
Security researchers discovered an attack campaign that abused fears surrounding the global coronavirus outbreak to deliver the Remcos RAT. Yoroi Security detected the attack campaign when its threat intelligence activities uncovered a suspicious artifact named “CoronaVirusSafetyMeasures_pdf.” In their analysis, Yoroi's researchers determined that the file established a TLS connection with file sharing platform “share.]dmca.]gripe” potentially in a bid to evade detection by next-fen firewalls. The attack leveraged this connection to download a file that wrote two additional files named “filename1.vbs” and “filename1.exe” to the “C:\Users\<username>\Subfolder” system directory. The VBS script served as a launchpad for the executable, which established persistence by setting up a registry key.
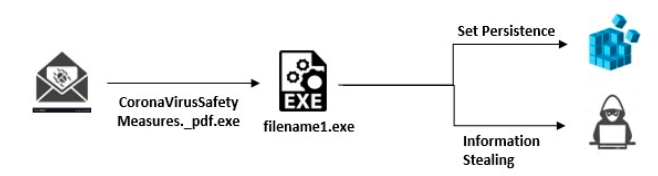
The malware attack chain (Source: Yoroi Security) The campaign then proceeded with its malicious activity, as described by Yoroi in its research:
Then, the malicious code stores sensitive information gathered from the monitoring of user keypress in a file named “logs.dat”, placed in the “%AppData%\Local\Temp\onedriv” directory. Different from the default Remcos working directory. Finally, all the loot is sent to the remote command and control hosted at 66.154.98.108, operated by “Total server solutions LLC”, an US hosting provider operating since 2012.
Researchers at Yoroi analyzed this network communication and found a “|cmd|” delimiter. This discovery them to conclude that the attack campaign's final payload was a customized build of Remcos. After discovering the RAT family back in February 2017, Fortinet spotted a phishing campaign using several new spam samples of Remcos in October 2019. This isn't the only instance in which digital attackers have abused the coronavirus as a theme for their attacks. In early 2020, IBM X-Force spotted a campaign that tricked Japanese users with fake warnings of new coronavirus cases in their area into enabling macros within a weaponized Microsoft Word document. Upon execution, those macros leveraged PowerShell to install Emotet on their computers. It's likely that digital attackers will continue to capitalize on fears surrounding the coronavirus, especially after the U.S. Centers for Disease Control and Prevention (CDC) said that the disease will almost certainly spread within the United States, as reported by the New York Times. Yoroi did not uncover the vector that attackers leveraged to deliver "CoronaVirusSafetyMeasures_pdf." Its researchers reasoned that a phishing email was likely to blame. With that said, organizations should take steps to protect themselves against phishing campaigns. They can do so by familiarizing their workforce with the most common types of phishing attacks in circulation today.

