
In May 2016, the Federal Bureau of Investigations issued an alert warning hospitals, state and local governments, law enforcement, small businesses, and individuals to be on the lookout for a rise in ransomware attacks. The FBI acknowledges in its letter that in the absence of data backups, victims of a ransomware attack have no option but to pay the ransom. That's why it encourages individuals and companies to think ahead and invest in ransomware prevention, which includes a business continuity plan that organizations can implement in the event of an attack. Unfortunately, not everyone has listened to the FBI's recommendations. While some users lack the time or resources to develop a data recovery plan for their home and/or business, others simply believe they will never be affected by ransomware. That's wishful thinking in this day and age. Anyone can find themselves victimized by ransomware, which is why researchers at the University of Florida and Villanova University have devised a tool to provide users with an automated layer of ransomware protection. At the 2016 IEEE 36th International Conference on Distributed Computing Systems, the research team unveiled "CryptoDrop," an early-warning detection system for ransomware infections. The tool detects suspicious file activity and can terminate a process that appears to be tampering with a large quantity of a user's data. In an academic paper (PDF), the researchers explain their system relies upon three primary indicators to detect processes characteristic of a ransomware attack. Those are:
- Bulk modification of file types,
- Dissimilarity in how an encrypted file looks compared to its plaintext version, and
- High entropy output consistently produced by encryption.
CryptoDrop tracks those three indicators together across a single process to lower the occurrence of false positives resulting from benign programs. The system assigns a reputation score based on whether and to what extent a process might be behaving maliciously. If the score reaches a certain threshold, CryptoDrop alerts the user and terminates the process. That means the tool does not totally prevent data loss. But the researchers openly acknowledge CryptoDrop is not designed to protect all of a user's files:
"Our system does not attempt to prevent all files from loss and is not intended to replace a user’s normal anti-malware software; rather, CryptoDrop is de-signed to be effective even when the user’s anti-malware software has failed to block the malware. Our system is built on Windows, a platform frequently targeted for ransomware attacks, providing a realistic solution to 'in-the-wild' threats. In doing so, we attack the core behavior of ransomware in a novel and practical manner that other anti-malware technologies fundamentally cannot."
The researchers tested their system by unleashing 14 distinct ransomware families consisting of 492 individual samples onto a directory of 5,099 user documents.
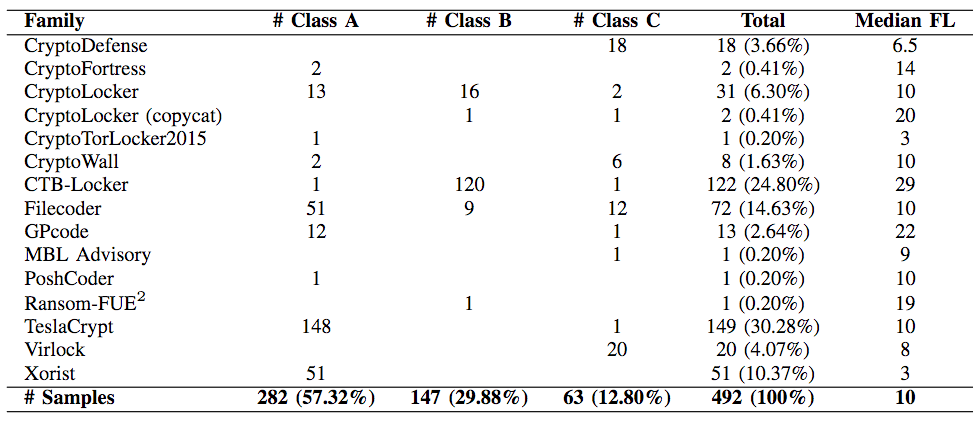
In their experiment, CryptoDrop detected all 492 samples. Each crypto-malware encrypted an average of 10 files before the system terminated it, but in some cases, CryptoDrop detected the ransomware before it had the chance to encrypt any files. The difference in detection speed rests with the order in which each sample attacked the files. This point of fact has security researcher MalwareHunterTeam questioning the system's viability. As he revealed to me in an email:
"An average of 10 files encrypted can cause enough problems. Attackers can break in through RDP. Once they are in, they can manually inspect the server and encrypt the most important files, or they can disable security tools to make sure nothing on the system is left untouched, thereby rendering CryptoDrop useless. Additionally, there are already some ransomware families that attack files with specified sizes or specified extensions (not the full extension list) first. If one of those files happens to be one of the 10 encrypted, that could spell a huge amount of trouble for the average user."
Aside from not being able to protect critical files, CryptoDrop still runs the risk of picking up false positives. The research team elaborates on that point:
"CryptoDrop is unable to determine the intent of the changes it inspects. For example, it cannot distinguish whether the user or ransomware is encrypting a set of documents. As a result, we expect that programs such as GPG and PGP, compression applications, and other applications which perform similar transformations will cause a CryptoDrop detection when applied to many user documents."
The system is not without its drawbacks, meaning its effectiveness would likely vary from user to user based upon how many critical files they have and how many background encryption-type tasks typically run on their computers. For now, CryptoDrop remains in the lab, but the research team hopes their system will eventually move to the public in the belief it can benefit the average user or company employee. You can read more about CryptoDrop in the researchers' paper here.

