
Earlier this year, Tripwire commissioned Dimensional Research to ask 500 IT security professionals about their organizations’ key challenges in their cyber security and compliance programs. Tripwire's 2016 Security Challenges Survey covered various areas of interest for infosec folks. For instance, it gauged respondents’ thoughts on the lack of trained personnel in the security field. The skills gap is one of the five greatest challenges to organizations’ compliance and IT operations. As such, it's not surprising that IT professionals were pessimistic about how it affects their organization's security capabilities. In fact, 75 percent of respondents said that a lack of people, a lack of proper experience, or both meant their organizations didn't have enough security personnel to detect and respond to a breach. Additionally, two-thirds of professionals felt the skills gap increased the IT security risks facing their organization. However, not all is lost. To mitigate a shortage of skilled personnel, organizations can automate their security and compliance processes. Tim Erlin, senior director of IT security and risk strategy at Tripwire, explains:
"Opportunities for automation are key to maintaining operational effectiveness when organizations are faced with a skills shortage that won’t be alleviated quickly. Using the tools at hand to prioritize alerts can save precious time in responding to an incident. Putting the right contextual data at the analyst’s fingertips can allow one person to simply get more done in a shorter period of time."
But that's easier said than done. Some organizations don't have the budget to purchase the necessary security tools. Even when other companies do, that doesn't mean they can leverage them to improve their incident response capabilities. Tripwire found out as much in its 2016 Security Challenges Survey.
Leveraging Technology for Breach Detection and Response
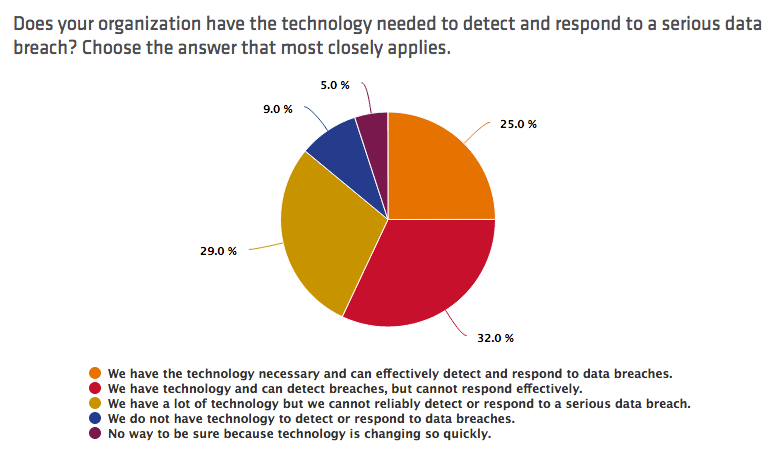
When asked if their organization had the technology needed to effectively detect and respond to a breach, only a quarter of respondents answered in the affirmative. Close to a third (32 percent) said they had the right tools and that they could detect breaches, but they were not confident about their response capabilities. At the same time, another third (29 percent) of IT professionals said they couldn't reliably respond to or detect breaches despite having "a lot of technology."
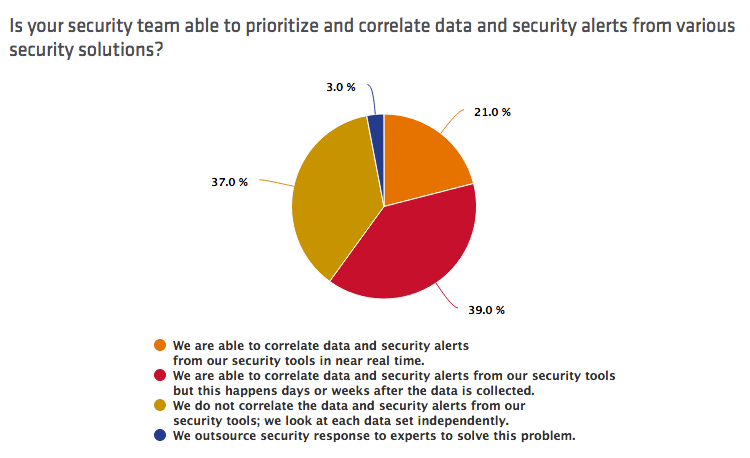
Organizations also lacked the tools necessary to exchange data between different solutions. For instance, almost three-quarters (73 percent) of IT professionals said less than half of their companies' security solutions are sufficiently integrated to exchange data. It's, therefore, no surprise that only one-fifth of respondents (21 percent) said their security teams can prioritize and correlate data and security alerts from various security solutions.
Conclusion
While technology goes a long way towards helping organizations detect and respond to a breach, it's not a catch-all solution. Companies need to make sure their security professionals have the skills necessary to respond to a data breach. They also need to make sure they have detailed processes in place that spell their incident response frameworks. Towards that end, it's important that organizations share information with one another, so that they can infuse their own strategies with others' experiences. As Erlin adds:
"Information sharing is a key defensive strategy for most companies. In order to protect an organization effectively, it’s incredibly valuable to know how other, similar organizations are being attacked or breached."
To learn about how some companies share threat intelligence, check out Tripwire's Technology Alliance Program (TAP).

