
This is a more technology-based continuation of KGW Portland's story that it published discussing what 86 convicted burglars looked for in target selection. My aim is to add aspects of both Social Engineering and Open Source Intelligence (OSINT) into this to attempt to help raise awareness. The purpose behind the anonymous questionnaire, which was distributed to inmates in Oregon Department of Corrections facilities, was to allow those who have done the deed to help others protect against it. This is similar to Frank Abagnale of Catch Me If You Can, who is now working for the FBI in identity theft and check forgery cases. The questionnaire focused on how the burglars entered homes, picked targets, surveilled houses, and what ultimately deterred them. Things like signs, cameras and dogs were all on the list. The questionnaire can be viewed here.
OSINT Angles
To apply the open source intelligence (OSINT) angle to the questionnaire, think of this: everything external to your house is open (assuming you do not live on a large property with the home centered on it). The same goes for your car(s). From the street, it is fair game.
Car Stickers
Those pesky stickers we see on cars, the ones of stick figure families, are vectors of OSINT gathering about you and your family. Stickers that say things like "My heart is in Iraq/Afghanistan" are also of value to would-be attackers. Stickers announcing your children's basketball team name can release the same information. Here is an example:

A back windshield that contains stickers What I infer from this image as a Social Engineer:
- The owner has pets; several of them. This is worth noting when scoping the house for intrusion.
- The owner has several children and has lost a couple. It is something that could be used to build a social engineering pretext for communication and exploitation.
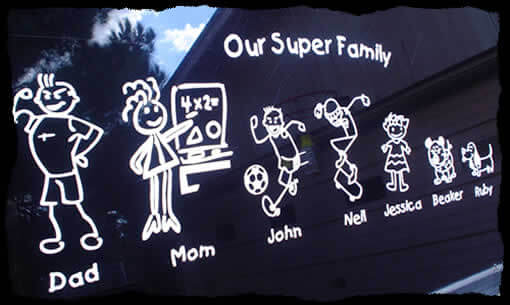
Another Stick Family What I infer from this image as a Social Engineer:
- Dad likes to work out, and Mom is a school teacher. Non-holiday weekdays are a lucrative target. An aspiring thief can also be used to build pretexts for phishing and vishing campaigns.
- John plays soccer and/or other sports. Depending on his age and whether he is on an organized team, he may practice 2-5 days per week after school.
- Neil skateboards. You may find him at the skate park after school.
- Jessica is too young to watch herself. She likely has a babysitter, which could be John, Neil, or someone else.
- Beaker and Ruby do not seem to be large or aggressive breeds.

Sports Stickers can be dangerous. What I infer from this image as a Social Engineer:
- We know the kid's name and team. Most teams in 2016 have websites and/or social media, mostly Facebook pages.
- We can use this to infer the child's age range and team schedule. This gives attackers an idea of when to strike since they can reasonably infer the house is empty.
- Depending on the team, this can also provide information about wealth levels based on the travel schedule, team, etc. that can help attackers further profile the targets.
Baby On Board

Baby on Board can help or hurt you from the OSINT perspective. I will only briefly touch on this. A baby on board sign on a car could elicit one of two responses. It could stop a criminal from targeting the house for fear of waking the baby, or someone truly nefarious could decide to threaten the baby or kidnap the baby as a hostage.
Security System Signs
The respondents of the questionnaire talked about their opinions of security systems and their signs. The general consensus was split between deterrence and the ability to disarm. Understanding that I can add little to nothing about deterrence, I would like to pose this from the perspective of disarming and deception. From the perspective of the attacker or thief, they are looking at who the security system carrier is. This allows them to research ways to bypass and defeat the system. A simple way to further challenge the burglars via deception is to use a sign that is not that of your carrier. If you use Comcast, get an ADT or Brinks sign for example. While there are overlaps in defeating the systems, it would be a surprise to the thief. Other methods to complicate this are below:
- When selecting a system, choose a variety of networking methods if possible. The burglar may attempt to sever phone and/or cable lines to kill the connection. Having cellular and/or reciprocity with your neighbor (via their wireless network) can provide the resilience that burglars are not expecting (assuming they're not doing homes in parallel).
- Use real and dummy cameras. Have them cover the same area. If the burglar decides to disable one, they are now conflicted as to which one they should shut down (assuming they see both).
- Consider installing a wireless doorbell (with camera) like Ring. This is a doorbell that can be rung, but it's also a motion sensing camera.
- Whether you have dogs or not, consider some signs and/or magnets showing your love for your (insert aggressive breed [i.e. Rottweiler, Doberman Pinscher, Pitbull, etc.] here). Having a large dog is to your benefit per the questionnaire, but just making the attacker wonder if there is such a dog may do the trick, as well.
Social Media
This is the pinnacle of OSINT gathering platforms. I will discuss some of this a little more in-depth below. What you post and how you post it can help cyber-enabled crooks paint a good picture of you and your routine. Obviously, all users of social networks and social media should have some level of cognizance about operations security (OPSEC). This is the thought that they should not make everything public and that they should scrutinize what they share and with whom they share it with. Social media platforms can give attackers some of the following examples of information:
- Information about (including pictures of) you, your family and your children.
- Information about your schedule, as well as your children's sports and activities schedule.
- IP Address or GPS Latitude and Longitude from where you posted. (See my Kim Kardashian post for more information).
- Enough information to build an effective pretext (character) to get close to you.
Miscellaneous Tools and Ideas
An awesome tool that I have found to collect and interpret OSINT data is the Advanced Recon Framework. A specific tool worth mentioning in this post is Melissa Data Property Viewer. This allows would-be thieves to follow vehicles then get their address and possibly contact the occupants using various pretexts. Note: This appears to only work in the USA.
Advice and Conclusion
There is little you can do to prevent entities from gathering OSINT on you, and even less can be done to prevent the creation of OSINT. The best thing that you can do is to be aware. Be cautious of any unsolicited visitors, emails, phone calls, etc. Think before you speak or respond. Attackers may be building a profile on you and yours to exploit you for their gain. Minimize what you tell people yourself. Be polite yet brief in any unsolicited conversations in-person, online, or otherwise. Do not provide too many details about anything. Understand what you're telling people in your use of sticks and adornments. Most of all, remain vigilant, and if it seems too good to be true, it probably is.

About the Author: Joe Gray has worked as a Systems Engineer, Information Systems Auditor, Senior UNIX Administrator, Information Systems Security Officer, Director of IT Security, and Enterprise Security Consultant. He is currently employed as an Enterprise Security Consultant with Sword and Shield Enterprise Security in Knoxville, TN. He also maintains the Advanced Persistent Security Blog and Podcast. Joe is also in the SANS Instructor Development pipeline and will be teaching SANS Security 504: Hacker Tools, Techniques, Exploits and Incident Handling. Joe holds the (ISC)² CISSP-ISSMP, GIAC GSNA, GCIH, CompTIA Security+, CompTIA Network+, and CompTIA A+ certifications. You can find him on LinkedIn here: linkedin.com/in/billyjgrayjr This post is meant to educate readers about how they may be inadvertently diving information to would-be thieves about them, their families, and their houses. These are from my own perspective. While I make every effort to be thorough and hit every aspect, there are times that I inadvertently omit things or skip them due to scope, time, length or applicability. Email any questions you have about this or any other topic to [email protected] The opinions expressed in this post do not necessarily reflect those of Joe's employers: past, present, or future. While I am a security professional, I am not your security professional. The data included in this post is sound by current industry parameters, your mileage may vary. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

