
Do you own an internet-connected DVR, CCTV or IP camera? You may want to check who manufactured it, as proof-of-concept code has been released capable of automating attacks against devices made by Dahua Technology. The firm has issued a security bulletin after a vulnerability researcher claimed that he had uncovered what he believed to be a backdoor into the devices, giving unauthorised users the ability to remotely download the device's database of user credentials and passwords. "This is like a damn Hollywood hack, click on one button and you are in," wrote independent researcher Bashis in a posting on the Full Disclosure mailing list. Controversially, Bashis explained that he had chosen not to give Dahua prior warning of his discovery, but to make the details public instead:
"I'm speechless, and almost don't know what I should write... I (hardly) can't believe what I have just found. I have just discovered (to what I strongly believe is backdoor) in Dahua DVR/NVR/IPC and possible all their clones. Since I am convinced this is a backdoor, I have my own policy to NOT notify the vendor before the community. (I simply don't want to listen on their poor excuses, their tryings to keep me silent for informing the community)"
Initially Bashis published proof-of-concept code, effectively giving anybody the ability to exploit the flaw. However, at Dahua's request, he has now withdrawn his code - but said he will republish it on April 5th as an incentive for the company to patch the problem quickly. For its part, Dahua has acknowledged that 11 of its devices with the following model numbers are vulnerable and made firmware updates available for download:
- DH-IPC-HDW23A0RN-ZS
- DH-IPC-HDBW23A0RN-ZS
- DH-IPC-HDBW13A0SN
- DH-IPC-HDW13A0SN
- DH-IPC-HFW13A0SN-W
- DH-IPC-HDBW13A0SN
- DH-IPC-HDW13A0SN
- DH-IPC-HFW13A0SN-W
- DHI-HCVR51A04HE-S3
- DHI-HCVR51A08HE-S3
- DHI-HCVR58A32S-S2
In its advisory, Dahua stresses that the vulnerability was not discovered through a malicious attack, but by the independent researcher's own testing. Furthermore, the firm says that it is continuing to investigate whether additional devices in its product line-up might face similar issues.
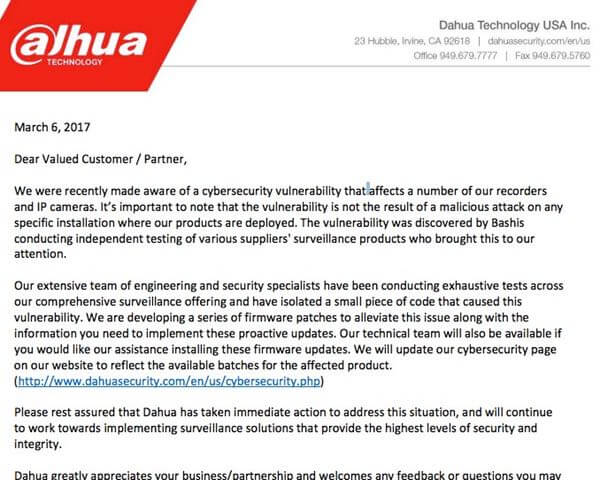
"Our extensive team of engineering and security specialists have been conducting exhaustive tests across our comprehensive surveillance offering and have isolated a small piece of code that caused this vulnerability."
Of course, if malicious hackers were to hijack control of Dahua's devices there is always the risk that they might be commandeered into nefarious activity - such as participating in a destructive botnet. Poorly secured IoT devices are proving to be a growing scourge for the internet because of lax security and the ease with which hackers seem capable of exploiting them. What we can't tell is whether this was truly a backdoor that Dahua's engineers intentionally left in device's firmware, or whether the sensitive credentials could be accessed through a bug. Personally, I'm more inclined to believe less in conspiracies and more in cockups. So I like to believe that this was an accident. What's most important now for users of the vulnerable devices is that they get patched quickly before they are exploited by malicious attackers. Furthermore, if you have made the mistake of reusing the same password on your internet-connected DVR or IP camera as you use elsewhere on the net, now would be a very good time to learn about sensible password practices. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

