
For years, computer criminals have been targeting unsuspecting web users with post office email scams. This particular method of attack consists of a fake email in which a recognizable postal service notifies the recipient that it has failed to deliver a package to their address. The email subsequently asks that the recipient pick up the package themselves and provides a link by which they can arrange to do so. When the recipient clicks on the URL, however, they are redirected to a page that installs malware--in most cases, crypto-ransomware--onto their machines. Heimdal Security notes that people tend to fall for this type of scam because by nature they trust familiar institutions such as the post office. The fact that attackers localize their fake emails, such as by customizing the name of each postal service and by correctly translating the email's text according to a specific country's language, only enhances the scams' success rate. This explains why we saw at least two campaigns, one based in the United Kingdom and one based in Denmark, that leveraged post office email scams in an attempt to infect users with some variant of Cryptolocker ransomware earlier this year. Unfortunately, computer criminals are always looking to exploit people, which means that no time of year is off-limits. In fact, it stands to reason that attackers prefer some seasons such as the holidays over others, for they know that during those periods users are less concerned about their own security and more concerned about convenience, shopping deals, and a package they might have received in the mail. It is therefore unsurprising that a post office email scam has recently been observed targeting PostNord customers with Cryptolocker2 ransomware. Heimdal Security explains in a blog post that the fake email employs one of three subject lines based upon whether the recipient lives in Denmark, Norway, or Sweden. It also comes with a dynamically generated folder, which enables the attackers to customize the contents of each message based upon the target's country.
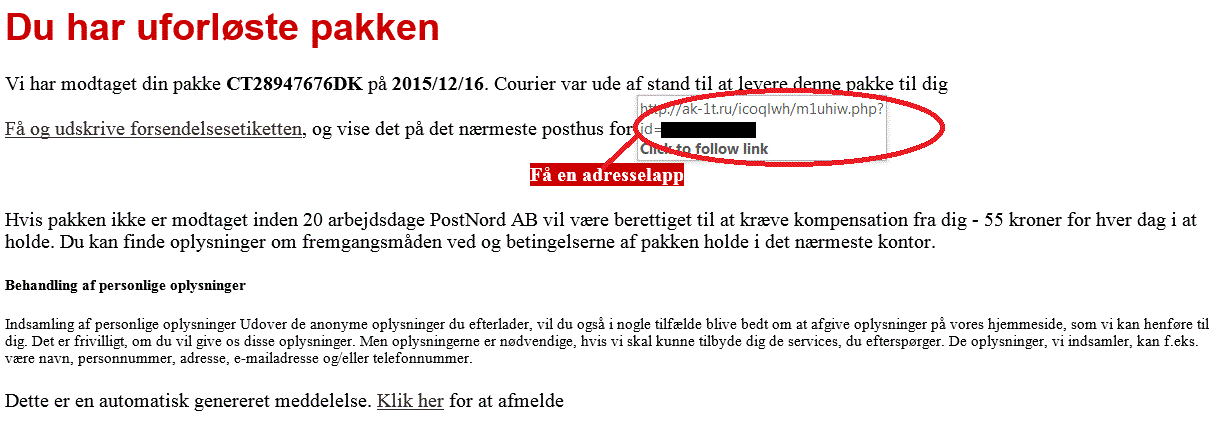
Source: Heimdal Security This folder's contents in part appear as follows: 3gjDGp2tX6Sx.js 4VrRa08A.png 5Gb4J9H.gif 5R9BcOwPKZ7b.js 5sj0l3D4YmLn.png C0QDbBRoGF.png JE7BTZispdlf2O.js NZbfEQXp8z4k2m0T.css ODpS2lYBN1.css WDvk6JwXx7FQ4.png mJZrShFWaYOsGoq9.html ozpb3w.png u6inWYt9EMr.php uEn23lx.html uQ2eTKl.png
"Upon dissecting the payload, we saw that it’s delivered as a zip file that can be delivered only once," Andra Zaharia of Heimdal observes. "As retaliation, cyber criminals have blocked several IP addresses that Heimdal uses in order to hinder our analysis. However, we managed to see that the payload that delivers the Cryptolocker2 infection is delivered only to IP addresses in Scandinavia."
The attackers are making use of three domains in particular--"Romashka-plus [.] ru", "gold comfort [.] ru", and "solid parquet [.] ru"--as part of their spam campaign. These domains each launch an infection cycle that terminates with the file "info_ [5 random numbers] .zip", whose binary is disguised as a PDF and which is loaded from "downloader.disk.yandex [.] com". Upon completion, the file loads up Cryptolocker2, which encrypts all of the data stored on your computer and on the cloud apps synced to your PC. The ransomware also harvests victims' email addresses and sends them to a C&C server for use in future spam campaigns. Heimdal recommends that businesses protect themselves against this threat by blocking several word combinations that appear in the spam message and that would not otherwise appear in legitimate emails sent from Danish speakers. Ordinary computer users can learn how they can protect themselves against ransomware by clicking here. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

