
Today was another successful day at BSides Las Vegas, with more intriguing presentations and an amped up crowd ready to hear from security researchers, engineers, analysts and catalysts alike. Although there were numerous interesting topics to choose from, my time only permitted for about a half-day of sessions. Luckily, many of the presenters noted they would make their slides available online, and videos of the talks are also expected to be published by BSides soon. Below is a quick recap of some of today’s sessions, including the awesome visual notes drawn by our sponsored graphic artist Kelly Kingman.
ZOMG It’s OSINT Heaven
Speaker: “Tazz Tazz” (@GRC_Ninja) The first session I attended was presented by “Tazz Tazz” who discussed OSINT (open source intelligence) and posting personally identifiable information (PII) online. Tazz Tazz began by explaining the numerous times she’s encountered tweets of people’s credit card numbers – in many instances, they believe it cannot be used without the CVV code, which is not true. She also made it clear that OSINT is not open source Internet, the Dark Web, or conducted with a “magic button.” It’s also not something that requires expensive tools. Tazz Tazz walked us through an interesting case study of how she was able to find out a plethora of information on a certain user, stemming from a single post. After leveraging several websites (many of them being free to access) she was able to gather information on this person’s current and former employer, education, date of birth, home address, and much more.
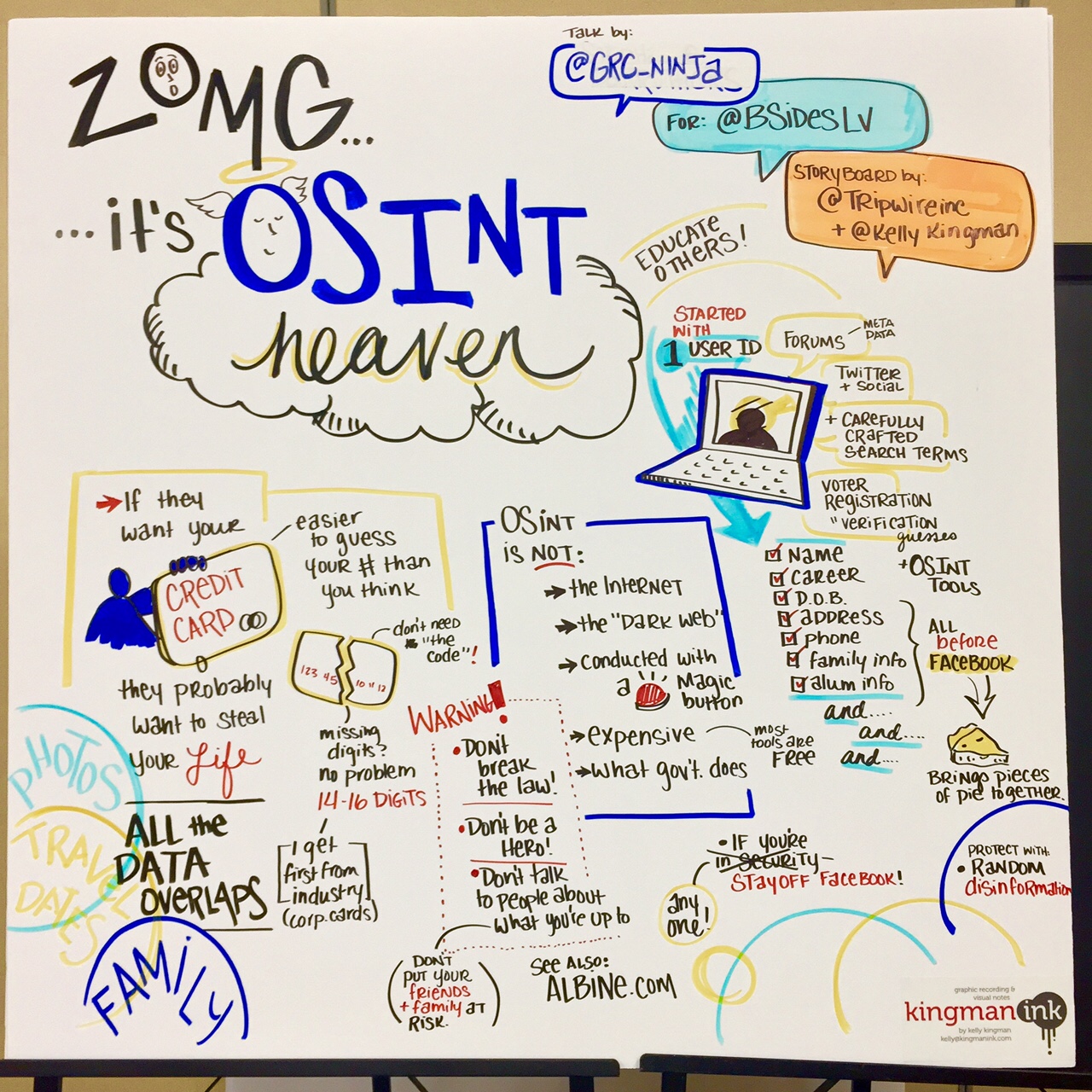
*Note: Correct link on image should be abine.com. Easy-to-access sites, such as Facebook and LinkedIn, often serve as a way to check for data overlap on the information the user has made available online. Her biggest recommendation on how to make it harder for fraudsters or criminals to get this info? Get off Facebook. Tazz Tazz urges even those not in the security space to consider getting rid of their profile. “It’s difficult to remove yourself from the grid, but it’s possible,” she said. She also recommended we go talk to people and educate them on these risks. Another tactic would be to provide disinformation on social channels, though it should be at least semi-legitimate.
I Forgot My Password
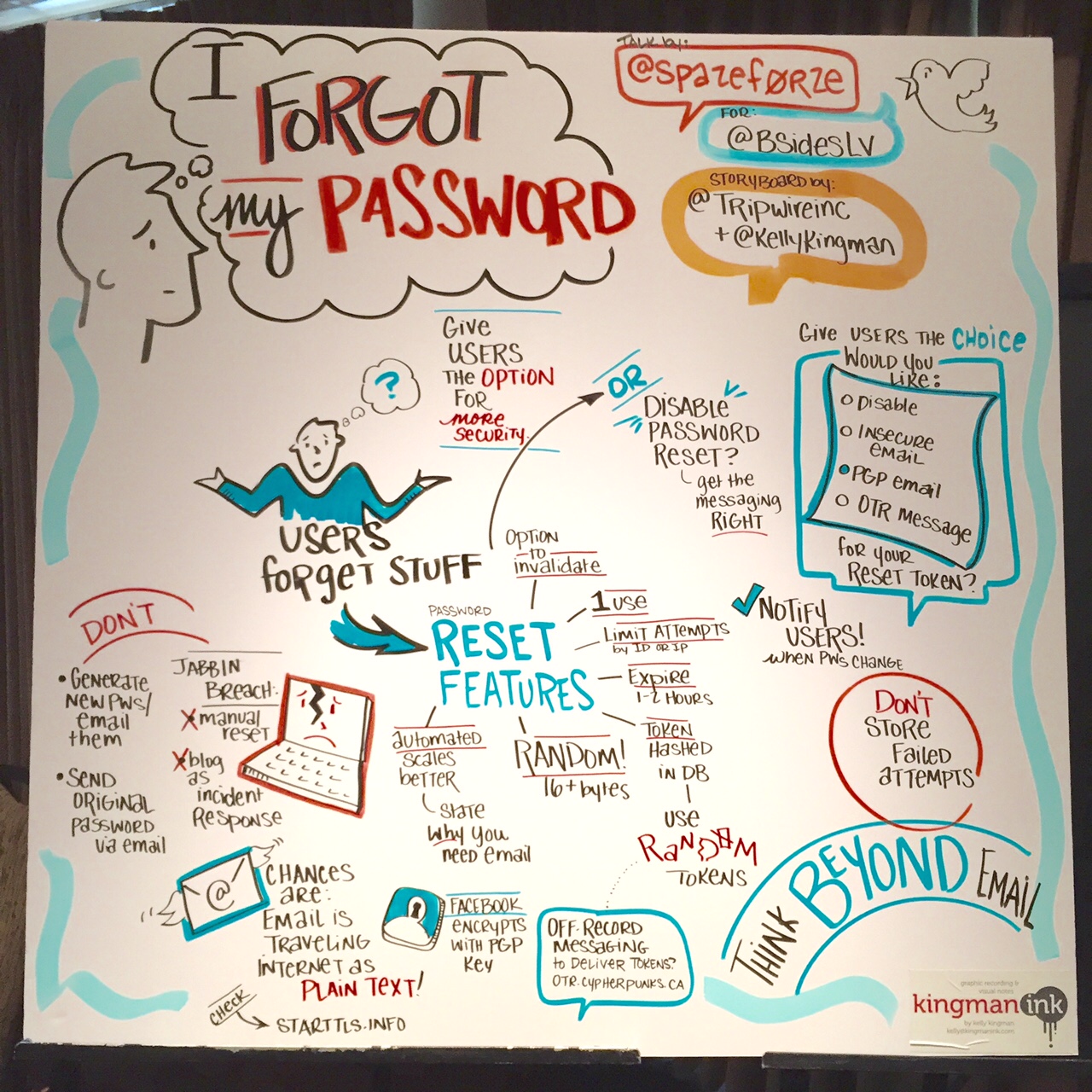
Speaker: Michal Spacek (@spazef0rze) This session was targeted towards applications looking to strengthen their password-reset mechanism. There are several ways to go about this, but many of them are fairly insecure. Michal made some good key points for these applications to consider, from basic to more mature practices. He said password resetting should