
A Gmail phishing campaign is clever enough to have almost tricked or successfully fooled multiple technical users. The attack, which other contributors to The State of Security have spotted, begins when a Gmail user receives an email. Oftentimes, the message comes from someone they know whose account has already been compromised. The email appears to contain a PDF attachment. In actuality, the "attachment" is an embedded image designed to fool the user into clicking on it. Doing so opens a new tab in the user's browser, where they are prompted to sign into their Gmail account using a legitimate-looking sign-in page.
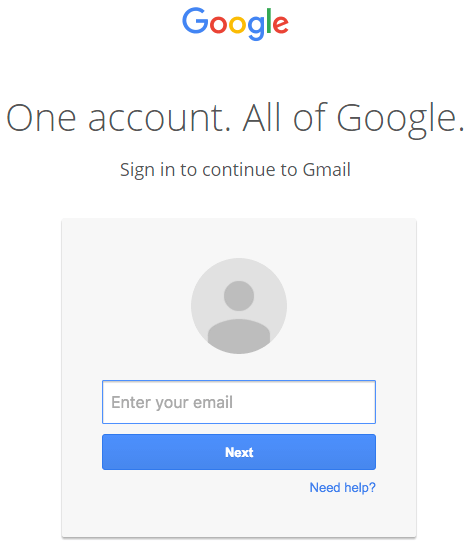
Upon entering their credentials, attackers can in most cases gain access to the victim's Gmail account. One victim explains what happens next on Hacker News:
"The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list. "For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team."
Fortunately, this scam isn't undetectable. The location bar uses "data URI" to include a complete file (the phishing page) in the browser. You can tell by the fact that the location lists "data:text/html," before "https://".
But there's a problem. The phrase "accounts.google.com" is clearly visible in the file's address. This tactic is enough to fool most non-techie recipients and has almost tricked even some technical users. https://twitter.com/tomscott/status/812265182646927361 Others said they've not been so lucky in blogs or comments. To its credit, Google has grown wise to this phishing scam and has instituted measures designed to protect Chrome users. Wordfence's Mark Maunder, who originally came across the scam, elaborates on that point in a blog post:
"Chrome has resolved this issue to my satisfaction. Earlier this month they released Chrome 56.0.2924 which changes the location bar behavior. If you now view a data URL, the location bar shows a “Not Secure” message which should help users realize that they should not trust forms presented to them via a data URL. It will help prevent this specific phishing technique."
To protect themselves against phishing attacks that are as clever as this one, users should verify both the hostname and protocol before they enter any personal information on a web page. They should also enable two-step verification (2SV) if the feature is available for their accounts. That way, an attacker won't be able to compromise their account even if they obtain their password.

