
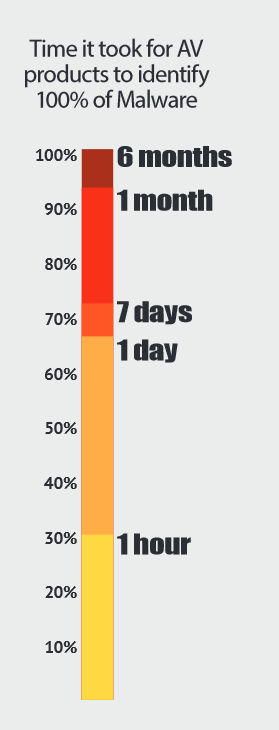
Source: Damballa State of Infections Report, Q4 2014 According to recent research, the average enterprise receives nearly 17,000 malware alerts per week; however, of these alerts, only 19 percent are considered reliable and a mere 4 percent are further investigated by security engineers. As IT teams are bombarded with “noise,” and potentially legitimate threats, Damballa’s latest State of Infections report revealed that Antivirus (AV) products overlooked 70 percent of malware infections within the first hour. After 24 hours, 66 percent of these malicious files were detected, and after one week, a total of 72 percent were successfully identified. It took AV products one month to detect 93 percent of the malicious files analyzed, and more than six months for 100 percent of the malware to be discovered. “In a real world environment, a file would only be scanned once by AV,” read the report. “If the average security team received 17,000 weekly alerts, or 2,430 daily, AV products would have missed 796 malicious filed in day one.”
“Consider the risk associated with that number of infections potentially dwelling undetected inside the network.”
As Damballa CTO Brian Foster explains, the ‘dwell time’ until hundreds of harmful files are identified and addressed could have serious consequences for any enterprise. “If it took you six months to get detected, that’s six months when that hacker has had access to one of your systems,” said Foster. The study analyzed tens of thousands of files submitted by companies for review using the four most commonly deployed AV products, although the names of these specific products were not disclosed. Daniel Schneersohn, APAC VP at Damballa, acknowledges the challenge that IT security teams deal with in order to identify “the needle in the haystack” from the overwhelming amount of alerts. “In the case of Target, for more than three months, they had several systems that were warning them of the infection, but it is just part of the hundreds of alerts the same system was sending them; all of the other ones were false positives,” said Schneersohn. With an infinite number of malware code at attackers’ disposal and only a finite number of skilled security staff on deck, it’s critical that security professionals implement a “forward-thinking breach readiness strategy,” concludes the report. “Enterprises should prevent what they can, and there are millions of known threats that can be identified with AV," said Foster. "But the real threat lies in what AV can't identify."
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

