
Joomla arrived on the scene in 2005 as a fork of the Mambo content management system (CMS). Downloaded over 91 million times, it has since eclipsed Mambo to become a ubiquitous platform for websites of all sizes. According to last year's Hacked Website Report from Sucuri, which used insights from over 36,000 compromised sites, Joomla is the second most-commonly infected CMS, in between WordPress and Magento. Joomla sites are an appealing target for black-hats, often as a consequence of security misconfigurations, vulnerable third-party extensions and servers running outdated core software. A compromised Joomla site could place your users at risk and lead to irreparable reputation damage. With that in mind, let’s take a look at eight pointers to help harden your Joomla sites against malicious activity.
Eight top tips
1. Keep your Joomla core up to date
First things first, you should check that your instance is running the latest stable build of Joomla. Official releases bring new features and functional bug fixes but most importantly patches for security vulnerabilities. A notification will surface in the Control Panel back-end if an update is available for download. Upgrade packages are also accessible on the Joomla Downloads site. Always back up your site before updating, and familiarize yourself with the instructions if you're handling the process manually.

2. Keep extensions up-to-date
You've updated your Joomla core, but have you checked your third-party extensions? Vulnerable plugins are a common attack vector for adversaries targeting a CMS-based site. Plugins made available on the official extension directory are now required to use the Update System, which will surface a notification in the Control Panel if a new version is available. External developers should write extensions with the Update System in mind. This ensures that the latest patches will always be pulled down from a predefined update server.
3. Remove unused and known-vulnerable extensions
More third-party code means a larger attack surface. Frequently audit the plugins installed on your site by visiting the Extension Manager in Control Panel and remove any that aren't in use. You should also take a moment to review the official Vulnerable Extensions List (VEL). The VEL outlines Joomla extensions with known security flaws for which patches do not exist.
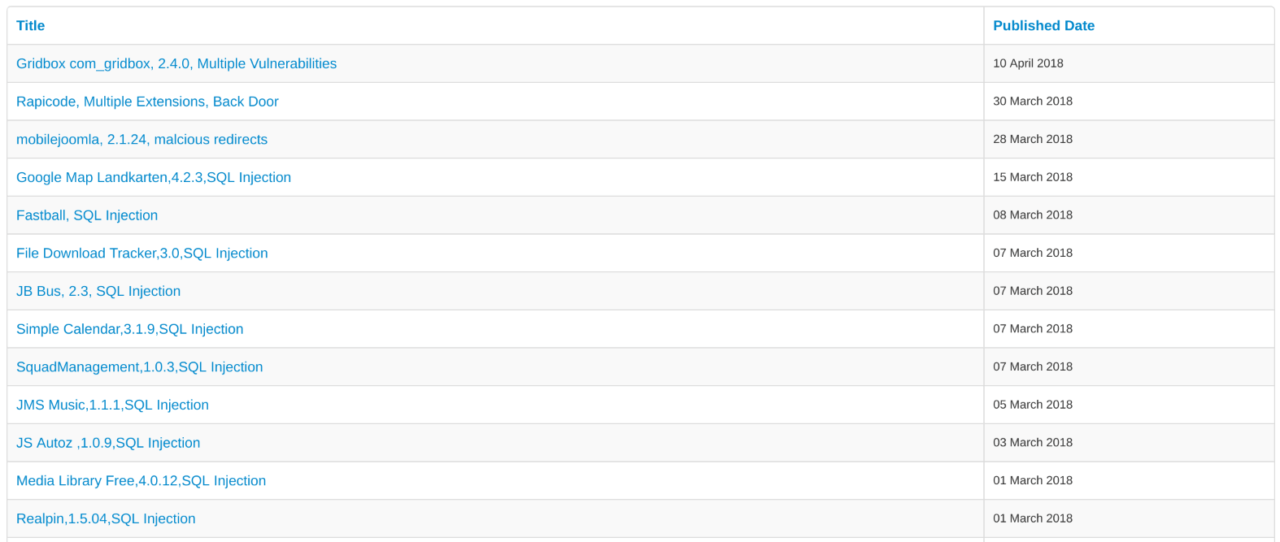
It is imperative that you remove any known-vulnerable extensions from your site. Joomla also provides a JSON feed of the VEL for use in your internal applications.
4. Audit privileged users
By default, Joomla allows three privileged user groups to access areas of the Control Panel:
- Managers — access to content creation features and system information in the backend
- Administrators — access to most administration functions but not Global options
- Super Users — access to all administration functions with complete control
Review your site's privileged user list on a regular basis and check when these users last logged in. Follow the principle of least privilege by ensuring everyone has the fewest permissions necessary to perform their work and nothing in excess.
