
Security researchers found evidence that the Conti ransomware strain could be a possible successor to the Ryuk crypto-malware family. Vitali Kremez, strategic advisor for SentinelLabs, analyzed both Conti and Ryuk. He found that the former appeared to be based on the code of the latter's second version. He also observed Conti to be using the same ransom note that Ryuk had dropped in its earlier attacks.
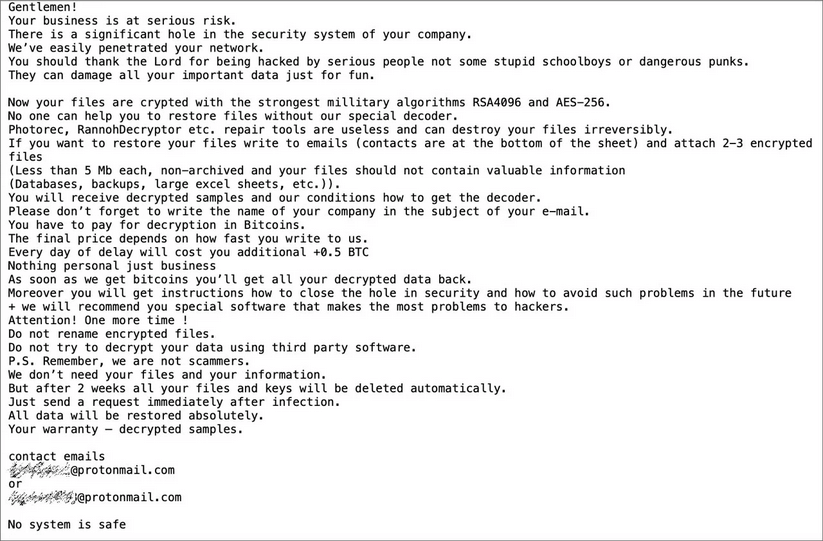
The shared Conti-Ryuk ransom note template (Source: Bleeping Computer) Finally, Kremez discovered that Conti submissions to ID-Ransomware were increasing while Ryuk attacks were decreasing. Both families leveraged the same Trickbot infrastructure for many of those attack campaigns. As Kremez told Bleeping Computer in an conversation:
Based on multiple incident response matters and current assessment, it is believed that Conti ransomware is linked to the same Ryuk ransomware developer group based on the code reuse and unique TrickBot distribution. The same distribution attack vector is used widely by the Ryuk deployment group.
Ryuk has a history of working with Trickbot. Back in July 2019, for instance, a municipality in Florida fired its IT director shortly after paying a ransom of $460,000 for an attack it had suffered a month earlier. In that "Triple Threat" infection, a malicious email attachment downloaded Emotet on the city's network. That malware then downloaded Trickbot, which was responsible for dropping Ryuk. Nearly a year after that, researchers uncovered several attack campaigns that waited two weeks after achieving a successful Trickbot infection before they deployed Ryuk ransomware as their final payload. The findings discussed above highlight the dynamism of the ransomware threat landscape. As one family's activity fades, another ramps up its attack efforts. Organizations therefore need to take steps to protect themselves against a ransomware attack. They can do this by working to prevent an infection in a first place. For more information on how Conti works, organizations can review Carbon Black Threat Analysis Unit's analysis of the ransomware family here.

