
Mac malware, or macOS malware, exists contrary to the popular belief that Apple’s operating system is immune to online threats. Cybersecurity researchers have been closely observing the threat landscape only to conclude that malware infections targeting Mac devices have increased in 2018.
Is Apple Losing Its Grip?
According to statistics, Mac malware increased by 270% in 2017 compared to 2016. To top that off, four brand new Mac threats were detected only in the first two months of 2018. Previous numbers revealed similar growth: AV-TEST security report for 2016/2017 indicated that Apple systems saw three times more attacks compared to past years. The crumbling privacy of iOS apps also adds up to the controversy of Apple’s state of security. Apparently, iOS apps have been used to covertly collect location histories from tens of millions of Apple devices, via packaged code that belongs to data monetization companies. The story goes that GuardianApp experts unearthed that these apps “present a plausible justification relevant to the app in the Location Services permission dialog, often with little or no mention of the fact that location data will be shared with third-party entities for purposes unrelated to app operation”. Multiple security reports reveal that Mac users, in particular, are increasingly targeted by Trojans, adware, and potentially unwanted programs (PUPs), and even cryptomining malware and ransomware. This makes it imperative for Mac users to be armed and prepared to detect and remove macOS malware in all its forms. So, what are the most widespread mac viruses in 2018?
Scams Such As “Apple wants to make changes”
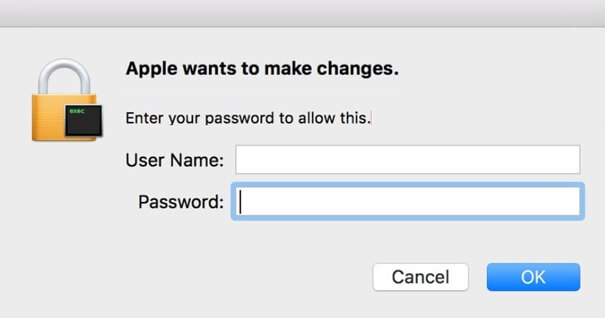
It’s not only Windows that is susceptible to mischievous and smartly crafted scams. Such scams tend to display a pop-up window prompting users to give away personal or financial information. In the case of the recently detected “Apple wants to make changes” scam, users are asked to enter their username and password. The scam is trying to obtain the victim’s Mac credentials, which also puts at risk all the information stored on the device.
Potentially Unwanted Programs Such As Advanced Mac Cleaner
Advanced Mac Cleaner is a potentially unwanted program (PUP). The company who developed this PUP is tied to a range of unwanted apps, and is also known to include various ads in their products to promote other software they have developed. Users affected by this program may be affected by scareware messages trying to trick them into installing even more PUPs. The tricky part is that Mac users may be affected without even knowing it, due to a freeware installation or a bundled software package. On top of that, the intrusive alerts and pop-up messages are not the only things that the Advanced Mac Cleaner can do. A particular file, Info.plist file, which is located inside the application, reveals a list of over 200 various file types that it claims to be able to open. If you try to open a file which doesn’t have a corresponding application associated to it, the file will be opened by Advanced Mac Cleaner. Another example of unwanted behavior is the fake message box linking to the official Advanced Mac Cleaner website. It attempts to install Mac Adware Remover or similar applications. All these programs are equipped with a valid, Apple-provided developer certificate. This means that macOS will install them without any triggered problem.
Browser Hijackers Such As Search.fastsearch.me
In short, Search.fastsearch.me is a website that features a hoax search engine in an attempt to trick affected users into visiting as much sponsored content as possible. This could be explained by the fact that its owners gain revenue for each visit of an ad generated by their website. The website also displays a typical browser hijacker behavior. What does this mean? It is designed to apply unwanted changes to browser settings. This would happen immediately after its configuration files are started on the targeted Mac device.
Trojans Such As OSX.Calisto Trojan
The OSX.Calisto Trojan was detected by Symantec researchers in July. The Trojan is designed to harvest information from infected Macs, take screenshots and also steal passwords and various files from users. The Trojan is designed to uninstall the DMG component on the compromised Mac, and after this is done, it will establish remote access to the compromised computer. Remote access allows the malware operators to perform the following actions:
Enabling remote login; Enabling screen sharing; Adding permissions; Adding remote login to all users; Adding its own account on the device.
Complex Adware Threats Such As OSX.Pirrit
Pirrit Adware (Adware.Pirrit, Adware: Win32/Pirrit) was first discovered in 2014 when it was plaguing Windows systems. The adware was later equipped with a variant specifically created for Mac. Interestingly enough, the Mac variant, OSX.Pirrit appeared to be more complicated than the Windows version, displaying complex malicious behavior. The advanced adware didn’t just flood the victim’s browser with ads but could also obtain root access to the operating system. Despite the complex code, the operators of the adware made a mistake - they left something important (and traceable) behind. They forgot to sanitize the tar.gz archive, one of the archives dropped by OSX.Pirrit. The archive is a Posix format, meaning that it contained all of the file attributes (such as owners and permissions) within the archive in the same form they were created. This helped the researchers locate the user name of the person who created the archive. The analysis led to an Israeli advertising company, TargetingEdge, believed to be behind the OSX.Pirrit’s operations.

About the Author: Milena Dimitrova is an inspired writer for SensorsTechForum.com who enjoys ‘Mr. Robot’ and fears ‘1984’. Focused on user privacy and malicious software, she strongly believes that passwords should be changed more often than opinions. If common sense makes no sense, she will be there to take notes. Those notes may later turn into articles! Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

