
Malware is one of the most dangerous classes of computer threats facing users today, and as a risk category, it is growing in sophistication. First, malware is now more difficult to detect. In an effort to stay one step ahead of security researchers, authors of malicious software are integrating evasion techniques, including environmental awareness and obfuscation, into their code. These techniques enable malicious programs to remain undetected while infecting a victim's machine. Second, individual samples are pushing the limits of what malware can do. For example, Rombertik, which is now known to be a newer version of the underground crimeware kit Carbon FormGrabber, has the ability to overwrite an infected system's Master Boot Record and restart the computer, effectively rendering the machine unusable. At the same time, many crypto-variants of ransomware are able to encrypt files or entire web databases, at which point in time they demand ransom payments in exchange for the decryption keys. Malware is known to target victims' information. However, we would be remiss to assume that that is the aim of all malicious programs. Indeed, as a new report published by the Digital Citizens Alliance reveals, attackers are using Remote Access Trojans (RATs) not to steal their targets' data but to hijack their computers and in some situations sextort their victims.
Source: Digital Citizens Alliance In their report entitled Selling "Slaving": Outlining the Principal Enablers from Pushing Malware and Put Your Privacy at Risk, the authors at the Digital Citizens Alliance explain that approximately 70 percent of malware consists of Trojans, the most easily deployable of which is the Remote Access Trojan. RATs are commonly used as the payload of spear phishing emails, a threat which along with normal phishing attacks saw the greatest increase in malicious DNS creation in the second quarter of 2015. Just as phishing tactics have a proven track record, RATs make up a tried and true malware subset that comes with many advantages. First and foremost, Remote Access Trojans are inexpensive and simple to deploy. As the report explains, well-known RATs such as Dark Comets and Blackshades sold for only between $50 and $250 back in 2013. The source codes of these and other samples have since been leaked online, which has led to a drop in price to between $10 and $50. These prices reflect the fact that an RAT is a valuable tool for attackers who do not have the requisite technical skills to use more sophisticated techniques.
“Whether it’s the family computer or the office network, most have the same vulnerability, and when people say this is a very sophisticated attack, it’s really not,” said Gary S. Miliefsky, who was a founding member of the Department of Homeland Security and is now Chief Executive Officer of the mobile app security firm SnoopWall. “It’s about patience.”
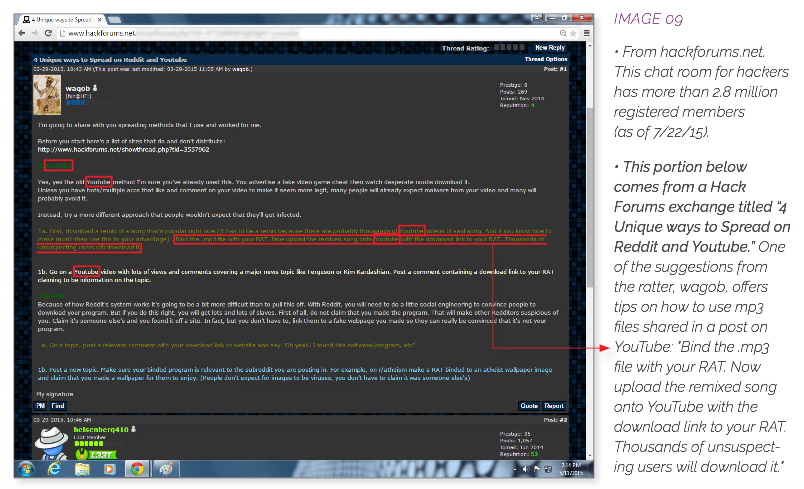
It is also about customizability. As Miliefsky goes on to explain in a SnoopWall paper, 2015: The Year of the RAT - Threat Report, attackers can use RATs to accomplish a number of tasks, including changing a victim's Windows registry, destroying the CPU by overclocking, and for the purposes of this article, seizing control of a target's computer and webcam. Some novice attackers and script kiddies might not know how to unlock these and other functionalities of a particular RAT. If this is the case, those attackers can visit a variety of forums and websites that provide tutorials on the subject. For instance, the Digital Citizens Alliance found that Hack Forums has 15 million posts on RATs. Meanwhile, YouTube has an estimated 30,490 instructional videos on how to use a number of different Remote Access Trojans, 38% of which display ads from reputable advertisers, including Boeing and the New York Yankees. These revenues are then split between Google, the advertisers, and the criminals who upload the videos.
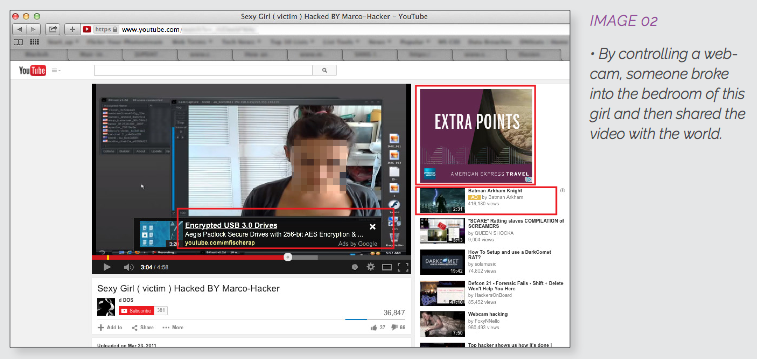
Source: Digital Citizens Alliance In addition to providing tutorials, YouTube also enables would-be attackers to download tools and to watch videos of successfully deployed RATs. This latter category oftentimes consists of videos of young boys and girls alone in their rooms who are completely unaware that they are being watched by thousands of viewers. Once a victim has been successfully infected, they are essentially at the mercy of their attacker. Cassidy Wolf, former Miss Teen USA, found this out first hand after she was "ratted" in 2013.
"One night I had an email sent to my computer anonymously threatening me, giving me three options to do whatever he asked," Wolf told CNNMoney. "The first one being to Snapchat him, the second one being to send him 'better quality' photos, and the third one being to video [myself] for five minutes doing whatever he asked," namely sexually explicit acts.
Cassidy did not submit to her attacker's demands, and he--a classmate at her local high school--was fortunately arrested and jailed for his crimes. But Cassidy's story is not unique. Given their inexpensiveness, their lack of sophistication, their customizability, and the expectation that they will begin targeting mobile platforms in greater force in the coming years, RATs are a persistent threat that will continue to target unsuspecting victims like Cassidy. That is not to say that law enforcement has not had some success in bringing down RATs. For example, an international legal operation arrested 100 individuals last summer who are believed to have helped propagate the Blackshades RAT. But as Scott Aken, a former FBI "cyber agent" explains, there are simply too many Remote Access Trojans in existence for law enforcement to bring down all of them.
“Law enforcement just isn’t equipped at this stage of the game to keep up with this stuff as fast as it’s changing," Aken said. "People aren’t trained enough. They don’t have the manpower to go after the people that want to abuse the technology that was originally meant for good and is now being used for evil.”
Acknowledging these limitations, the onus for removing these RATs falls on sites such as YouTube. At this time, YouTube generally removes content if and when it is flagged by users. But perhaps YouTube should do more. Perhaps it should follow the lead of Google, which earlier this year established a manual team of human analysts to patrol its Play Store for malware, and create its own team of reviewers to remove these types of videos. Ultimately, it might take a human touch to protect our children from being victimized by these types of attacks. In the meantime, users are urged to not open suspicious links, to protect their web accounts with strong passwords, and to activate some form of AV software on their computers. To read Digital Citizens Alliance's report in full, which includes further recommendations on how you can protect yourself against RATs, please click here. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