be random 16+ bytes, should expire in 1 or 2 hours, be made usable only once and have the option to invalidate. Furthermore, the number of attempts that can be made from a single IP address and for one username should be limited. Michal also noted that it’s important to use the right messaging when alerting a user their passwords needs to be reset. Additionally, applications may want to think beyond a password-resetting email and give users the option for more security, such as disabling the account, sending a PGP email or an OTR message.
Phishing: Going from Recon to Credentials Speaker: Adam Compton (@tatanus) Adam’s talk gave an introduction into “phishing,” a tried-and-true tactic leveraged by attackers in which they attempt to acquire sensitive information by masquerading as a trustworthy entity via electronic communication.
According to Adam, this common scamming method goes back to the mid-90s. “It used to be ‘script kiddies’ running visual basic scripts or attackers posing as AOL admins via IM and email,” he said.
So, why phish when there are numerous other attack vectors? Because it works! People are gullible, we want to be helpful and we’re also “unpatchable.” In addition, phishing has a high return on investment. It’s much easier to target 10 – 20k people for the same effort as targeting 10, 20 or 30 through other attacks. Lastly, phishing bypasses all the perimeter controls.
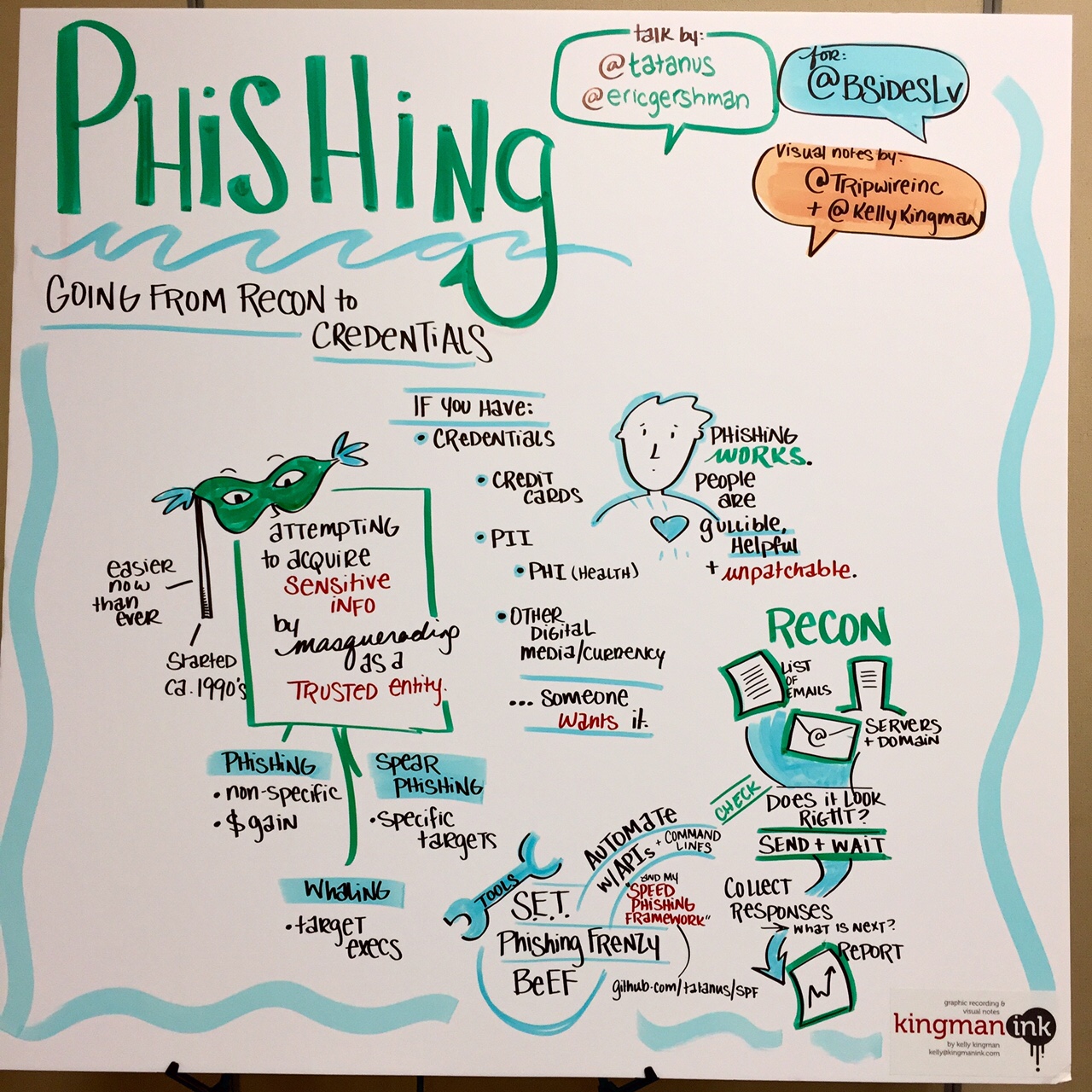
Adam mentioned a few common tools that can make phishing easy, including SET (Social Engineering Toolkit, PhishingFrenzy and BeEF). At the end of his presentation, he gave an overview of a phishing tool he’s been working on, called SPF.
Social Media In Incident Response Program
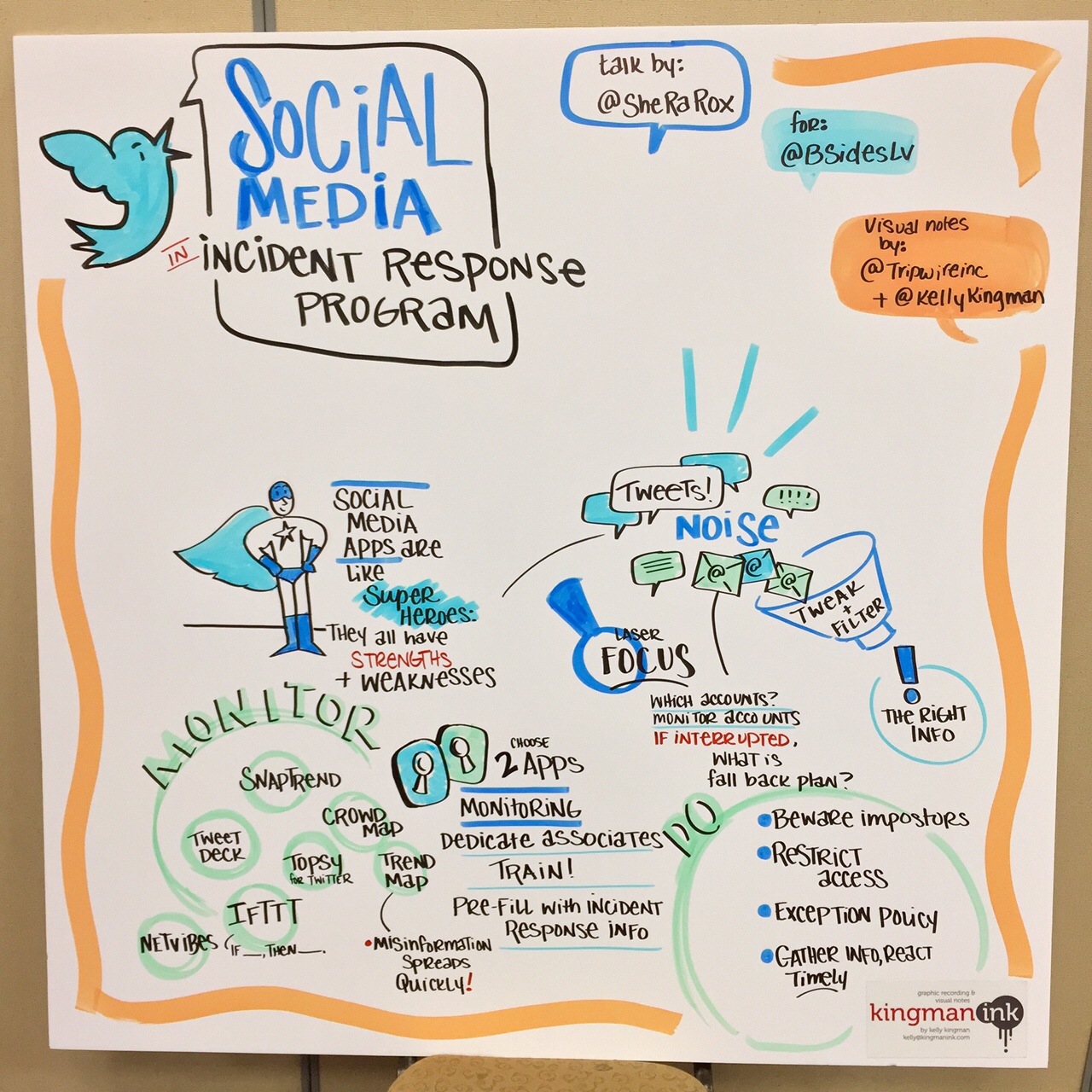
Speaker: JoEtta LeSueur (@SheRaRox) In this presentation, JoEtta discussed various strategies and tools to make social media an integral part of your company’s incident response. The first goal is to choose two social media apps that can be integrated to your IR program. Remember that monitoring these channels will require dedicated and trained, associates, and you’ll need to configure the use of these applications with corporate needs. The second goal will be to make sure these apps have a laser focus. Work closely with legal department and discuss whether these would be run on your network vs. the cloud. Think about if an unexpected outage were to occur, what would be your backup? JoEtta suggested a number of social media tools to help with monitoring, such as:
- Crowdmap – used to collaborate physical location
- Trendsmap – monitor hashtag trends physically
- Topsy – used for Twitter hashtag analytics
- Snaptrends – monitor and analytics on social media apps
- Tweetdeck – for scheduling tweets and monitor accounts
- IFTTT – for simple multiple account recipes
- Netvibes – use to set up and monitor several social applications
A restricted list of employees with access to posting/logging in, etc. may be a good practice, and be sure to establish an official communications policy. Last but not least, JoEtta recommends to look out for imposters, or fake accounts, and figure out how to address those situations.
FAA, FTC, FCC – FU: How Three F’ing Agencies Are Shaping InfoSec
Speaker: Elizabeth Wharton (@LawyerLiz) The last talk was one of my personal favorites, presented by a very passionate Elizabeth Wharton. She discussed the three government agencies whose recent oversight and regulatory actions are slowly shaping the direction of information security research. Why have these agencies suddenly picked up the interest in cybersecurity? As Elizabeth explained, the answer is money, fame and political power – it’s all about big budgets. For example, after the FCC introduced net neutrality rules, they requested an additional 73 million in budget for the fiscal year of 2016. Until recently, these were overlooked agencies that didn’t take the headline approach. But now, these agencies are having hearings, promoting themselves and even gaining a large follower base online.
