Week after week and year after year penetration tests are performed against companies and we continue to find the same things. Do you really want to hire that pentest company to come in and tell you the obvious? You could get better value from your tester if you take some simple steps to prepare before they start their assessment, not to mention you could make your systems more secure right now. Here are some things you should check (and fix) on your internal network right now. As always, these tests/changes should only be performed with prior authorization.
Remove Passwords from Group Policy Preference (GPP) Files.
Group Policy Preference (GPP) files initially expanded the capabilities of Group Policy to allow for adding users and passwords. The password resides in a file on the domain controller that is readable by all domain users and is encrypted. However, the private key used to encrypt the password has been published making it possible to decrypt any password stored in GPP. Microsoft released a patch in 2014 (link to: https://technet.microsoft.com/en-us/library/security/ms14-025.aspx) that removed the ability to deploy passwords using GPP because of this issue. However, the patch did not remove any passwords already existing in GPP files. Even if you don’t quite understand what all this means, just run this simple command from your work computer. If it returns anything, you’ve got passwords being openly exposed on your internal network. The command searches through XML files on the domain controller looking for the word ‘cpassword’
findstr /S cpassword %logonserver%\sysvol\*.xml
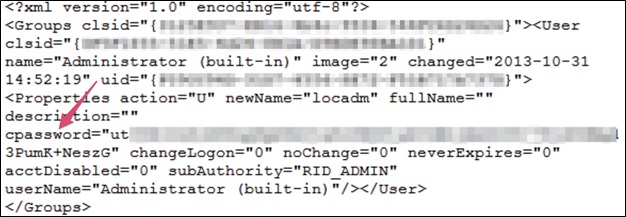
An example result from running this command is shown below. The ‘cpassword’ value, which has been redacted in this screenshot, is an encrypted password which can be easily decrypted. These passwords are often times valid administrator credentials.
In many cases, these GPP files are legacy files that are not even being used anymore and just plain need to be deleted. This will clear up one major vulnerability on your internal network. Wasn’t that so easy?
Check For Weak Password Use
An attacker could penetrate your network by impersonating other users after discovering their credentials. Chances are, someone on your network is using an all too easy to guess password. But how do you know? Try it! This one-liner will guess a set of passwords against all users on the domain.
@FOR /F %n in (users.txt) DO @FOR /F %p in (pass.txt) DO @net use \\DC-NAME\IPC$ /user:DOMAIN\%n %p 1>NUL 2>&1 && @echo [*] %n:%p && @net use /delete \\DC-NAME\IPC$ > NUL
Create a list of all domain usernames in a file called users.txt, one username per line. Put your password guesses in a file called pass.txt but be careful about account lockout! To play it safe, just use one password guess at a time. Lastly, substitute your domain name and domain controller name where highlighted in yellow above. Here are some great password guesses you should try, because your tester will:
- Current Season Name and Year (e.g. Winter2015, Spring16)
- Password1!
- Variations on Company Name
- P@ssw0rd
- ChangeMe
When you run the FOR loop as described it will output the username and password combinations that were successful as shown below.

To fix this, use a password policy that requires longer passwords that are harder to guess and continue to check that easy to guess passwords are not in use. Are you interested in learning more common ways that internal network are being compromised and what you can and should do about it? I’ll be covering a “Top Ten” list on the same topic with more examples and explanation at my BSides Seattle presentation on February 20, 2016 and BSides SLC presentation on March 11, 2016.

About the Author: Carrie Roberts is a Security Analyst for Black Hills Information Security. She performs regular penetration testing including web app, mobile and network assessments for companies in a variety of industries. She holds computer science and information security engineering degrees and recently earned the prestigious GIAC Security Expert (GSE) designation in 2015. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc. Title image courtesy of ShutterStock

