
A new Netflix phishing attack leverages fake emails from the streaming service to trick users into handing over their credit card credentials. The attack starts when a user receives an email from what appears to be Netflix warning them that they need to update their membership information.
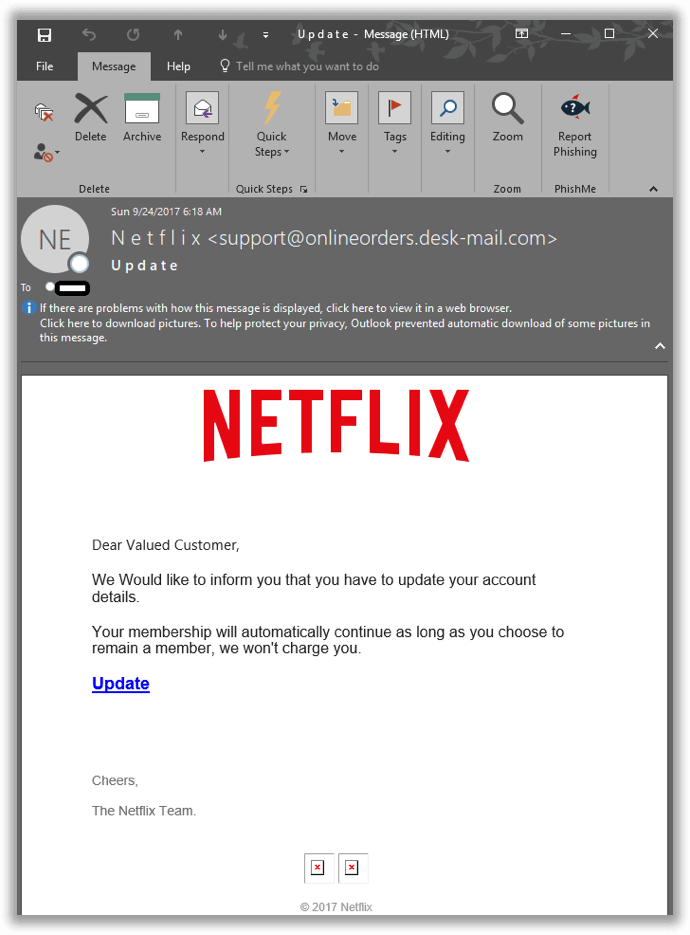
An example attack email received in the Netflix phishing campaign. (Source: PhishMe)
"Dear Valued Customer, We Would like to inform you that you have to update your account details. Your membership will automatically continue as long as you choose to remain a member, we won't charge you. Update Cheers, The Netflix Team."
You can see that the sender email address, support@onlineorders[.]desk-mail[.]com, has nothing to do with Netflix. So it's not surprising that clicking on the "Update" link leads somewhere other than the streaming service. In fact, it directs the user to hxxp://see-all[.]norafix[.]com/, a location which immediately redirects them to the subdomain hxxp://account[.]norafix[.]com/ch/customer_center/customer-IDPP00C274/js/?country.x=&locale.x=en_. That page prompts the user to enter in their Netflix credentials followed by their payment card details.
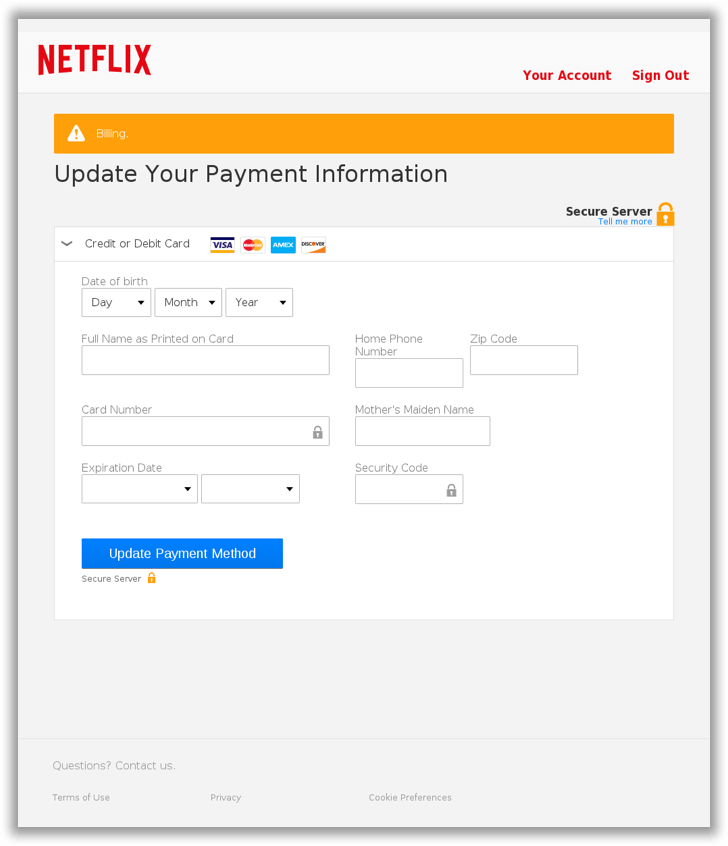
The Netflix phishing scheme's credit card info-stealing page. (Source: PhishMe) Once it's succeeded in stealing that information, the scam confirms that the user's account is now updated. It then provides them with a link to Netflix's actual homepage. So what happens then? Well, the attacker could abuse the user's stolen credentials to gain access to Netflix content for free. They could also leverage the credit card information to make fraudulent purchases. But they could also reuse the stolen login details in an attempt to gain access to some of the user's other accounts. PhishMe senior threat analyst Chase Sims elaborates on this scenario:
"So now the attacker hopes that you reuse the same password for your personal email account or, if the attacker is very lucky, for your work email account. In either case, they can now reset passwords for various other online services—banking, healthcare, social media—to pivot and carry their attack forward. "One reason this tactic could succeed: a lot of companies might not enforce two-factor authentication for their single-sign-on services, which means reused credentials might be a skeleton key for multiple corporate services."
This isn't the first Netflix phishing scheme to surface on the web, and it certainly won't be the last. With that in mind, users should make an effort to familiarize themselves with some of the most common social engineering ruses out there so that they can spot a potential attack. They should also exercise caution around suspicious links and email attachments, verify the legitimacy of a web domain before entering in any login or financial information, and enable multi-factor authentication on any and all accounts that allow it.

