
Over the years, I have written multiple articles on the subject of digital or cyber forensics and the importance it serves in supporting the modern world with regards to corporate and government incident response, first responder engagements, and more general aspects of scene-of-crime management in the digital age. Before we get into the detail, please allow me travel back to my days in the Royal Air Force, during which I took training on the subject of crime-scene-management. We covered a variety of issues, including the importance of preserving life, accessing the scene, and of course, ensuring that any acquired artifacts were properly documented, as well as how crucial it is to keep a contemporaneous record that one can in turn present to any enquiring/challenging authority. Following these practical gems of knowledge being planted, I transitioned them over to the operational world of policing, dealing with cases ranging from the RTA-72 (drinking and drive), administering the breath test, and overseeing the obtaining of blood samples, right through to the world of counter intelligence, conducting searches of persons and premises which were suspected to be the clandestine, unauthorised location for the illicit storage of high-grade classified materials. However, no matter the engagement, the same rules were always applied on every occasion in the form of ‘process’ – the King (and Queen) to assure that the investigation, and supporting acquired artifacts were robust, defensible (if subject to challenge) and that an accurate and robust chain-of-handling/custody, along with secure storage/transmission, had been applied at all stages.
Note: No matter what actions have been taken, what has been acquired, and what the implied burden of proof is, if process is broken, it can (and will) serve as the ‘Achilles Heel’ to challenge and diminish the value of what is presented, seeking to make it inadmissible, or to reduce its weighting to the case.
In essence, over the years, the very foundation of scene-of-crime management has not really changed, apart from one exception, which arrived in the guise of the digital footprint (DF): digital evolution. Here we are looking to the era of technology, people with tilted heads, walking down the street staring into the palm of their hand, the quick-jerk fingers of the lady on the train as she complies a text manage or email, right down to the case of the Soham Murders of Holly Marie Wells and Jessica Aimee Chapman in 2003 committed by Ian Huntley – all of which have one thing in common = 'DF'. In the case the Soham murders, the presence of the ‘DF’ was one key area of evidence supporting the prosecution, as whilst Huntley denied being in the vicinity of the crime, his cell phone inferred a different story as ‘it’ had registered in, or close to the edge of the radio-cell, and thus played an important part in placing, or inferring the suspects cell phone (and by association Huntley) had been close to, or in attendance at the scene.
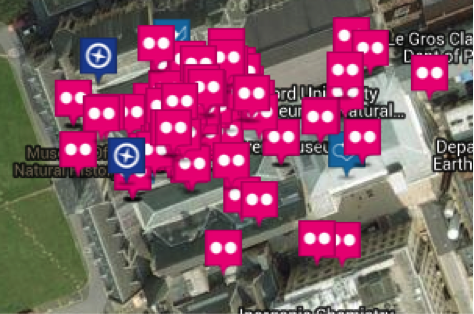
Fig 1 – Social Media Activity Map Extrapolate this forward to 2015, with Location Services and GPRS facilities, which can track and place individuals to locations, and we can start to appreciate the implications of what the DF can present. We may also look to some of low-cost tools, which have emerged to track individuals, and place them, or infer they are at, or close to a physical location – that is, assuming the transmitting device is in the possession of the legitimate owner. One such tool is echosec (See Fig 1 with the tool mapping social media activity associated with a University Campus).
In our technological age, it may therefore be argued that in around 99.99% of scenes-of-crime are associated with some form of technical component, and by implication it follows that there is a close, proximity, or a removed presence of the digital footprint is in existence. For example, the last phone call made by a victim, or attacker, a social media trace with an associated implication, some form of conjoined electronic interface between suspects; use of a home, or office-based VoIP appliance; metadata hidden deep inside the code of an image or document; the contents of removable media, or a computer hard drive; CCTV; and not forgetting the prospect of any related artifacts, which may be resident within the circuits and/or storage of on-board automobile computing facilities – all of which possess unknown possibilities for the representation of ‘DF’. It is for this reason I put the case forward that, whilst on rare occasion the ‘DF’ element may not be relevant at the end of the investigation, it must be considered as a matter of priority within the first responder landscape, and should thus be accounted as a process line entry as a matter of course for every crime scene or subsequent investigation encountered.
