
Researchers have confirmed that a variant of the BlackEnergy malware was behind a power outage that occurred around Christmas Eve last year. Reuters reports that the Western Ukrainian power company Prykarpattyaoblenergo reported on outage on December 23rd that affected an area including the regional capital Ivano-Frankivsk. A subsequent investigation revealed that a variant of the BlackEnergy malware had caused "interference" in the working of the company's systems, which led to the power interruption. The investigation also found that the malware had been injected into the networks of two other utilities, though neither had reported any service problems. In a post on welivesecurity, ESET researchers Robert Lipovsky and Anton Cherepanov explain that BlackEnergy used Microsoft Office documents containing malicious macros in these particular attacks.
"The attack scenario is simple: the target gets a spear-phishing email that contains an attachment with a malicious document," the researchers observe. "The document itself contains text trying to convince the victim to run the macro in the document. This is an example where social engineering is used instead of exploiting software vulnerabilities. If victims are successfully tricked, they end up infected with BlackEnergy Lite."
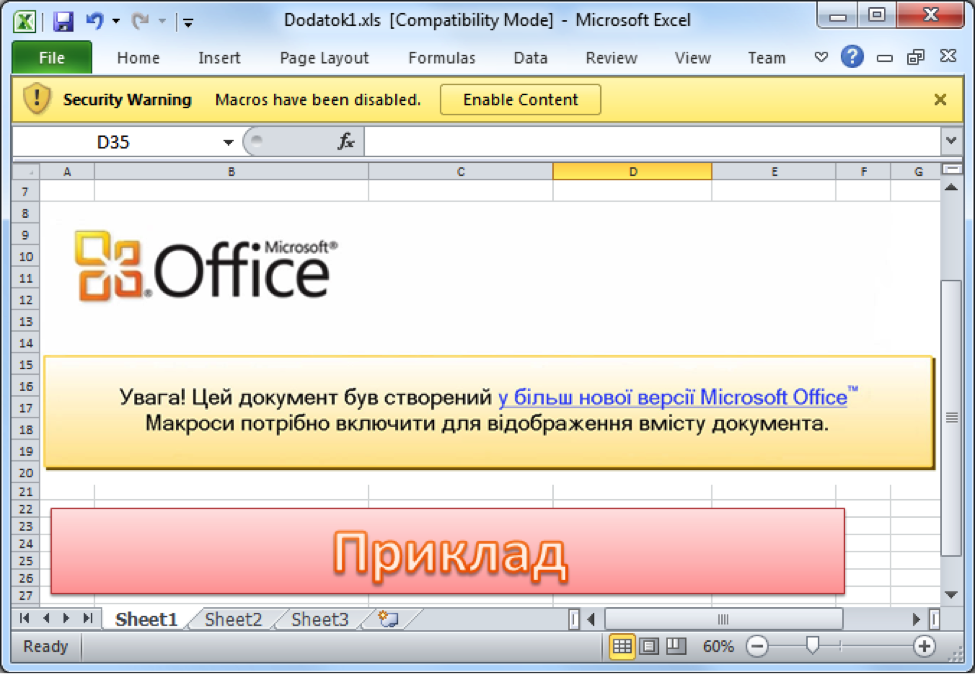
A screenshot of a malicious document used in the BlackEnergy campaigns (Source: ESET)
Once the infection process is complete, victims are vulnerable to a variety of plugins that the modular trojan is capable of deploying against them. These include a destructive KillDisk component, which is designed to overwrite documents based upon their file extensions and to render the OS unbootable, as well as an SSH server called Dropbear SSH, which allows the operators of the malware to return to the compromised network whenever they want.
Lipovsky and Cherepanov's findings mark a dangerous precedent at a time when governments including the United States are growing increasingly concerned about attackers targeting their critical infrastructure.
"It's a milestone because we've definitely seen targeted destructive events against energy before—oil firms, for instance—but never the event which causes the blackout," John Hultquist, head of iSIGHT's cyber espionage intelligence practice, told ArsTechnica. "It's the major scenario we've all been concerned about for so long."
As noted by The Register, BlackEnergy has been around since 2007. Since then, it has evolved from a distributed denial-of-service (DDoS) attack malware into a modular trojan that has leveraged unknown vulnerabilities to attack targets in the Ukraine and Poland, leading some to suspect that the authors of BlackEnergy are Russian in origin. Security researchers have resisted firmly attributing the malware as state-sponsored, however, writes InfoSecurity Magazine. Utilities are encouraged to learn from the case of Prykarpattyaoblenergo and implement measures that can help protect themselves against becoming infected by BlackEnergy and similar malware.
"Every piece of malware requires an infection vector," Tim Erlin, Director of Security and Product Management at Tripwire, informed SCMagazine. "Keeping systems hardened and patched, and training employees to defend against phishing, are the best anti-malware defences."
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

