
A malvertising actor known as "eGobbler" used obscure browser bugs to bypass built-in browser protections and expand the scope of its attacks. Confiant observed eGobbler exploiting the first vulnerability back on April 11, 2019. In that particular attack, the threat actor leveraged a Chrome exploit to circumvent the browser's pop-up blocker built into iOS devices. The impact of the bypass was even greater due to the lack of mitigation from iframes with standard ad-serving sandbox attributes. Six days after the malvertiser began using this weakness, Confiant notified the Chromium team about it. These researchers responded by releasing a fix for the vulnerability (CVE-2019–5840) in Chrome 75. They then lifted the security view restrictions on the report submitted by Confiant in early August. But malefactors like eGobbler are always constantly evolving. Case in point, it was around the time when the Chromium team lifted those view restrictions that a new eGobbler payload emerged. Confiant recreated its testing environment and found that the iOS Chrome pop-up blockers were once again not working. This time, however, researchers experienced redirections using WebKit browsers upon the ‘onkeydown’ event. As Confiant noted in a blog post:
The nature of the bug is that a cross-origin nested iframe is able to “autofocus” which bypasses the “allow-top-navigation-by-user-activation” sandbox directive on the parent frame. With the inner frame automatically focused, the keydown event becomes a user activated navigation event, which renders the ad sandboxing entirely useless as a measure for forced redirect mitigation.
The security firm reported this issue to Apple on August 7. Within two days, Apple responded and said it was investigating the issue. That's the same day when WebKit received a patch for the bug. Approximately a month later, Apple closed the security gap in both iOS 13 and Safari 13.0.1.
eGobbler still had a busy month, however. From August 1 to September 23, the malvertiser affected 1.16 billion impressions. Those attacks targeted primarily Windows users surfing the web via Chrome in 13 different countries.
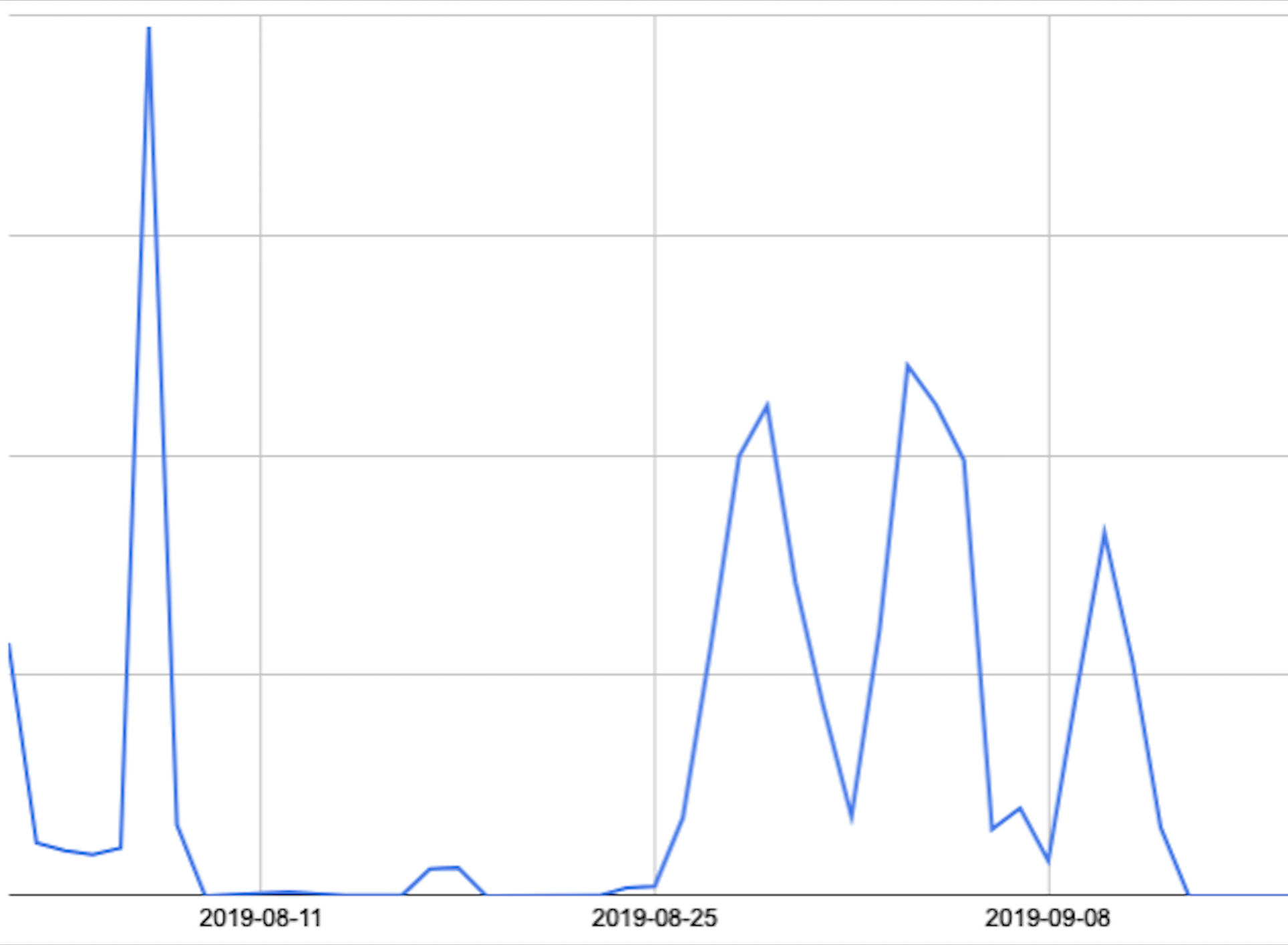
eGobbler Activity By Day 08/01–09/23 (Source: Confiant)
The scale of eGobbler's campaigns, not to mention the speed with which it has adopted new exploits, illustrates the importance of organizations taking security vulnerabilities seriously. One of the best ways they can do this is for organizations to strengthen their vulnerability management capabilities. Learn how Tripwire IP360 can improve organizations' efficiency and focus when dealing with security weaknesses.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