Locard's Exchange Principle
When considering the digital artifact, Locard's Exchange Principle is equally applicable to the world of bits and bytes in that the perpetrator of a crime will bring something into the crime scene and leave with something from it. For instance, consider the following as applicable to a Digital Footprint:
"Wherever he steps, whatever he touches, whatever he leaves, even unconsciously, will serve as a silent witness against him. Not only his fingerprints or his footprints, but his hair, the fibre’s from his clothes, the glass he breaks, the tool mark he leaves, the paint he scratches, the blood or semen he deposits or collects. All of these and more, bear mute witness against him. This is evidence that does not forget. It is not confused by the excitement of the moment. It is not absent because human witnesses are. It is factual evidence. Physical evidence cannot be wrong, it cannot perjure itself, it cannot be wholly absent. Only human failure to find it, study and understand it, can diminish its value."
Here, it is also important when considering digital forensics not to suffer tunnel vision on the digital element only, as the physical nature of the artifact may also provide proof of the act in both mens rea (guilty state of mind), and actus reus (the act).
Robustness of Standards
Given the importance of this digital science, it may be asserted that it cannot be left any longer to an approach based on chance, best endeavours, or a have-a-go approach, as the resulting implications, and the prospective impact(s) on both investigator, and suspect carry the potential of real world impact, which could manifest in woeful, damaging, and life changing implications. For instance, take the case of an ‘expert witness’ who provided testimony in support of the prosecution in a case of medical malpractice which focused on a key email artifact. However, our expert in this instance only passed judgment on what could be seen as lexical content within the body of the communication, and took the ‘To’ and ‘From’ as prima facie facts, and did not follow through with any further corroboration of the email headers – leaving the interpretation and assessment of the acquired artifact open to error – something which should have been subject to challenge.
ISO/IEC 17025:2005
It is for this reason why the application of the ISO/IEC 17025:2005 is so very important to drive the intrinsic expectations of competence, experience, and skill to assure that professionals who are engaging in this scientific practice meet the expectations of the discipline. For example:
- Was the digital evidence tainted or compromised regarding how it was collected and where it was stored? [1/2]
- Is the chain-of-custody complete and accurate? [1]
- Is on-the-job training alone sufficient to qualify the examiner as an expert? [2/3]
- Are documented, verified/validated procedures available for review? [4/5]
- Is the case file documentation complete and detailed such that another examiner can recreate the results of the examination(s)? [1/2/3]
- Were the examination results peer reviewed? [4/5]
- Is the examiner competent to perform the examination(s)? [2/3]
- Was the examiner proficiency tested? [5]
- How are the forensic computers and forensic software maintained and updated? [6/7]
- Are the software tools used legitimate, licensed, authorized versions? [7]
- Were the software tools performance tested prior to their use? [5/6]
- Did the software or hardware alter or change the original digital evidence? [1/2/3]
- Were scientific principles followed during the examination(s)? [1/7]
When considering the aforementioned shopping list of assurances, it may be argued that these fundamentally breakdown into 7 areas, which are shown in the below:
| Process | 1 |
| Training | 2 |
| Proficiency | 3 |
| Documentation | 4 |
| Review | 5 |
| Maintenance | 6 |
| Legal | 7 |
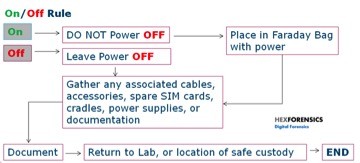