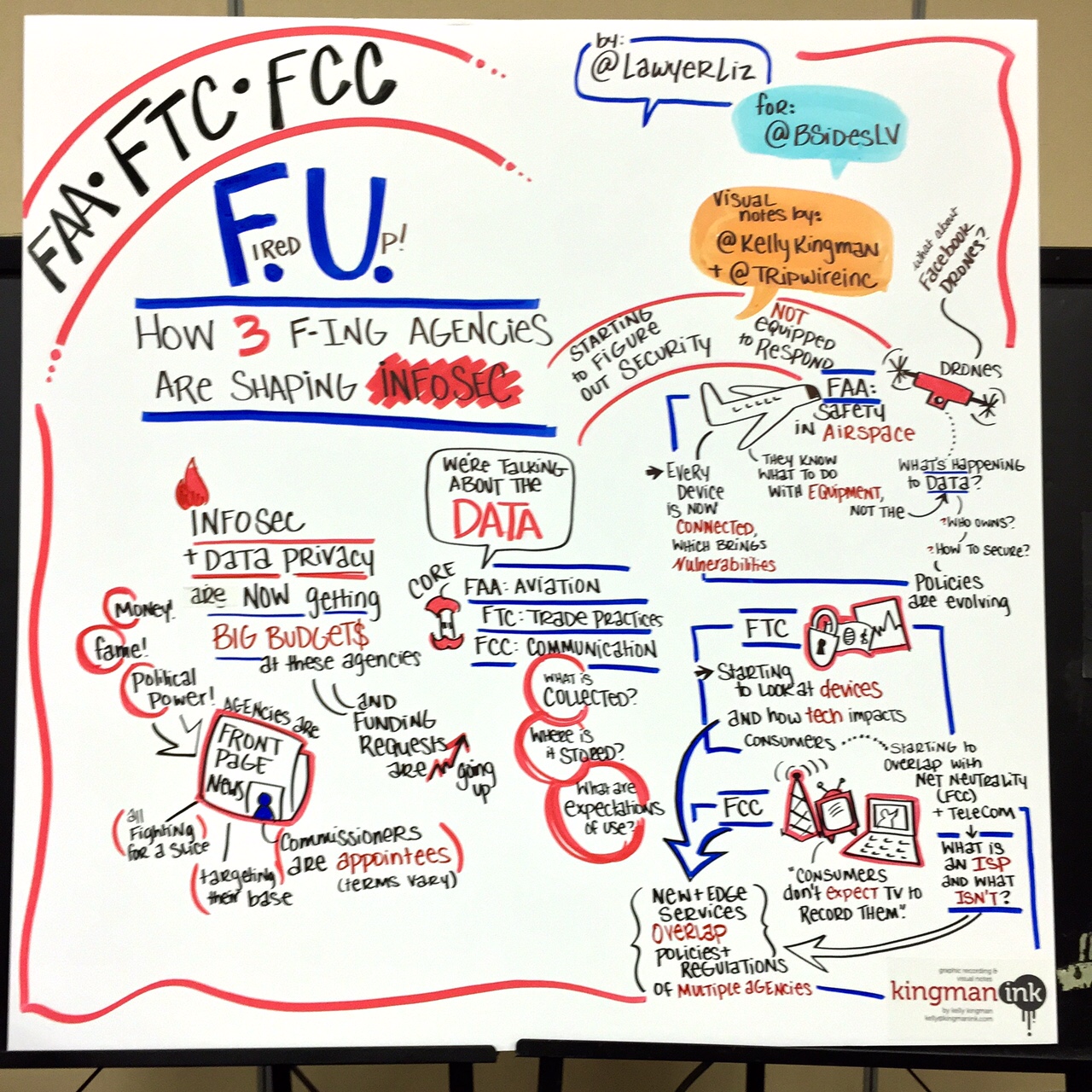
Elizabeth added that although the FAA’s core mission is aviation, it recently began looking into how to implement the rolling out of drones. Meanwhile, the FTC’s core mission is to protect consumers, prevent fraud and deception in unfair business. Not too long ago, however, they released an IoT report looking at the development and protection of devices as they were launched. As one audience member asked, “so, what’s next?” Who knows… It’s the gap that these three-letter government agencies have yet to close.

