
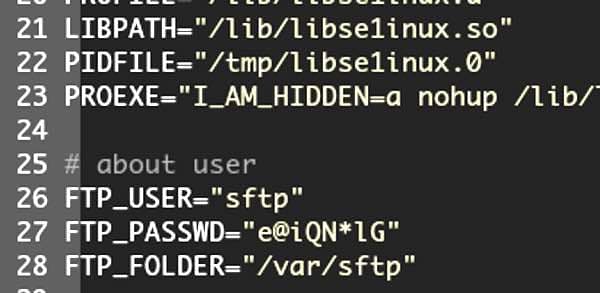
Security researchers have discovered a new strain of malware called "HiddenWasp" that they believe is being used in targeted attacks to seize control of Linux systems and open backdoors for remote hackers. According to a blog post by researchers at Intezer, the malware borrows from existing malware code publicly available on the internet including the Azazel rootkit and the notorious Mirai worm. The researchers say there are similarities between HiddenWasp and the Linux branch of the Winnti malware family, as the malware contains a user-mode rootkit, a Trojan horse and an initial deployment script. In its initial deployment script, HiddenWasp sets up a user named 'sftp' on the compromised system with a hardcoded password. It would appear that the script does this to allow hackers to continue to gain access to targeted systems even if their malware is later spotted and removed.
The malicious script can also clean up older versions of HiddenWasp on infected systems and download a tar-compressed archive containing all of its components, thereby providing a means to ensure compromised computers are running the latest version. Clues scattered within the code, as well as similarities with previously-discovered malware, point a finger of suspicion towards China, though Intezer's researchers admit that the attribution should only be made with "low confidence."
We noticed that the trojan has code connections with ChinaZ’s Elknot implant in regards to some common MD5 implementation in one of the statically linked libraries it was linked with. In addition, we also see a high rate of shared strings with other known ChinaZ malware, reinforcing the possibility that actors behind HiddenWasp may have integrated and modified some MD5 implementation from Elknot that could have been shared in Chinese hacking forums.
So, how does HiddenWasp end up infecting systems running Linux? Unfortunately, the security researchers have not been able to answer that question. The malware can be found on Linux computers, and it is possible to determine how HiddenWasp can be used to run commands on the terminal, execute files and be commanded to download further malicious scripts by its remote hackers, but it isn't apparent how computers are being infected in the first place. In other words, it's quite possible that computer systems are being compromised in a variety of ways and *then* HiddenWasp is being deployed as a secondary payload by attackers. Intezer's researchers claim that security products are currently doing a poor job of detecting the HiddenWasp malware and recommend that concerned administrators block the Command & Control IP addresses listed in its the IOC section of its blog post.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