5. Prevent directory indexing
When a web server can't locate a default file in a directory such as index.php or index.html, it may fall back to displaying a list of the folder's contents. As explained by MITRE, the specific risks and consequences of directory indexing vary depending on which files are listed. With Joomla sites, you could inadvertently disclose information retained by extensions, themes or the server itself. Exposed files may contain credential pairs or debug functionality that an adversary can use to escalate privileges on your site and cause severe damage. To disable directory indexing on Apache, navigate to your Joomla web root and append Options -Indexes to the .htaccess file. On IIS servers, visit "Directory Browsing" in the Manager console and un-tick any enabled check boxes.
6. Enable two-factor authentication
Joomla was the first major CMS to implement two-factor authentication (2FA) as a core feature. With version 3.2 and later, Joomla administrators can visit the User Manager in Control Panel to enable 2FA for users' accounts. The module supports software-based OTP clients (such as Google Authenticator) and YubiKey hardware devices. You can limit two-factor checks to the frontend or backend, or you can require its use on both surfaces. Two-factor authentication is an excellent defense measure which you should take advantage of, especially for privileged users who hold Manager, Administrator or Super User status.
7. Monitor your site for malicious content
Google's Safe Browsing technology proactively examines billions of URLs each day to identify hazardous websites serving malicious content. Check the status of your Joomla site on a regular basis and take immediate action if issues are detected. When investigating a potentially compromised website, use the on-demand VirusTotal URL scanner to narrow down the manner of infection.
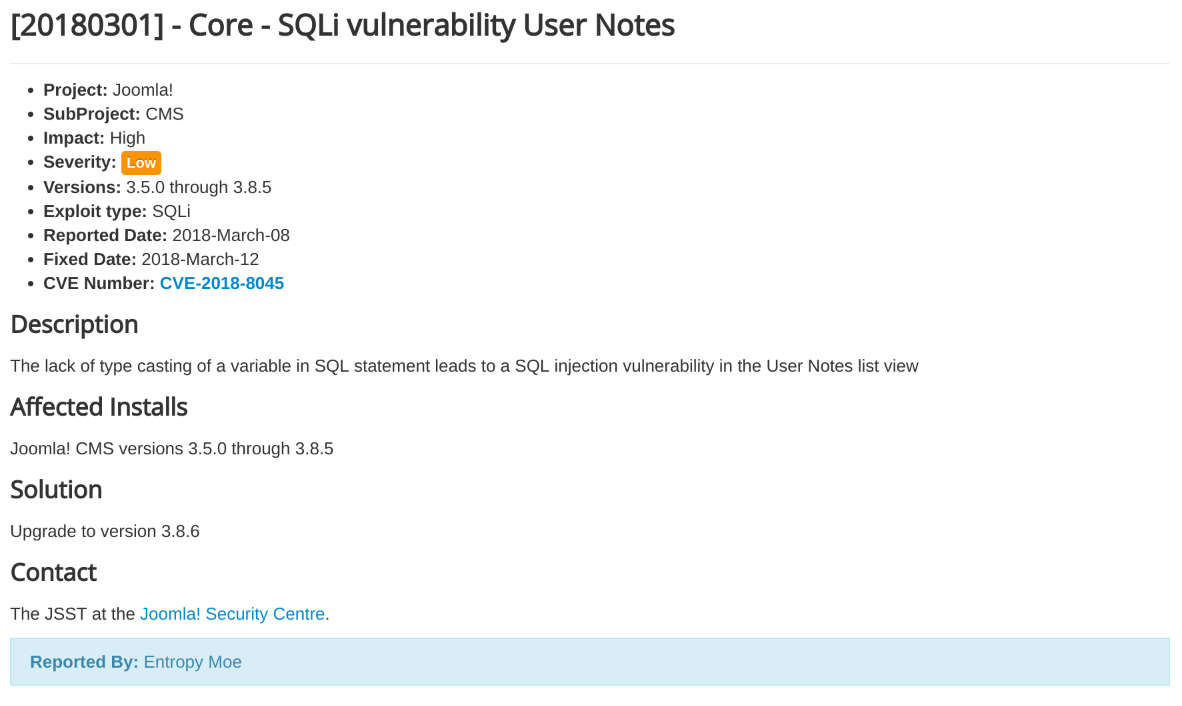
8. Subscribe to Joomla's official Security Announcements
Joomla publishes vulnerability advisories on the Security Announcements page. Subscribe to email notifications via FeedBurner or add the RSS feed to your reader of choice to stay up-to-date with resolved issues in the core software. Each advisory contains a straightforward description, impact rating and remediation details to help keep your Joomla site protected.
Further reading
- Joomla Security Checklist
- Joomla Security and Performance FAQs

About the Author: Yasin Soliman is a security analyst from the UK with an interest in web application testing and red team operations. Writing on cybercrime and emerging technologies, Yasin lives and breathes information security. You can find him on Twitter at @SecurityYasin. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