Fig 2 – Cell Phone Acquisition For instance, take item 1 from the table above. As an example let us focus on the exemplar process of taking a cell phone into the custody of the first responder, which can be seen at Fig 2. Of course, an additional step which may be applied to the process could be attaching a battery backup to sustain the acquired artifacts in a state of as-was at time of acquisition, to preserve the dynamic profile. Or what a documented process may exist to support first responder to make a qualified assessment based on a recognised scale – and here at Fig 3 below is an example of the COPINE (Combating Pedophile Information Networks in Europe) when investigating images, along with overarching support being driven the a high level policy at Fig 4:
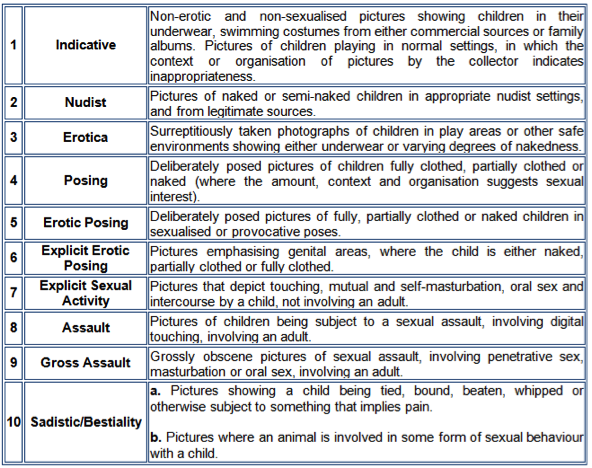
Fig 3 – The COPINE Scale

Fig 4 – High Level Policy
Hardware, Applications and Tools
When it comes to the hardware and applications in support of the digital forensic mission, whilst home-grown systems may well provision a level of service, they may not be of a proven ability, or accepted as trusted instruments to support the criticality of a serious investigation. Thus choosing established, and proven tools from the stables of access data in the form of FTK, EnCase, or the cost effective solutions from Paraben can go a long way to satisfying the provision of robust solutions – with the caveats that:
- They are maintained with the most current updates
- They are in the hands of proficient, and trained operators
There is, of course, the need to support the operational service of our digital forensics first responders with specialist hardware, such as write-blockers like the UltraBlock device to assure that when using Wintel Systems, the target drive is not contaminated with any anticipated ‘are-you-there’ system calls, which can leave their invasive footprint on the artifacts(s) under investigation. For the first responder working in the field, it is important to assure the collected evidential materials are afforded a commensurate level of protection when outside of any controlled environment. A very versatile and low-cost tool I have seen deployed is the CESG CCTM, FIPS 140/2 IStorage USB drive, fully enabled with Pin-Pad Access Control. The above is not a fully comprehensive list but does hopefully provide some exposure to the type of tools, applications and investigative support with which the digital forensics operator needs provisioning with.
Fit for Purpose Operations
It may be that for some organisations consider the gravitas which is applied to the technological requirements of such a critical service are beyond the internal capabilities and resources of the internal team, and that running a fully blown and robust internal digital forensics team within a commercial organisation may be cost prohibitive, and not represent a solid investment or ROI (Return on Investment). However, this should not bar any company from provisioning an in-house first responder capability (FRC) in the form of a first touch, first response/engagement element whilst at the same time recognising the implied limitations of the team. So, here, one may consider:
- Creation of policies to cover the objectives of the service offering
- Establish processes which may be applied to support the first responder engagement
- Define clear Terms of Reference (TORs) for the first responder team
- Provision an adequate base level of training to underpin their areas of anticipated expertise and responsibilities
- Recognise limitations
- Have an established contract in place with an external professional provider of such a service
Conclusion
It is an established opinion of many professionals, practitioners and academics that to provision such a service as digital forensics, by inference dictates the necessity exists to grant a high level of autonomy to those who are responsible, and incumbent to support such professional expectations. We must also keep a clear mind on one important fact: to acquire what can be dynamic and intangible, and time sensitive artifacts in the early stages of an investigation presents of highest opportunity of success. However to return to a scene which has seen the reuse, or change of state of any artifacts may well encounter they are no longer present, or have been corrupted, and diminished in their evidential value. As with dynamic states, they do not always wait for tide or mankind to return to acquire what was missed at the first pass. Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

