
A security firm has released the results of an experiment that used a honeypot script named "GasPot" to determine the security threats facing gas tanks. These results were announced by Trend Micro researcher Kyle Wilhoit and Industrial Control Systems (ICS) expert Stephen Hilt during their presentation for Black Hat 2015, "The Little Pump Gauge that Could: Attacks Against Gas Pump Monitoring Systems."
"Over a period of months, several Guardian AST gas pump monitoring systems were attacked," reads the description for Wilhoit and Hilt's talk. "These attacks occurred on real pump monitoring systems, but also on systems that we controlled, created, and deployed. We watched these attackers, what they did, and performed intelligence gathering on the nefarious actors."
The types of attacks varied in sophistication. Whereas simple ones enabled the attackers to monitor the status of a given pump, more advanced techniques gave attackers the ability to manipulate their targets' tanks. According to a blog post published by Trend Micro, this latter category of attacks consisted of acts of vandalism--such as changing the name of a pump, which Trend Micro believes Anonymous may have done with one particular unit it was monitoring--to changing a pump's behavior so that it became a public safety hazard. Wilhoit and Hilt observed all of this and more using GasPot, a single Python script that was intended to function as a honeypot to the extent that it could log connections and compromise attempts.
"It [GasPot] was designed from the ground up to look like no other existing virtual honeypot," reads a research paper published by Trend Micro on its experiment. "Each instance that it runs is unique, making honeypot fingerprinting harder for attackers to do."
Patching vulnerable gas tank systems will be difficult, according to Trend Micro, because of an unpreparedness when it comes to patching SCADA systems more generally. In fact, as a result of many SCADA systems, such as gas tanks, running legacy code, not to mention the threat of service interruptions for customers, most ICS experts estimate that only 10-20 percent of systems will implement patches that are released by manufacturers.
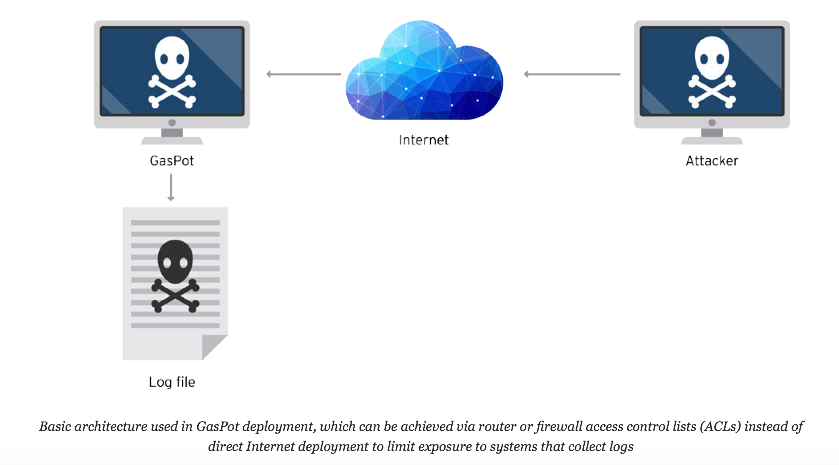
Source: Trend Micro It is important to note this is not the first instance that security vulnerabilities have been found in automated gas tank systems. Earlier this year, a security researcher for Rapid7 discovered that 5,800 automated tank gauges were exposed to the Internet with no password set, leaving them vulnerable to web-based attacks. To learn more about Trend Micro's GasPot experiment, please click here.

