
The Blank Slate attack campaign is pushing out one of two ransomware to unsuspecting Windows users via Microsoft-themed malspam. An attack begins when a user receives a malicious spam ("malspam") email message. As in previous instances of Blank Slate, the email's subject line doesn't give away the attack. It incorporates seemingly random numbers and letters, perhaps in the hope the recipient will be curious enough to open the email. If a user opens up Blank Slate malspam mail, they usually don't see any message content.
Example of a typical Blank Slate email from Wednesday 2017-06-28. (Source: ISC) But that's not the case in this phase. These new emails come with a message warning the recipient that Microsoft has detected suspicious activity on their accounts. The message then instructs the recipient to open an attached document containing further instructions.
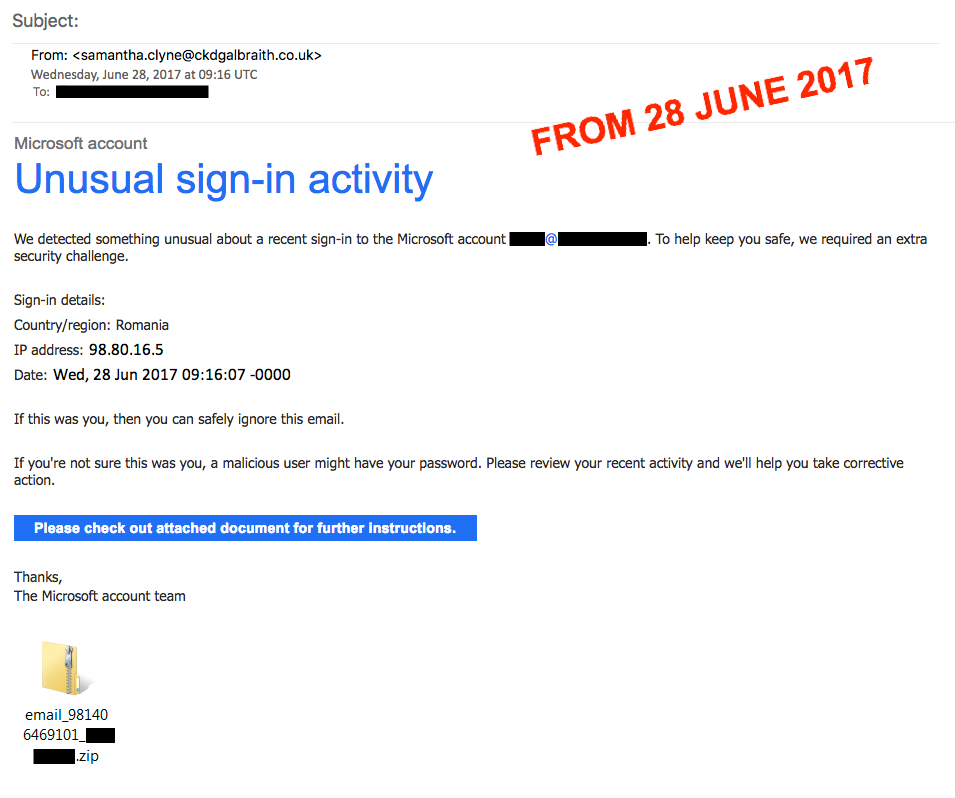
Microsoft-themed Blank Slate email from Wednesday 2017-06-28. (Source: ISC) Brad Duncan, an information security handler at SANS' Internet Storm Center (ISC), has been tracking Blank Slate for months. He explains what happens if a user opens one of Blank Slate's .zip attachments:
"As usual, the zip attachments are double-zipped, and they contain a .js file designed to infect a Windows computer with ransomware. I saw two types of .js files. One was about 9 kB in size, and it ran the downloaded ransomware from the user's AppData\Local\Temp directory. The other type of .js file was about 31 kB in size, and it ran the downloaded ransomware from the user's AppData\Roaming\Microsoft\Windows\Templates directory."
Specifically, this campaign is know for running one of two types of ransomware: Cerber and GlobeImposter. Binaries for the threats usually download from a domain name ending in .top. Whichever ransomware strikes then proceeds to encrypt the user's files before demanding a ransom. To protect against this evolving campaign, users should exercise caution around emails with subject lines that contain random numbers and letters. They should also think twice about clicking on suspicious links and email attachments. For added protection, they should run an anti-virus solution on their machines and back up their data regularly.

