
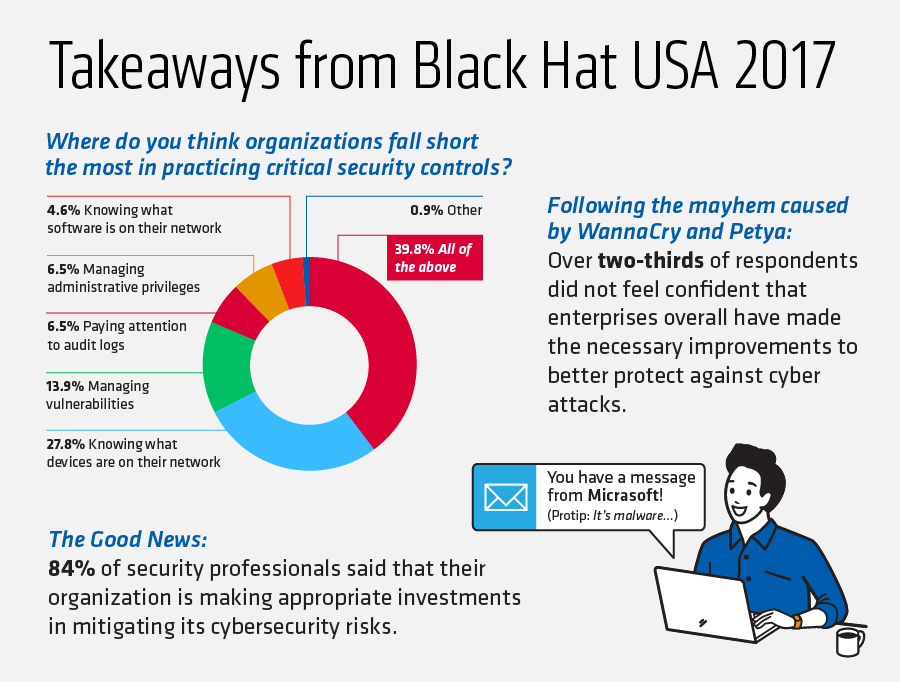
The WannaCry and NotPetya attacks caused disruption on a global scale in the spring and early summer of June 2017. Following those malware campaigns, businesses around the world should have heard the alarms and responded by tightening their security systems in an effort to mitigate against similar attacks in the future. But reality doesn't always adhere to the logic of "should," a sobering thought which leaves us with one question: have organizations actually worked to strengthen their security in the wake of those global malware outbreaks? In an effort to answer that question, Tripwire surveyed 108 security professionals at Black Hat USA in July 2017 and asked them about the security improvements their organizations made after the WannaCry and NotPetya attacks. The results were discouraging. Over two-thirds (68 percent) of respondents did not feel confident their enterprises made the necessary improvements to better protect against digital attacks following the WannaCry and NotPetya outbreaks. When asked where they thought organizations were coming up short with their security, approximately a third (28 percent) said network device discovery was the biggest issue businesses weren't addressing. Others pointed to vulnerability management (14 percent), administrative privilege management (6 percent), and audit log reviews (6 percent) as other controls being overlooked, whereas two out of five respondents said organizations were failing across multiple security measures. Tim Erlin, VP of product management and strategy at Tripwire, feels organizations' lackadaisical response to WannaCry and NotPetya is dangerous considering the cost of falling victim to a digital attack:
“No matter the size of your organization, you must treat cybersecurity seriously. If you were lucky enough not to have been directly affected by WannaCry or Petya, take it as an opportunity to get your cybersecurity house in order. Remember, you don’t have nine lives. All it takes is one data breach or another WannaCry and your company has lost data, money, credibility and most importantly, customer trust, which is one of the most difficult things to recover."
The survey wasn't entirely doom and gloom. Eighty-five percent of those surveyed said their organization is making appropriate investments in solutions that can help mitigate its digital security risks. It's reassuring to hear so many organizations are investing in security technologies and other defenses. But hopefully, those companies are doing more than just that. Erlin identifies another method of protection that organizations should be actively pursuing in the aftermath of WannaCry and NotPetya:
"One of the most important tools, and probably the one that gets overlooked, is education. Malware attacks often rely on social engineering and playing on the weakness of human nature. The recent malware attacks are perfect examples of where a sound, consistent education program could have either prevented or reduced the impact of the attack."
In other words, technology is a crucial component of a digital security policy. But businesses don't run themselves. People do, which means employees need to be aware of and ideally help hold the line against digital threats like WannaCry and NotPetya. At the same time, organizations should aim to reduce their digital security risk by implementing foundational security controls such as the Center for Internet Security's top 20 critical security controls (CIS CSC). Erlin agreed:
“Adopting best practices and leveraging critical security controls continues to be the best bet for defending against advanced adversaries, and can help close the gap within a business’s security infrastructure. There is solid research that supports the claim that the vast majority of attacks are due to known vulnerabilities and preventable misconfigurations. It is important to understand that good security hygiene will greatly reduce the effectiveness of an attack and goes a long way to making the attackers job more difficult.”
For more information on how implementing security controls can reduce the risk from common digital attack types, click here. You can also learn how Tripwire's solutions can help your organization achieve compliance with the European Union's General Data Protection Regulation (GDPR), a standard which is set to take full effect on May 25, 2018.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

