
eBay has patched a cross-site scripting (XSS) vulnerability that attackers could have exploited in order to steal users' passwords. A researcher who goes by the name MLT explains in a blog post how he was able to exploit a "fairly basic" XSS vulnerability without needing to resort to any additional measures, such as bypassing the WAF, in order to spear phish for users' login credentials. He first begins his post by discussing how to create a convincing phishing page:
"Obviously the first step would be to obtain a copy of the website’s source for the login page," comments the researcher. "You could do this by saving the source code after viewing it manually, but this is time consuming and inefficient, as for the page to look identical you would need to individually download every single image that’s on the page and ensure that they are saved in the correct directories, as well as creating a bunch of relevant directories or altering the paths to images and other pages in the source code. Alternatively you can use some website mirroring software to automate this process, which is what I suggest doing."
MLT details his use of the WebHTTrack software to save all of the necessary web files, which are downloaded into the correct directory. He next discusses how he changed the form inputs to direct to his PHP script rather than eBay's login script. After locally testing the forms, the researcher reveals how he was able to include the link to his phishing page in eBay's code.
"In the example of ebay, the XSS vulnerability was not tag-based but was rather pure javascript, so rather than including an iframe directly as input to the ?url= get param, the javascript document.write function needed to be used to write the HTML contents to the page and embed the iframe," he observes.
Ultimately, he injected an iframe containing his phishing link into the code, thereby creating a very convincing fake eBay log-in page:
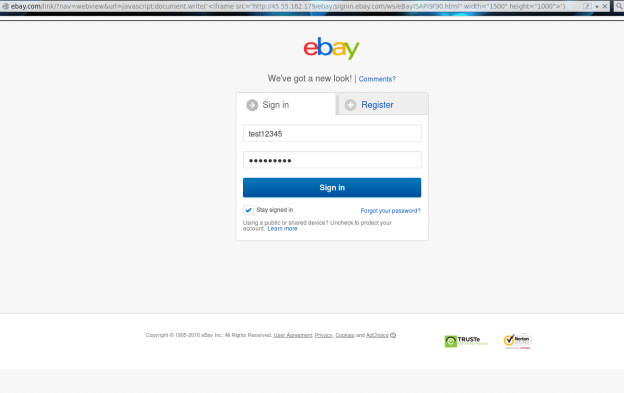
Via this technique, every time a user entered their credentials, a GET request on his server would connect to log.php and the inputs would be written in plaintext. A video of this exploit in action is available here. Motherboard reports that the researcher found the vulnerability and reported it to the e-commerce website on December 11. Last week, both MLT and eBay confirmed that the bug has been patched. News of this bug follows three vulnerabilities, including a client-side XSS flaw, that eBay patched back in early summer of last year.

