
Digital attackers created a fake PayPal website to distribute samples of a new variant of the Nemty crypto-ransomware family. Security researcher nao_sec uncovered the ransomware variant after they came across a fake PayPal website. This site promised users a return of 3-5 percent for making purchases through its payment system. But its primary purpose was to trick visitors into downloading and running a malware executable called "cashback.exe."
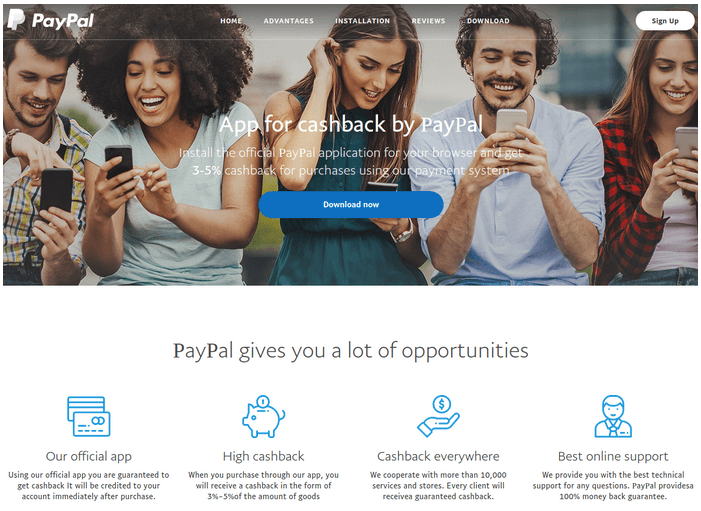
The fake PayPal website (Source: Bleeping Computer) To do this, the site stole the structure and branding of PayPal's official site to trick users into believing it was a legitimate location. It also leveraged homograph domain name spoofing techniques to fool users who might have been a bit warier of its promises. As Bleeping Computer explained in its research:
The crooks achieved this by using in the domain name Unicode characters from different alphabets. To distinguish between them, browsers automatically translate them into Punycode. In this case, what in Unicode looks like paypal.com translates to 'xn--ayal-f6dc.com' in Punycode.
Once run, cashback.exe loaded version 1.4 of Nemty ransomware, a threat family which has leveraged compromised Remote Desktop Protocol (RDP) connections and the RIG exploit kit for distribution in the past. This version arrived with a few modifications and bug fixes. For instance, researchers observed that the malware authors had updated the "isRU" check, which Nemty uses to verify the location of an infected host. If it finds that the computer is located in Russia, Belarus, Kazakhstan, Tajikistan or Ukraine, it terminates before initiating its encryption routine. Otherwise, it encrypts the machine's files and deletes its Shadow Volume Copies. News of this new Nemty variant and distribution vector demonstrates how many ransomware attackers continually update their programs in order to more efficiently prey on users. In response, users and organizations alike should follow security best practices designed to prevent a ransomware infection in the first place. This resource is a good place to start.

