
Researchers have identified a new Trojan that targets mobile banking apps with customized phishing pages in an attempt to steal users' login credentials. According to a blog post recently published by security firm Symantec, the Trojan, which has been named "Android.Fakelogin", is targeting primarily Russian mobile users. The malware comes in the form of a fake app, and upon download, it requests administrator permissions, including the ability to access a list of accounts, end background processes, and read a user's call log. If the Trojan is granted these permissions, it downloads a list of banking applications from its command-and-control (C&C) server and saves it as a preference file, at which point it then checks to see if any of the apps on its list are installed on the infected device.
"The server responds with a phishing page that mimics the appearance of the targeted app," explains Symantec. "The flexibility afforded by this cloud-based approach means that the malware does not need to be updated each time the targeted banks change the look or format of their mobile banking apps."
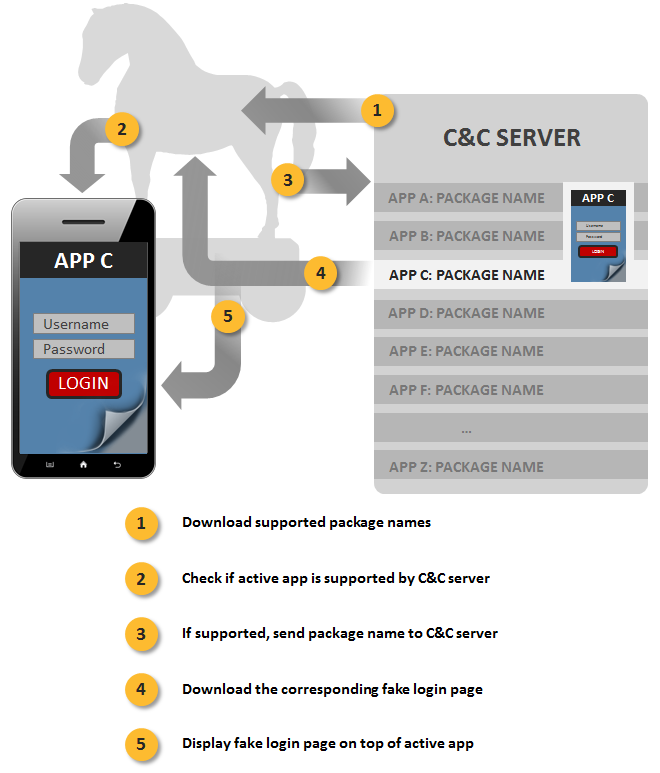
Android.Fakelogin steals login credentials from compromised devices by leveraging cloud-based logic from its C&C server (Source: Symantec)
The blog post goes on to state that Android.Fakelogin uses code obfuscation, a common evasive behavior in malware, to avoid detection and make reverse engineering difficult. It also does not require the user to launch it once it has successfully infected a device.
Symantec recommends that app developers introduce additional layers of authentication into their banking apps, especially when a user approves a transaction or modifies sensitive personal information. In the meantime, mobile users are urged to install a mobile security solution on their phones, keep their software updated, and download apps only from trusted sources.
Android.Fakelogin is just one of many banking Trojans in existence today. Recently, the Federal Bureau of Investigations helped take down part of a botnet responsible for disseminating Dridex, a well known banking Trojan. However, researchers have since confirmed that parts of the botnet might still be functioning.

