump signed an executive order that provides guidance on strengthening the United States' digital security. The directive makes clear that each head of a U.S. federal agency or government department is ultimately responsible for managing their organization's risk. It also emphasizes their use of a specific document to fulfill that obligation:
Effective immediately, each agency head shall use The Framework for Improving Critical Infrastructure Cybersecurity (the Framework) developed by the National Institute of Standards and Technology, or any successor document, to manage the agency's cybersecurity risk. Each agency head shall provide a risk management report to the Secretary of Homeland Security and the Director of the Office of Management and Budget (OMB) within 90 days of the date of this order.
President Trump was wise to incorporate NIST's Framework into his executive order. Originally published in 2014, the Framework is explicitly aimed at helping operators of U.S. critical infrastructure. Even so, plenty of private businesses now use the document's five core digital security functions—Identify, Protect, Detect, Respond, and Recover—to mitigate the risk of ransomware and digital crime more generally on their networks as well as correlate their digital security metrics with their business objectives.
Since its publication, NIST has received lots of feedback from organizations and other parties on Version 1.0 of its Framework. It's gathered these comments from online forums, workshops, and formal requests for information (RFIs) over several years. Now NIST has incorporated these viewpoints into a second draft for Version 1.1 of its Framework. It's done so in the interest of meeting the demands of those that use the document to stay on top of the latest digital threats.
The updates NIST made in Version 1.1 of its Framework (PDF) boil down to five major revisions. These are as follows:
1. Amendments to Digital Security Risk Management Language
In an effort to emphasize the correlation of business results and digital security risk management, NIST added Section 4.0 "Self-Assessing Cybersecurity Risk with the Framework." The Section explores the value of self-assessment and measurement when it comes to organizations security-related investments. As such, it provides some basic guidance on how organizations can best incorporate measurements into the Framework process:
Organizations should be thoughtful, creative, and careful about the ways in which they employ measurements to optimize use, while avoiding reliance on artificial indicators of current state and progress in improving cybersecurity risk management. Any time measurements are employed as part of the Framework process, organizations are encouraged to clearly identify and know why these measurements are important and how they will contribute to the overall management of cybersecurity risk. They also should be clear about the limitations of measurements that are used.
The Section ends by encouraging organizations to innovate new measurements and incorporate them into their application of the Framework "with a full appreciation of their usefulness and limitations."
2. Alterations to an Explanation of How the Framework Can Help Manage Digital Security within the Supply Chain
NIST, which has also published guidance on how companies can recover from data corruption events, made a second major revision by adding the concept of supply chain risk management (SCRM) to Section 3.3 "Communicating Cybersecurity Requirements with Stakeholders." This revision discusses how supply chains factor into critical stakeholder communication and of what SCRM broadly consists. It also identifies a main purpose of SCRM:
A primary objective of cyber SCRM is to identify, assess, and mitigate "products and services that may contain potentially malicious functionality, are counterfeit, or are vulnerable due to poor manufacturing and development practices within the cyber supply chain."
The Section also now includes the following infographic that depicts the relationships connecting the technology supplier, technology buyer, non-tech supplier, non-tech buyer, and organization within a digital security supply chain.
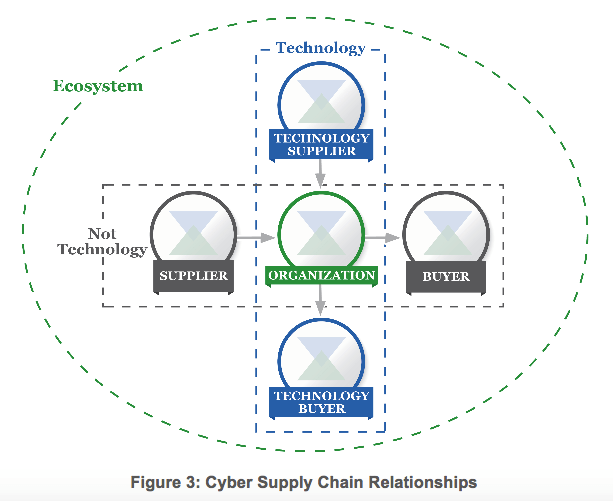
Framework for Improving Critical Infrastructure Cybersecurity Version 1.1 Draft 2 page 17
3. Better Accounting of Authentication
To emphasize the importance of authentication, NIST added a Subcategory to Protect -- Identity Management and Access Control (PR.AC) Category. This Subcategory reads as follows:
PR.AC-7: Users, devices, and other assets are authenticated (e.g., single-factor, multi-factor) commensurate with the risk of the transaction (e.g., individuals’ security and privacy risks and other organizational risks).
4. Consideration of Coordinated Vulnerability Disclosure
In addition to authentication, NIST created a Subcategory for coordinated vulnerability disclosure in the Response -- Analysis (RS.AN) Category that reads thusly:
RS.AN-5: Processes are established to receive, analyze and respond to vulnerabilities disclosed to the organization from internal and external sources (e.g. internal testing, security bulletins, or security researchers).
5. Excision of the Federal Alignment Section
Last but not least, NIST removed a section on aligning the Framework to federal networks. It made this decision following the publication of President Trump's digital security executive order, a document which along with other memoranda and guidance remove the need for federal applicability statements within the actual Framework publication.
A Framework for the Future
Matt Barrett, NIST's lead on the Framework, feels the revised document can help federal and private organizations strengthen their digital security for years to come. As quoted in an interview conducted with Jai Vijayan of Dark Reading:
Given the increasing dependence of organizations on technology, digital trust is an increasingly important topic. In other words, not only does an organization need to manage their cybersecurity risk, but they also need to communicate it in various forms to suppliers, partners, customers, auditors, and regulators. [The] Framework provides a basis for a standardized communication – increasing and organizations efficiency and reducing the chances of miscommunication – and it also provides the high-level methods of determining cybersecurity state, deciding desired state, and planning the improvements necessary to achieve the desired state.
At this time, NIST is currently seeking feedback on whether the revised document reflects the current digital security landscape. It's also looking to see how the changes might affect those who currently use the Framework as well as the likelihood that those who currently don't use the Framework might decide to adopt it. Towards that end, feedback and comments should be directed to [email protected].
NIST will then review those public comments and use them to publish a final Framework Version 1.1 in early 2018. In the meantime, learn how Tripwire can help your organization keep up with NIST's ever-changing Framework compliance standards by clicking here.

