
Our nation depends heavily on the more than 2.3 million miles of pipelines in the United States that move oil, gas and other liquid products cross country to delivery points, such as airports, refineries, homes, and businesses. At an average of every 40 miles for natural gas pipelines, there are compressor stations that move the gas further along the pipeline. Each compressor station depends on PLC’s (Programmable Logic Controllers) to regulate flow and communicate critical operational information. Recently, these devices have come under attack by targeted malware.
In the last few years, malware designed to take over and control SCADA systems, e.g. pipeline pump stations and compressors, has become more prevalent. You may be familiar with examples like BlackEnergy, Stuxnet, Shamoon and Dragonfly/Havex.
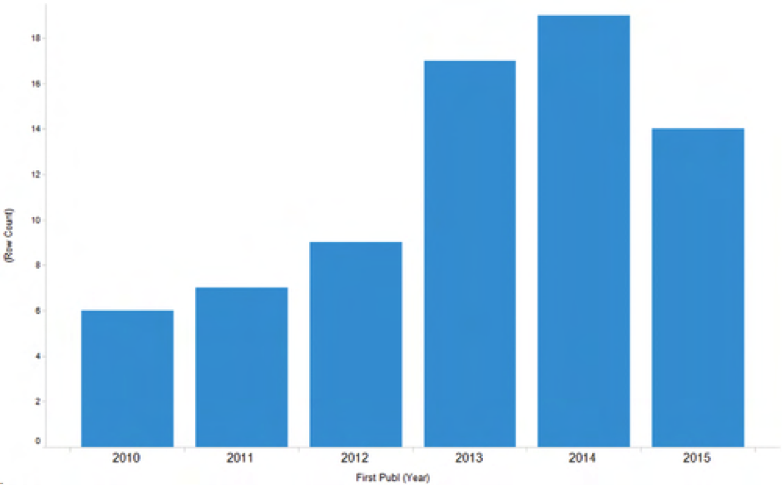
The number of reported exploits has risen sharply since 2011, and for 2015, it is continuing that trend. (Source: Recorded Future) Just one specific example is the attack on Saudi Aramco that occurred on October 23, 2012. As CIO blogger Constantine von Hoffman wrote, “You don’t destroy 30,000 workstations without causing a vast amount of damage. It might be possible that the attack didn’t directly hit oil production or harm the flow of oil out of the ground. No one I’ve spoken to has suggested it did, but it’s clear that if the company's statement is true, then Aramco used a very strict reading of the phrase 'oil production.'"
Pipeline SCADA Segment/Components Threatened Today
The devices and systems that are critical to the nation’s pipeline system are not your average Microsoft or Linux servers. These components are often fit-for-purpose and sometimes specifically unique to the pipeline industry. End Points – RTU (Remote Terminal Units), PLC’s (Programmable Logic Controllers) are one of the most critical component of pipelines as they can all too often be hacked and thus enable bad actors to remotely control and even destroy not only the device itself but also destroy what they are controlling, e.g. the compressor, pump, or generator. Communication Networks – Many pipelines today rely on satellite VSAT (Very Small Aperture Terminal) to provide critical SCADA communication. Traditional communications, e.g. lease circuits and other network mediums, are often not available in remote areas where pipelines traverse. Shared satellite networks all too often do not have hot-standby alternate satellite service for outages when the primary satellite link is out of service. SCADA Host (e.g. Pipeline Control Centers) – HMI (Human Machine Interface) are in many cases “open” to hackers wanting to take over control of the pipeline, and if the pipeline SCADA system “faces” the internet, then online malicious actors can get to the pipeline. In many cases, a standard, off-the-shelf approach to cybersecurity won’t work for pipeline infrastructure.
What Can We Do?
ICS-CERT

We all need to join together to do whatever we can do to protect our nations pipeline infrastructure. Learning more about ICS-CERT is one way we can help: ICS-CERT coordinates control systems-related security incidents and information sharing with Federal, State, and local agencies and organizations, the intelligence community, and private sector constituents, including vendors, owners and operators, and international and private sector CERTs. The focus on control systems cybersecurity provides a direct path for coordination of activities among all members of the critical infrastructure stakeholder community.
Control Systems Advisories and Reports
- Alerts - Alerts provide timely notification to critical infrastructure owners and operators concerning threats to critical infrastructure networks.
- Advisories - Advisories provide timely information about current security issues, vulnerabilities, and exploits.
- ICS-CERT Monitor - We provide this newsletter as a service to personnel actively engaged in the protection of critical infrastructure assets.
- Joint Security Awareness Reports (JSARs) - ICS-CERT coordinates with US-CERT and other partners to develop Joint Security Awareness Reports (JSARs) to provide situational awareness for the public on cybersecurity issues.
- Other Reports - Technical Information Papers (TIPs), Annual Reports (Year in Review), and other products that ICS-CERT believes are of interest to persons engaged in protecting industrial control systems.
InfraGard

You can join InfraGard and attend monthly regional meetings in your area to learn more about all the threats to our critical infrastructure. InfraGard partners with the FBI and thousands of volunteers who are dedicated in protecting our nation’s critical infrastructure. Pipelines fall under the InfraGard Transportation Sector. InfraGard has various Special Interest Groups (SIG), and each InfraGard Chapter typically has an “Oil & Gas SIG” (of which I am a member) that meets each month to learn more about technologies that can protect areas within the Oil & Gas Sector. Leading industry professionals are selected each month to do a presentation to share proven technologies that provide critical infrastructure protection. There are InfraGard chapters all around the country.
Support Developing Cybersecurity Frameworks
There are many standards and frameworks for cybersecurity, but few address the needs of pipeline security. You can both support these standards and influence them to consider the vital pipeline infrastructure as well. In 2013, the President issued Executive Order 13636 on Improving Critical Infrastructure Cybersecurity. This EO sparked the creation of the National Institute of Standards and Technology (NIST) Cybersecurity Framework and the National Cybersecurity Center of Excellent (NCCoE). The Cybersecurity Framework uses business drivers to guide cybersecurity activities and consist of three parts: the Framework Core, the Framework Profile, and the Framework Implementation Tiers. It’s currently in version 1.0. Pipeline companies and professional should support this framework and seek to influence its evolution through the workshops and events hosted by NIST.
Conclusions
Pipeline cybersecurity may not get a lot of attention, but it’s a vital part of our energy infrastructure that is at risk from cyberattack. As information security professionals, we should encourage broader thinking and inclusion of pipeline security issues in critical infrastructure discussions. You can make a difference with just a little additional focus and participation. Together we can help protect pipelines and ensure that our energy supply is safe from cyberattack.

About the Author: Ron Carr is President and Managing Member of Access Control Technologies, LLC (ACT) a sales representative company he started in 2008. He has over 40 years’ experience in pipeline SCADA communications, and he is a Business Development Partner for Tripwire. Previously, Ron had a tenure at Motorola for 14 years and was a Zone Manager responsible for the Energy Market. Ron has also held Account Manager position at Stratos Global Corporation and was responsible for accounts of many Fortune 100 pipeline companies. Ron is a member of the InfraGard and is Vice President of the City of Houston Police Department PIP (Positive Interaction Program). He is a United States Air Force veteran and frequently hosts corporate webinars on various topics, including pipeline SCADA communication and cyber security. He is a blogger on the Tripwire State of Security website. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

