
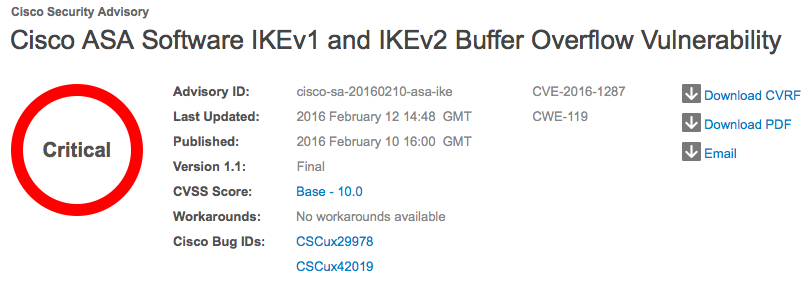
Cisco has patched a 'critical' buffer overflow vulnerability affecting the Internet Key Exchange (IKE) implementation in Cisco ASA. On Wednesday, the multinational technology company published a security advisory for CVE-2016-1287. First discovered and reported by researchers at Exodus Intelligence, the vulnerability could lead to a complete compromise of ASA devices connected to the Internet. Exodus Intelligence has released a detailed blog post discussing the issue and it’s exploitation.
"The algorithm for re-assembling IKE payloads fragmented with the Cisco fragmentation protocol contains a bounds-checking flaw that allows a heap buffer to be overflowed with attacker-controlled data," Exodus researchers David Barksdale, Jordan Gruskovnjak, and Alex Wheeler explain. "A sequence of payloads with carefully chosen parameters causes a buffer of insufficient size to be allocated in the heap which is then overflowed when fragment payloads are copied into the buffer. Attackers can use this vulnerability to execute arbitrary code on affected devices."
Successful exploitation of this vulnerability, which affects Cisco ASA software if the system is configured to terminate IKEv1 or IKEv2 VPN connections, could lead to a full compromise of the affected system.
Not surprisingly, the SANS Internet Storm Center (ISC) has noted a large spike in active scanning for UDP Port 500, a channel through which an exploit would likely arrive, since the vulnerability went public. It is therefore imperative that sysadmins move quickly. According to Cisco, Cisco IPS Signature 7169-0 and Snort ID 36903 can detect attempts to exploit this vulnerability. One can also test to see if a device is vulnerable by checking the running crypto maps: ciscoasa# show running-config crypto map | include interface If a crypto map is returned, the device is vulnerable. Tripwire will release ASPL-657 on Wednesday, February 17th, which will include Vulnerability ID #224098 to detect this issue within Tripwire IP360. This detection is also available via the Tripwire Customer Center to those interested in scanning early. In the meantime, Cisco has released software updates that address the vulnerability. It is recommended that system administrators implement those fixes sooner rather than later. News of this patch follows a fix for vulnerability in the code that handles the reassembly of fragmented IPv4 and IPv6 packets of Cisco IOS XE Software for its ASR 1000 Series Aggregation Services Routers back in August of 2015.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

