
Fraudsters are using fake Delta Air Lines receipts that lack any flight information whatsoever to infect unsuspecting users with malware. An attack begins when a user receives a fake payment confirmation email from Delta Airlines.

Fake Delta Airlines receipt. (Source: Heimdal Security) Notice anything missing? The senders of the email don't include any flight information in the message's body, something that you would expect to see in a legitimate email sent by Delta. See for yourself in the example below:
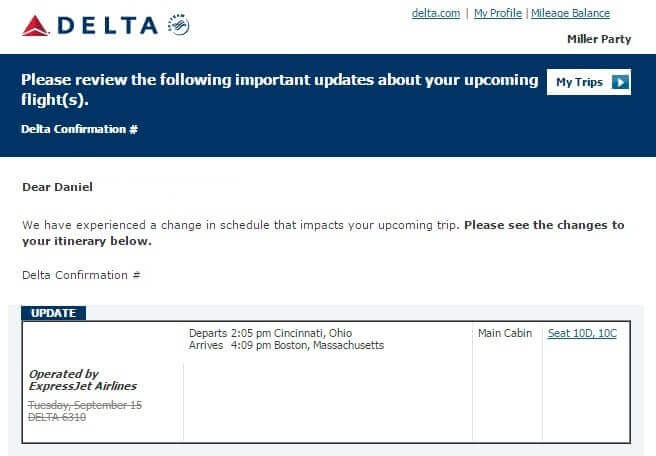
Legitimate Delta Air Lines receipt. (Source: Heimdal Security) Clearly, the fake email looks different than the legitimate receipt. It also doesn't originate from the proper sender. Valid Delta email addresses bear the "delta.com" domain, not "deltaa.com." Those differences notwithstanding, attackers are hopeful a recipient will click on one of the links embedded in their email. Heimdal Security's Paul Cucu elaborates on this point in a blog post:
"The email is designed to scare you into thinking someone bought an airplane ticket using your identity. You then panic and click on one of the links in the email in order to figure out how someone could do an unauthorized purchase with your credentials."
Clicking on a link redirects the recipient to one of several compromised websites hosting Word Documents. If the user downloads the document and opens it, the common phishing-based malware Hancitor uses PowerShell to infect the machine's legitimate system processes. At that point, the computer connects to a command and control (C&C) server from which it retrieves Pony. This credential-stealer terminates the campaign by downloading Zloader, a banking malware family. This isn't the first time we've seen Hancitor and Pony leverage malicious Word documents to distribute banking malware. With that said, users should protect themselves by disabling macros in Office documents by default. They should also exercise caution around suspicious links and email attachments. That goes especially for Delta Air Lines receipts with no flight information.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

