What is the Interlock ransomware?
Interlock is a relatively new strain of ransomware, that first emerged in late 2024. Unlike many other ransomware families it not only targets Windows PCs, but also systems running FreeBSD.
If you are impacted, you will find that your files have not only been encrypted but have also had ".interlock" appended to their filenames. For example, a file named report.xlsx would become report.xlsx.interlock, visibly signaling that it has been encrypted by Interlock.
And let me guess - it asks you to pay up for the decryption?
How did you know? Yes, as is so normal with cyber attacks these days, the malicious hackers will leave an extortion note on your system - telling you that you will need to pay a ransom for the decryption key that will unlock the encrypted files, and also to prevent the files from being published on the dark web.
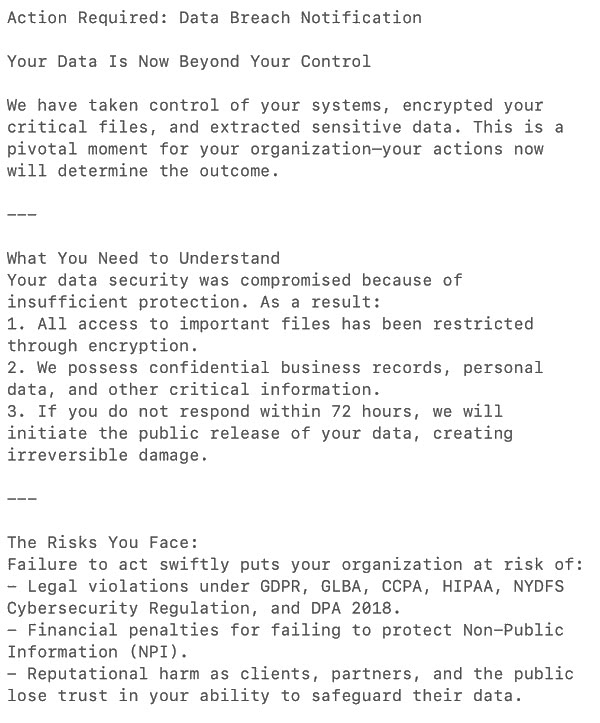
Do I need to take the threat seriously?
You would be sensible to treat any ransomware threat seriously. Interlock's leak site on the dark web has made available terabytes of data stolen from scores of organisations.
How do companies get hit by Interlock in the first place?
Interlock has been seen distributed via fake updates for browsers such as Google Chrome and Microsoft Edge, made available for download from compromised legitimate websites.
The fake installers for these updates run a PowerShell backdoor, and ultimately leads to the delivery of the ransomware.
What makes Interlock different?
Aside from the ability to also attack FreeBSD systems, Interlock has also been observed using the ClickFix social engineering technique.
ClickFix? What's that?
It is a social engineering tactic used by malicious hackers to trick users into copy-and-pasting malicious commands into their computers. The end result is often the installation of malware, remote access being granted to cybercriminals, or full system compromise.
For instance, a fake error webpage of CAPTCHA dialog may tell you to press a particular key sequence to verify yourself or "fix" a problem. Following the instructions actually sends a malicious command from your clipboard to the computer, which will end up with malicious code being run on your PC.
In October last year, the US Government warned internet users to be vigilant of the ClickFix threat, giving the example of websites that impersonated Google, Facebook, reCAPTCHA, and others.
Every day thousands of people are falling for ClickFix scams, and helping their computers become infected as a result.
Nasty. How do ransomware gangs like Interlock justify their activities?
In Interlock's case, they argue that they are trying to improve cybersecurity.

We don’t just want payment; we want accountability. Our actions send a message to those who hide behind weak defenses and half-measures: your data is only as safe as the effort you put into protecting it. If you don’t take data security seriously, we will on your behalf. Pay attention or pay the price. In this digital age, there's no excuse for complacency. When companies neglect cybersecurity, we make them pay not just with ransoms, but with lessons they won’t forget. We are here to enforce the standards they fail to uphold.
Does that justify what they do?
No, of course not. Notably hospitals and healthcare organisations have been amongst the ransomware's targets, which seems particularly callous.
So how can my company protect itself from Interlock?
The best advice is to follow the same recommendations on how to protect your organisation from any other type of ransomware. These include:
- making secure offsite backups.
- running up-to-date security solutions and ensuring that your computers are protected with the latest security patches against vulnerabilities.
- using hard-to-crack unique passwords to protect sensitive data and accounts, as well as enabling multi-factor authentication.
- encrypting sensitive data wherever possible.
- reducing the attack surface by disabling functionality that your company does not need.
- educating and informing staff about the risks and methods used by cybercriminals to launch attacks and steal data.
Stay safe folks.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.
Beating the Business of Ransomware
Learn how to beat cybercriminals’ ransomware business.

